If you own an Intel motherboard with a Z170 or Z270 chipset, you might believe that it only supports CPUs up to Intel’s 7th generation, known as Kaby Lake. Even the CPU socket’s pinout is different in the next generation — we are told, it will fit the same socket, but it won’t boot. So if you want a newer CPU, you’ll have to buy a new motherboard while you’re at it. Or do you?
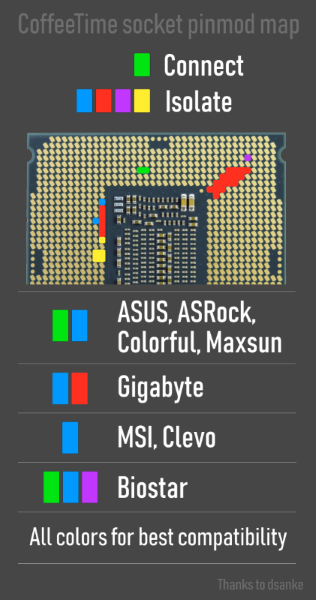 Turns out, the difference in the socket is just a few pins here and there, and you can make a 8th or 9th generation Coffee Lake CPU work on your Z170/270 board if you apply a few Kapton tape fixes and mod your BIOS, in a process you can find as “Coffee Mod”. You can even preserve compatibility with the 6th/7th generation CPUs after doing this mod, should you ever need to go back to an older chip. Contrasting this to AMD’s high degree of CPU support on even old Ryzen motherboards, it’s as if Intel introduced this incompatibility intentionally.
Turns out, the difference in the socket is just a few pins here and there, and you can make a 8th or 9th generation Coffee Lake CPU work on your Z170/270 board if you apply a few Kapton tape fixes and mod your BIOS, in a process you can find as “Coffee Mod”. You can even preserve compatibility with the 6th/7th generation CPUs after doing this mod, should you ever need to go back to an older chip. Contrasting this to AMD’s high degree of CPU support on even old Ryzen motherboards, it’s as if Intel introduced this incompatibility intentionally.
There’s been a number of posts on various PC forums and YouTube videos, going through the process and showing off the tools used to modify the BIOS. Some mods are exceptionally easy to apply. For example, if you have the Asus Maximus VIII Ranger motherboard, a single jumper wire between two pads next to the EC will enable support without Kapton tape, a mod that likely could be figured out for other similar motherboards as well. There’s a few aspects to keep in mind, like making sure your board’s VRMs are good enough for the new chip, and a little more patching might be needed for hyper-threading, but nothing too involved.
Between money-grab features like this that hamper even the simplest of upgrades and increase e-waste, fun vulnerabilities, and inability to sort out problems like stability power consumption issues, it’s reassuring to see users take back control over their platforms wherever possible, and brings us back to the days of modding Xeon CPUs to fit into 775 sockets.
Don’t get too excited though, as projects like Intel BootGuard are bound to hamper mods like this on newer generations by introducing digital signing for BIOS images, flying under the banner of user security yet again. Alas, it appears way more likely that Intel’s financial security is the culprit.
Continue reading “Intel’s Anti-Upgrade Tricks Defeated With Kapton Tape”












