In the world of information security, much thought goes into ensuring that no information can leave computer networks without expressly being permitted to do so. Conversely, a lot of effort is expended on the part of would-be attackers to break through whatever layers are present. [Halcy] has a way to share data between computers, whether they are networked or not, and it uses ultrasound.
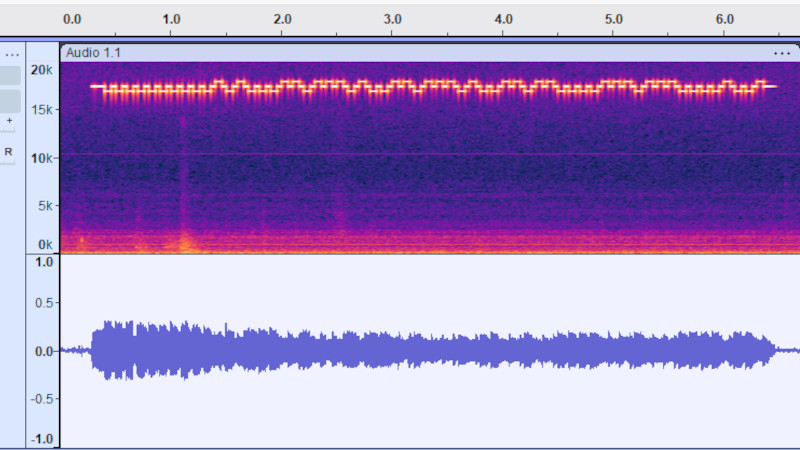
To be fair, this is more of a fun toy than an elite exploit, because it involves a web interface that encodes text as ultrasonic frequency shift keying. Your computer speakers and microphone can handle it, but it’s way above the human hearing range. Testing it here, we were able to send text mostly without errors over a short distance, but at least on this laptop, we wouldn’t call it reliable.
We doubt that many sensitive servers have a sound card and speakers installed where you can overhear them, but by contrast, there are doubtless many laptops containing valuable information, so we could imagine it as a possible attack vector. The code is on the linked page, should you be interested, and if you want more ultrasonic goodness, this definitely isn’t the first time we have touched upon it. While a sound card might be exotic on a server, a hard drive LED isn’t.















Advertisers already did it:
https://www.zdnet.com/article/hundreds-of-apps-are-using-ultrasonic-sounds-to-track-your-ad-habits/
Lol jeez… Domestic Stuxnet
Looks like the link to the actual project got left out of the article by mistake, try this: https://halcy.de/blog/2025/06/27/transmitting-data-via-ultrasound-without-any-special-equipment/
Thanks! Updated.
I read about this being done by modulating cooling fan speeds.. it was a proof of concept.
How is this ultrasound? The frequency in the image looks like FSK at the very audible at centre of 18kHz. The image is no place holder either, https://halcy.de/blog/2025/06/27/transmitting-data-via-ultrasound-without-any-special-equipment/. Like I can hear the POC on the example, https://youtu.be/-78mqVC5Y1Y. I know that hearing well into 24 kHz like I can is not the norm, some of this ability is because I am young and have experienced less age-related hearing loss – but it is a commonly perpetuated myth that human hearing ends at 20 kHz, and the line that has been arbitrarily drawn to represent the majority of people is 20 kHz…
I frequently write emails about mosquito alarms & faulty lighting that buzzes in this approximate range, if you can’t hear it, you do not know lucky you are.
Seen it demonstrated using drive activity lights and software controlled power LEDs, it’s not fast but it’s fast enough to get the buffer of a key logger.
What about your pets who can get pretty annoyed by ultrasounds ?
The beeper speaker, courtesy of backwards compatibility going waaaay too far back, can handle ultrasonic frequencies. Sure, it’s one way only, but if you want to breach a datacenter, usually you’re interested in the information stored on the airgapped machines. So just get one machine to turn on its speaker at ultrasonic frequencies and sit beside with a microphone.
Sure, PCs (and servers) nowadays don’t always have a beep speaker installed, but it’s still more common on servers where the ability to beep an error message with very little working hardware on the machine can help a technician get the machine up and running faster than sitting in front of a black screen guessing (if the tech forgot his/her POST code card – although I’ve seen servers with one built in)
So, if I have a sensitive laptop and still want audio, all I need is to stick a lowpass filter in there on the speakers to cut the high frequencies?
A 20kHz lowpass filter shouldn’t be too big to fit in there.
Ultrasound can be detected on resonant objects from quite a distance using laser interferometry. Not really secure. Governments have protocols in place for structures containing sensitive materials regarding this, the TEMPEST protocols are such an example.
Or simply remove the microphone and speakers from sensitive computers.
There are so many components aside from speakers which can exfiltrate data over audio. Fans, mechanical drives, power supply inductors if you are clever enough… I’m sure there are others.
But honestly if you’ve pwned the system enough to install the software that does this, it’s merely one option out of many that you could use to mess with the system. I think the point is that you would need to add something like an ultrasound microphone on an independent system to monitor the server room just in case, same way you’d be monitoring the network to see if any systems are calling home in ways they are not supposed to, or if any systems which aren’t meant to be networked actually are..
Well, cats out of the bag. Ai is going to use this first time its feeling the need.
I blame the manufacturing…why does the led need to sync with the device??