Dan Maloney and I were talking about the chess robot arm that broke a child’s finger during the podcast, and it turns out that we both have extreme respect for robot arms in particular. Dan had a story of a broken encoder wheel that lead to out-of-control behavior that almost hit him, and I won’t even get within striking distance of the things unless I know they’re powered off after seeing what programming errors in a perfectly functioning machine can do to two-by-fours.
This made me think of all the dangerous things I’ve done, but moreover about all the intensely simple precautions you can to render them non-risky, and I think that’s extremely important to talk about. Tops of my list are the aforementioned industrial robot arm and high powered lasers.
Staying safe with an industrial robot arm is as easy as staying out of reach when it’s powered. Our procedure was to draw a line on the floor that traced the arm’s maximum radius, and you stay always outside that line when the light is on. It’s not foolproof, because you could hand the ’bot a golf club or something, but it’s a good minimum precaution. And when you need to get within the line, which you do, you power the thing down. There’s a good reason that many industrial robots live in cages with interlocks on the doors.
Laser safety is similar. You need to know where the beam is going, make sure it’s adequately terminated, and never take one in the eye. This can be as simple as putting the device in a box: laser stays in box, nobody goes blind. If you need to see inside, a webcam is marvelous. But sometimes you need to focus or align the laser, and then you put on the laser safety glasses and think really hard about where the beam is going. And then you close the box again when you’re done.
None of these safety measures are particularly challenging to implement, or conceptually hard: draw a line on the floor, put it in a box. There were a recent series of videos on making Lichtenberg figures safely, and as a general rule with high voltage projects, a great precaution is a two-button deadman’s switch box. This at least ensures that both of your hands are nowhere near the high voltage when it goes on, at the cost of two switches.
If all of the safety precautions are simple once you’ve heard them, they were nothing I would have come up with myself. I learned them all from other hackers. Same goes with the table saw in my workshop, or driving a car even. But since the more hackery endeavors are less common, the “common-sense” safety precautions in oddball fields are simply less commonly known. It’s our jobs as the folks who do know the secrets of safety to share them with others. When you do something dangerous, show off your safety hacks!
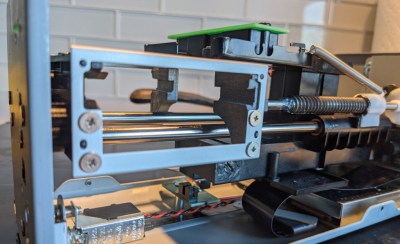 On the software side, [Christian] modified a driver for the Plustek 8100 so that it sweeps the scan head further than usual. At the application level, to scan medium format frames, it does a total of four scans: one for each quadrant. The results get stitched together in software with a thoughtfully-designed shell script that provides previews and handles failures and restarts gracefully.
On the software side, [Christian] modified a driver for the Plustek 8100 so that it sweeps the scan head further than usual. At the application level, to scan medium format frames, it does a total of four scans: one for each quadrant. The results get stitched together in software with a thoughtfully-designed shell script that provides previews and handles failures and restarts gracefully.