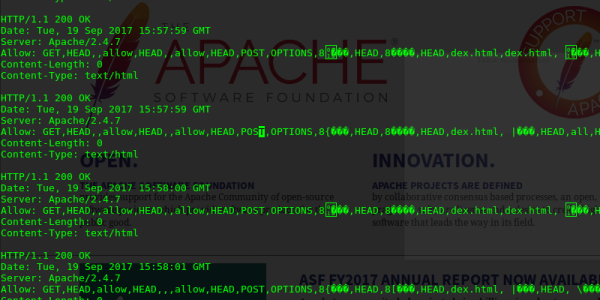
[Hanno Böck] recently uncovered a vulnerability in Apache webserver, affecting Apache HTTP Server 2.2.x through 2.2.34 and 2.4.x through 2.4.27. This bug only affects Apache servers with a certain configuration in .htaccess file. Dubbed Optionsbleed, this vulnerability is a use after free error in Apache HTTP that causes a corrupted Allow header to be replied by the webserver in response to HTTP OPTIONS requests. This can leak pieces of arbitrary memory from the server process that may contain sensitive information. The memory pieces change after multiple requests, so for a vulnerable host an arbitrary number of memory chunks can be leaked.
Unlike the famous Heartbleed bug in the past, Optionsbleed leaks only small chunks of memory and more importantly only affects a small number of hosts by default. Nevertheless, shared hosting environments that allow for .htaccess file changes can be quite sensitive to it, as a rogue .htaccess file from one user can potentially bleed info for the whole server. Scanning the Alexa Top 1 Million revealed 466 hosts with corrupted Allow headers, so it seems the impact is not huge so far.
The bug appears if a webmaster tries to use the “Limit” directive with an invalid HTTP method. We decided to test this behaviour with a simple .htaccess file like this:
Continue reading “OptionsBleed – Apache Bleeds In Uncommon Configuration”