[Walker] has a very interesting new project: a completely different take on a self-destructing USB drive. Instead of relying on encryption or other “visible” security features, this device looks and works like an utterly normal USB drive. The only difference is this: if an unauthorized person plugs it in, there’s no data. What separates authorized access from unauthorized? Wet fingers.
It sounds weird, but let’s walk through the thinking behind the concept. First, encryption is of course the technologically sound and correct solution to data security. But in some environments, the mere presence of encryption technology can be considered incriminating. In such environments, it is better for the drive to appear completely normal.
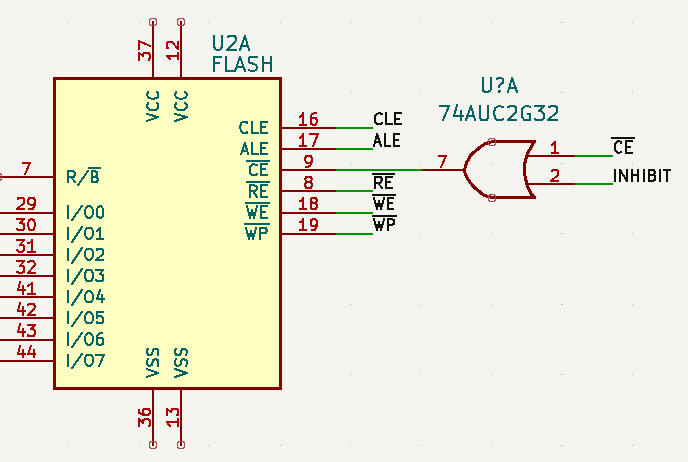
The second part is the access control; the “wet fingers” part. [Walker] plans to have hidden electrodes surreptitiously measure the resistance of a user’s finger when it’s being plugged in. He says a dry finger should be around 1.5 MΩ, but wet fingers are more like 500 kΩ.
But why detect a wet finger as part of access control? Well, what’s something no normal person would do right before plugging in a USB drive? Lick their finger. And what’s something a microcontroller should be able to detect easily without a lot of extra parts? A freshly-licked finger.
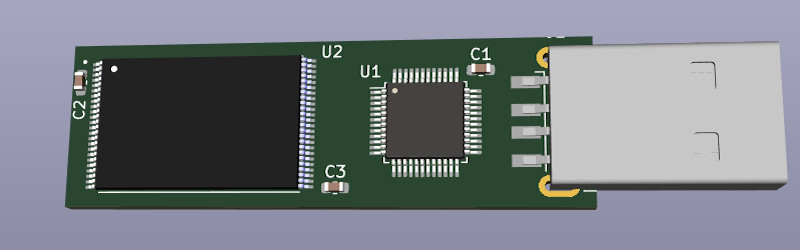
Of course, detecting wet skin is only half the equation. You still need to implement a USB Mass Storage device, and that’s where things get particularly interesting. Even if you aren’t into the covert aspect of this device, the research [Walker] has done into USB storage controllers and flash chips, combined with the KiCad footprints he’s already put together means this open source project will be a great example for anyone looking to roll their own USB flash drives.
Regular readers may recall that [Walker] was previously working on a very impressive Linux “wall wart” intended for penetration testers, but the chip shortage has put that ambitious project on hold for the time being. As this build looks to utilize less exotic components, hopefully it can avoid a similar fate.















Ewwwwww!
Gross, but clever. I mean, probably not useful in situations of actual peril, but a fun trick.
Next up, a USB drive that’s based on volatile ram.
A rechargeable coin cell keeps the contents whilst it’s not plugged in. Removing the cover disconnects the power.
I mean, Battery Backed RAM has been a Save Media for a long time. N64 savepaks used it, but implementing it in a Security-minded way would be an interesting project
It was used in a few arcade cabinets to store a decryption key for the ROM so if the chip was removed it would be lost and the ROM would be useless. This meant if the battery for it ran out the system was bricked.
Battery backed ram (usually containing security keys) is actually a very common method when you want something to be highly tamper resistant. Very common in anything that handles money electronically, like credit card terminals or ATMs. Often with a thin conductor wrapped around the inside on the enclosure that will dump the data if broken, like in the case of being opened.
Interesting concept. I’d love to see an ultra version that has a capacitor and voltage booster built-in so that the first time it’s plugged in without the wet fingers trick, it sends a relatively high voltage and large current pulse to the nand chip to destroy it!
Cool trick, and I like it too, but I think it would remove any ability to plausibly deny that you had something secret in the drive. If your threat model involved government actors then it would not help your deniability. I even think the pads to detect wet fingers would give it away upon closer inspection.
I had once thought of using a ceramic MLCC on a circuit board as a force sensor to make a secret button. I think that could work here really well. The user would squeeze the plastic case of the USB stick, applying a force to the MLCC and this can be sensed by the microcontroller to unhide the data. A teardown and close inspection of the device would reveal nothing.
Wouldn’t it be better to partition the memory space into TWO drives? Then a licked finger gets you one section and an unlicked finger gets you the other one? That way it survives more careful examination.
I had this exact same thought. And to further drive the deception home, pick a drive come in two or more capacities. Use a laser etcher to remove the flash chip’s top layer of plaster including the part number and re etch a lower capacity part chip (ideally one with half the capacity). Then if they do tear it down the changed part number will hopefully convince them the partition they can access is all there is based on the part number.
The wet fingers thing is clever but imperfect. I would propose using the access indicator led as a poor man’s photodiode/solar panel. Have the drive read the voltage across the led when it’s plugged in for just a moment before lighting it up and if any light is detected it shows the public partition. In order to get to load the secret partition you have to plug it in in complete darkness. No one would suspect the led to be used in such a way.
How about a capacitive input disguised as a decorative part of the case? You tap out a knock code or a bit of Morse and it switches to the real data.
sounds like VeraCryped
Is this wise with COVID-19 still floating around?
Ideally you wouldn’t be sharing this particular drive.
Unless they read this article. Publishing it makes the idea useless
Not really – even if you suspect such a thing actually proving which one of the many such concepts it is can be excessively time consuming, and if it has a self destruct system even more so.
When something just looks like x brand USB stick, behaves like the usb stick should, and was found in a place USB sticks are normally found then odds are its just a usb stick.
Trying to test every possible fun trick like this will take not only a great deal of an electronics expert time but also lots of money – as they have to be enough of an expert to notice this chip has 2 extra pins, a larger footprint, or the traces don’t quite match the legitimate PCB’s purchased and to prove its not bogus you would need to buy a great deal of ‘real’ ones – as product evolution, substitutions, regional variations and the better knock offs COULD be this USB stick.
It only becomes useless if ‘THEY’ are seriously looking at me funny for some reason so would look at every article i’ve ever written/comment on, rummage through my project draws etc or I am stupendously famous and then publish such a thing, showing off this exact fake USB stick and then go and have exactly one of these USB sticks in my possession that does this trick exactly as I demonstrated. Otherwise good luck finding this exact article or the project log that ties the normal USB stick to me and this method.
VeraCrypt’s hidden volumes would be safer, except you couldn’t claim not using any encryption in the first place.
could you hide data stored in cells flagged as dead? the drive proper would contain dummy data that would pass any scrutiny. they could image the drive if they wanted to, they would just get a partition full of things like kitten videos, linux isos, and bad poetry. if you create a file with a specific name, the controller would see that and write the dead cell data to the file. a different file name triggers a write command, storing the contents of the file in “dead” cells and then deleting it. the file could be a zip or a file system image.
Could have two flash chips and based on wet fingers at boot or not you could show one or the other. That way it’s not suspicious that the drive doesn’t work.
Old, worn-out USB drives malfunction all the time. I have a box with a dozen of drives that work one day and refuse the next. Just scrape it on the walls a little, smudge the case and it can be a convincing old USB drive.
Bonus points if the capacity is 4GB or less. A 256MB drive would be ideal.
Ummmm we are hackers…. Can’t see people giving up that easy, can still read the chip protection or not
Very interesting idea, are skin resistances all that reliable though, skin is a very dynamic thing. Instead how about implementing this idea by plugging and unplugging the device into the computer with specific timings, a supercap allows the uC to keep track, but as the supercap drains and charges could be used as the main metric with an ADC.
Skin resistances are not reliable. Besides natural variation between users, here are four things that could be found at any office desk which might provide unintended device access: a salty snack, condensation on a cold beverage container, moisturizing lotion, and a user with naturally sweaty hands.
While hiding data by the conductivity of your finger is a neat idea, obfuscation will only get you so far.
A lot more work, but definitely within reach, would be to start with a USB with two partitions. With the first partition mounted with some corporate sales documents. To unlock the second partition, you would need undocumented USB commands. Better yet if the memory is properly encrypted, with the passphrase as a key.
Wouldn’t any sufficiently capable agency just access the memory chip directly? An X-ray would show if there were any booby traps to destroy data upon opening the device and if not then this wouldn’t work well. Apart from a custom memory chip, it would be difficult to prevent direct access to the chip without some kind of physical intrusion detection mechanism.
If you are under the microscope enough for that to be an issue I don’t think it much matters what you do, eventually they will manage to get hold of one of your boobytrapped, encrypted, tricky in every way possible data hordes and manage to get the data out. You can’t spend the hours of skilled time and fancy inspection tools on every USB drive that may cross your path no matter how ‘capable’ your agency – the workload would be far too vast, and so soul destroying probably going to miss some of the bad ones though human error too, as when 99.99999999% of the time that thing that looks and acts like a USB key with nothing incriminating/important on it is proved to be just as USB key after a mornings work…
It sounds like you’re contradicting yourself?
A) If an agency wants your info, they’ll get it no matter what.
B) It’s too much work to go through every normal-looking USB drive.
I don’t mean to be rude, but I can’t tell if you’re pro or con.