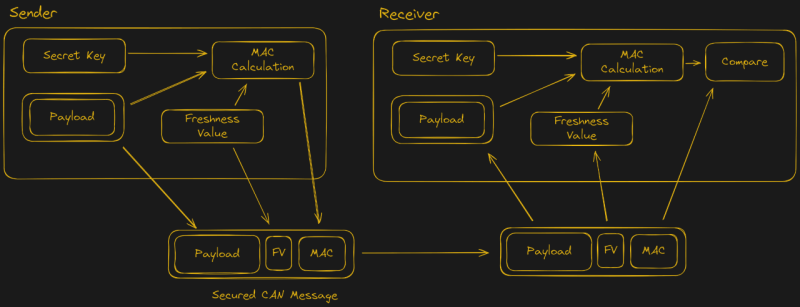
With the recently introduced SecOC (Secure Onboard Communication) standard, car manufacturers seek to make the CAN bus networks that form the backbone of modern day cars more secure. This standard adds a MAC (message authentication code) to the CAN messages, which can be used to validate that these messages come from a genuine part of the car, and not from a car thief or some third-party peripheral.
To check that it isn’t possible to circumvent SecOC, [Willem Melching] and [Greg Hogan] got their hands on the power steering (EPS) unit of a Toyota RAV4 Prime, as one of the first cars to implement this new security standard.
As noted by [Willem], the ultimate goal is to be able to run the open source driver assistance system openpilot on these SecOC-enabled cars, which would require either breaking SecOC, or following the official method of ‘rekeying’ the SecOC gateway.
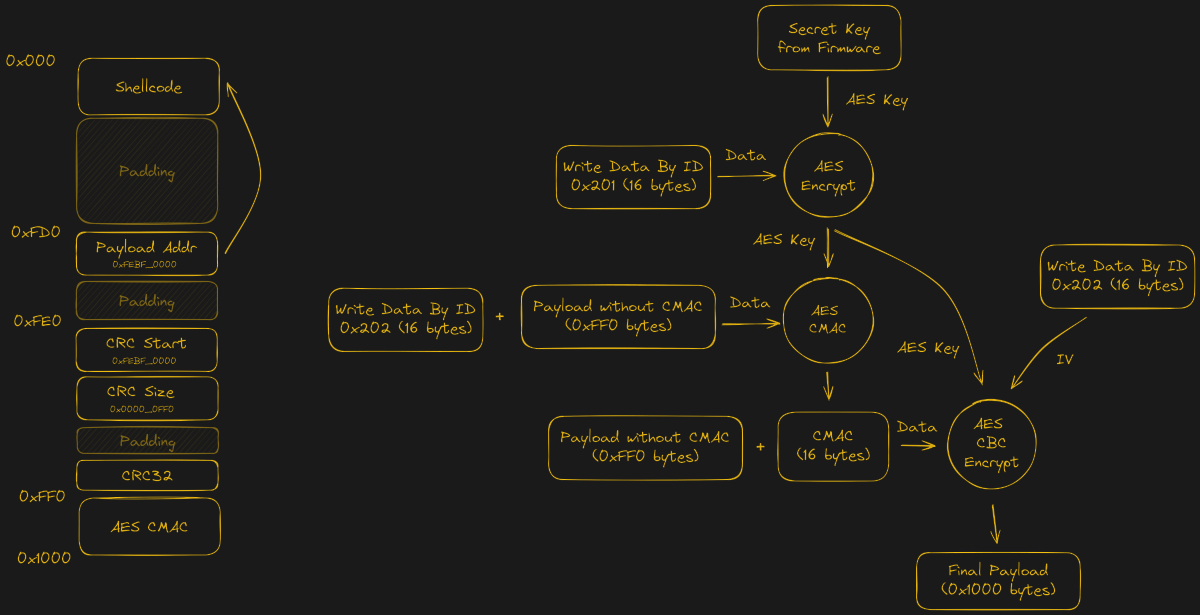
After dumping the firmware of the EPS Renesas RH850/P1M-E MCU via a voltage fault injection, the AES-based encryption routines were identified, but no easy exploits found in the main application. This left the bootloader as the next target.
Ultimately they managed to reverse-engineer the bootloader to determine how the update procedure works, which enabled them to upload shellcode. This script then enabled them to extract the SecOC keys from RAM and send these over the CAN bus. With these keys the path is thus opened to allow any device to generate CAN messages with valid SecOC MACs, effectively breaking encryption. Naturally, there are many caveats with this discovery.
As noted in the blog post, the specific MCU targeted did the crypto routines in software rather than using a more secure hardware module, while also omitting to validate the payload sent to the bootloader. That said, it might be that this approach works even with much newer SecOC implementations. Some experimentation on a 2023 Corolla Cross demonstrated that its power steering unit could also be coaxed into allowing code execution via the bootloader, but further attempts at defeating SecOC on it haven’t been made yet.
A GitHub repository containing the the software tools to extract keys and such has been made available.
While SecOC promises to make the future of CAN hacking more difficult, there are still millions of vehicles on the road that are all too happy to let you poke around in their data networks — allowing you to do everything from pulling EV battery info to adding a backup camera so long as you have the proper tools.
















Giving vehicle owners the capacity to update and change features on their vehicle electronic control systems should be a *right* for folks who own their vehicles and are not leasing them.
We’ve seen how unscrupulous companies like John Deere hold their customers hostage with such proprietary controls.
Hats off to the hacker communities, giving us freedom to control and manage our own systems.
Sounds like a good way for manufacturers to lock out third-party parts and jack up prices.
Yeah, that is what I was thinking too.
I understand the case for securing the CAN bus, which will (in theory) prevent criminals from popping out a headlight to get access to CAN, connect a device that can inject some commands to unlock/start vehicle, and steal it.
The side effect of this basically creates parts pairing. I assume the EPS board they used for the research was integrated with the electric pump and/or steering column/rack. Those are mechanical parts that will wear out and fail eventually. Pre-SecOC, there are various options to repair – new OEM part, new aftermarket part, or used (junkyard) part, plus the labor to physically swap it.
Looking around some auto parts suppliers, the older (less integrated) pumps, both mechanical and electric are $100-200, and available from a variety of OEM and aftermarket manufacturers. In other words, a failed pump is likely to be $500 or less from just about repair shop.
Looking at some similar Toyota models from 4-5 years ago, the highly-integrated EPS has MSRP of $1260, street price of $850, and aftermarket/reman for $600-750. That obviously hurts the wallet more, but still a situation where an independent shop could get you back on the road for ~$1000.
If the vehicle has SecOC, now you are going to need the official Toyota diagnostic software suite to pair the new EPS. I would bet that will be a $2000 dealer repair. This will definitely have a negative impact on Independent repair shops and aftermarket parts, not to mention all of those who would DIY repair.
The future sucks, we really need more right-to-repair protections.
Just bring back the physical keys, easy enough
But… the keys are specific to that car, right? Not any Toyota…? Please tell me they are…?
Would a company like Toyota use the same key on all models, just to save a few hundred million dollars in parts management?
Better question:
Would a company like Bosch use the same key in all brands, just to save a few billion dollars in parts management?
Jatco? They would never, ever ship known garbage. (I know Jatco CVT owners, not funny.)
Cars shouldn’t be secure! Ensure physical security and bye.
We don’t want to bin entire cars because app fails to update onboard TLS cert.
Bring back dumb cars!