[Robert] has been snooping around Naenara in order to learn more about how North Korea’s intranet might work. Naenara is the web browser that comes bundled with North Korea’s official Linux-based operating system known as Red Star OS. [Robert] once saw a screenshot of the browser and found it interesting that the browser seemed to automatically load a non-routable IP address immediately upon start-up. This made him curious about what other oddities one might uncover from the software.
Upon start-up, the browser tries to load a page located at IP address 10.76.1.11, which is a reserved IP address for private use. This indicated that North Korea’s “Internet” is actually more of in intranet. [Robert] suspects that the entire country may be running in private address space, similar to how your home or business likely runs.
[Robert’s] next thoughts were that the browser looks like a very old version of Mozilla Firefox, but with some default configuration changes. For one, all crashes are automatically transmitted to “the mothership”, as [Robert] calls it. He suspects this is to fix not only bugs, but also to find and repair any security vulnerabilities that may allow users more control.
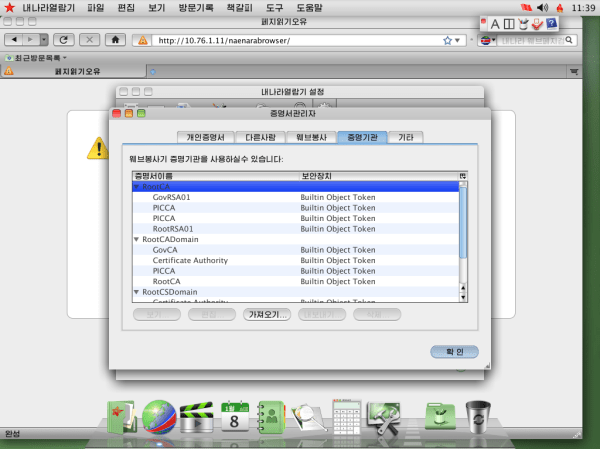
There are some other interesting changes as well, such as the supported security certificates. The Naenara browser only accepts certificates issued by the DPRK, which would make it very easy for them to snoop on encrypted HTTPS traffic. there is also evidence suggesting that all traffic for the entire country is routed through a single government controlled proxy server.
None of these findings are all that surprising, but it’s still interesting to see what kind of information can be gleamed from poking around the browser and operating system. [Robert] has found more than just these few findings. You can check out the rest of his findings on his blog.
[via Reddit]