Earlier this week, another nation joined the still relatively exclusive club of those which possess a satellite launch capability. North Korea launched their Malligyong-1 spy satellite, and though it has naturally inflamed the complex web of political and military tensions surrounding the Korean peninsula, it still represents something of a technical achievement for the isolated Communist state. The official North Korean news coverage gleefully reported with much Cold War style rhetoric, that Kim Jong-Un had visited the launch control centre the next day and viewed intelligence photographs of an American base in Guam. Could the satellite have delivered in such a short time? [SatTrackCam Leiden] has an interesting analysis. Continue reading “Could North Korea’s New Satellite Have Spied On Guam So Easily?”
North Korea9 Articles
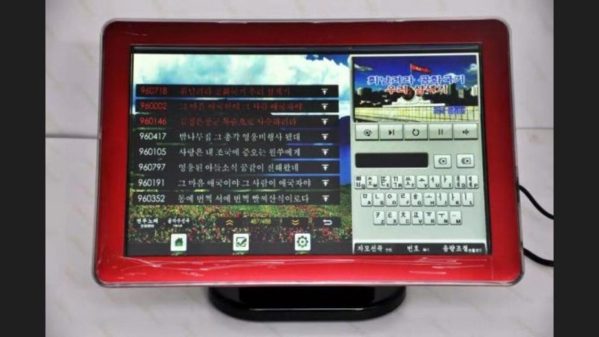
North Korean Karaoke Machine Teardown
Karaoke is a very popular pastime in Seoul — there are venues where you can sing on a stage, sing in rooms with your friends, and even sing solo in coin-operated karaoke booths on the bullet train. Apparently it is also popular in North Korea as well — [Martyn Williams] of the North Korea Tech blog reported on an interesting teardown by web hacker [Will Scott]. It is the Tianchi v700 machine, a Chinese product tailored for North Korean users, obtained online back in 2020.
Unlike the karaoke machines encountered by this author in South Korea, the v700 form factor is a 19.5-inch Android tablet with touch-screen and all the necessary interfaces you’d expect: external video, speakers, and microphone, as well as WiFi and Ethernet for content upgrade and online payment systems. Not surprisingly, the connectivity aspects of the machine are not used in the North Korean model, but with a large catalog of pre-loaded music, it’s perfectly usable as a stand-alone device.
[Will] dug into the innards of the machine and discovered it was powered by an Allwinner ARM processor (seemingly the H6 V200, a quad-core ARM Cortex-A53). He also found it uses a swappable external disk to hold the songs, but all the files were encrypted. You can read more details in the blog post linked above, but eventually he was successful in decoding the disk and accessing the material.
The V700 consults both “/proc/cpuinfo” to learn the CPU serial number of the device it is on, and a binary file associated with the device file system structure as part of its method for determining its AES (Advanced Encryption Standard) key. It then ignores all of these device-specific items, and reverts back to a static key “87654321” stored in the binary.
All the songs on the disk were posted up on the Internet Archive. Check them out if you’re curious what North Korean karaoke songs sound and look like. One video that caught our attention was about CNC machines (see the video linked below the break). [Martyn] has been covering technology issues related to North Korea since 2011. In 2016, he learned after the fact that his website had been banned by the South Korean authorities. Believing this was in error, he appealed the ban and eventually prevailed in the courts. We wrote about some of [Will]’s research on consumer computing technology back in 2017 if you’re interested in learning more.
This Week In Security: Zimbra, Lockbit 2, And Hacking NK
Unknown attackers have been exploiting a 0-day attack against the Zimbra e-mail suite. Researchers at Volexity first discovered the attack back in December of last year, detected by their monitoring infrastructure. It’s a cross-site scripting (XSS) exploit, such that when opening a malicious link, the JavaScript running on the malicious page can access a logged-in Zimbra instance. The attack campaign uses this exploit to grab emails and attachments and upload them to the attackers. Researchers haven’t been able to positively identify what group is behind the attacks, but a bit of circumstantial evidence points to a Chinese group. That evidence? Time zones. The attacker requests all use the Asia/Hong_Kong time zone, and the timing of all the phishing emails sent lines up nicely with a work-day in that time zone.
Zimbra has responded, confirming the vulnerability and publishing a hotfix for it. The campaign seems to have been targeted specifically against European governments, and various media outlets. If you’re running a Zimbra instance, make sure you’re running at least 8.8.15.1643980846.p30-1.
LockBit 2.0
Because security professionals needed something else to keep us occupied, the LockBit ransomware campaign is back for a round two. This is another ransomware campaign run in the as-a-Service pattern — RAAS. LockBit 2 has caught enough attention, that the FBI has published a FLASH message (PDF) about it. That’s the FBI Liaison Alert System, in the running for the worst acronym. (Help them figure out what the “H” stands for in the comments below!)
Like many other ransomware campaigns, LockBit has a list of language codes that trigger a bail on execution — the Eastern European languages you would expect. Ransomware operators have long tried not to poison their own wells by hitting targets in their own back yards. This one is being reported as also having a Linux module, but it appears that is limited to VMWare ESXi virtual machines. A series of IoCs have been published, and the FBI are requesting any logs, ransom notes, or other evidence possibly related to this campaign to be sent to them if possible. Continue reading “This Week In Security: Zimbra, Lockbit 2, And Hacking NK”
Hackaday Links: December 2, 2018
CircuitPython is becoming a thing! CircuitPython was originally developed from MicroPython and ported to various ARM boards by Adafruit. Now, SparkFun is shipping their own CircuitPython board based on the nRF52840, giving this board an ARM Cortex-M4 and a Bluetooth radio.
You like contests, right? You like circuit boards too, right? Hackster.io now has a BadgeLove contest going on to create the Blinkiest Badge on Earth. Yes, this is a #badgelife contest, with the goal of demonstrating how much you can do in a single circuit badge. Prizes include a trip to San Francisco, a badass drone, a skateboard, a t-shirt, or socks. YES, THERE ARE SOCKS.
We have a date for the Vintage Computer Festival Pacific Northwest 2019. It’s going down March 23 and 24 at the Living Computers Museum in Seattle. The call for exhibitors is now open so head over and check it out. So far the tentative list of exhibits and presenters include Attack of the SPARC Clones, and I must mention that SPARC systems are showing up on eBay with much higher frequency lately. I have no idea why.
Need another con? How about a KiCAD con? The inaugural conference for KiCAD users is happening next April in Chicago and the call for talk proposals just opened up. The con focuses on topics like using KiCAD in a manufacturing setting, what’s going on ‘under the hood’ of KiCAD, and how to use KiCAD to make an advanced product.
Spanish police have stopped a homemade scooter. Someone, apparently, was tearing around a public road in Galacia on a homemade scooter. From the single picture, we’re going to say ‘not bad.’ It’s a gas-powered weed wacker mounted to a homemade frame.
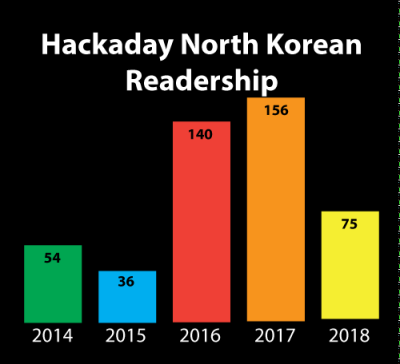 Every year, in December, we take a look back at what Hackaday has accomplished in the past twelve months. Sure, we gave out hundreds of thousands of dollars in awards in the Hackaday Prize, and yes, we’ve pushed our coverage of tech advancements into weird, uncharted, but awesome territory. Our biggest accomplishment, though, is always how many readers we reach. This year, we had a slight fall-off in our readership in the Democratic People’s Republic of North Korea. We’re down from 156 views in 2017 to 75 views this year. While the year isn’t over, we don’t expect that number to change much. What was the cause of this drop-off? We’re not quite sure. Only time will tell, and we’re looking forward to serving fresh hacks every day to the DPRK in 2019.
Every year, in December, we take a look back at what Hackaday has accomplished in the past twelve months. Sure, we gave out hundreds of thousands of dollars in awards in the Hackaday Prize, and yes, we’ve pushed our coverage of tech advancements into weird, uncharted, but awesome territory. Our biggest accomplishment, though, is always how many readers we reach. This year, we had a slight fall-off in our readership in the Democratic People’s Republic of North Korea. We’re down from 156 views in 2017 to 75 views this year. While the year isn’t over, we don’t expect that number to change much. What was the cause of this drop-off? We’re not quite sure. Only time will tell, and we’re looking forward to serving fresh hacks every day to the DPRK in 2019.
Hackaday Links: April 29, 2018
Amazon has released the Echo Dot Kids Edition, an always-on, Internet-connected microphone. According to Amazon’s Children’s Privacy Disclosure, the Amazon Echo Dot Kids Edition collects data such as, ‘name, birthdate, contact information (including phone numbers and email addresses), voice, photos, videos, location, and certain activity and device information. The Amazon Echo Dot Kids Edition is able to read audiobooks for bedtime reading and teaches your children to live in a dystopian panopticon of Orwellian proportions. It comes in green, red, and blue.
 Kim Possible! The biggest news headline this week is the coming end of the Korean War. The peninsula has been in a state of war since 1950, but leaders from both countries have agreed to negotiate a treaty to replace the 60-year-old truce. There is also an agreement between the two countries for complete denuclearization. This is great news for Hackaday. Every day, we’re eyeing our North Korean readership. Some days we get a view, some days we don’t, but year over year we’re always getting more views. Will this treaty result in even more Hackaday readers in North Korea? Only time will tell. Here’s some music. It wasn’t a chicken.
Kim Possible! The biggest news headline this week is the coming end of the Korean War. The peninsula has been in a state of war since 1950, but leaders from both countries have agreed to negotiate a treaty to replace the 60-year-old truce. There is also an agreement between the two countries for complete denuclearization. This is great news for Hackaday. Every day, we’re eyeing our North Korean readership. Some days we get a view, some days we don’t, but year over year we’re always getting more views. Will this treaty result in even more Hackaday readers in North Korea? Only time will tell. Here’s some music. It wasn’t a chicken.
The East Coast RepRap Festival is on. Inspired by the Midwest RepRap Festival, the ERRF is happening north of Baltimore on June 23rd and 24th. What’s it going to be like? Nobody knows! This is the first time ERRF is happening, but judging by MRRF standards, it should be awesome. Also, crab season.
One of the most interesting hacks of this year is [Steve Markgraf]’s tool to allow transmit-only SDR through cheap USB 3.0 to VGA adapters. The hack relies on the Fresco Logic FL2000 chip and gives you the ability to transmit FM, TVB-T, and create your own GSM cell site. You can also spoof GPS to get something besides a rattata in Pokemon Go or hack your ankle bracelet to keep your parole officer off your back. The open question, though, is which USB to VGA adapter has the FL2000 chipset. I can confirm this one on Amazon has the relevant chipset. It’s a bit expensive at $15 (the same chipset is available from the usual eBay and AliExpress suppliers for $6), but if you’re looking for something that is available with Prime, there you go. Now we’re looking for shared OSH Park projects with a VGA input on one end and some antennas on the other. Make it happen, people.
Supercapacitors are awesome, but is it possible to fly a drone with a bank of them? Sure, for about 10 seconds. [dronelab] built a 7-cell, 200F supercap and managed to fly a little racing quad for about ten seconds. Not terribly great, but this is going to be awesome when we get multi-thousand Farad superultramegacaps.
Like Open Hardware? The Open Source Hardware Association is opening up the Ada Lovelace Fellowship for women, LGTBA+ and other minorities to attend the Open Hardware Summit. The deadline is tomorrow, so do it soon.
M3D has announced a new 3D printer that can print with four filaments. The Crane Quad is your basic i3 ripoff with an interesting extruder. It looks like it uses four tiny motors to feed filament into the main extruder motor. This isn’t really anything new; the Prusa i3 multimaterial upgrade does the same thing. However, M3D claims they have mastered color mixing. The Prusa upgrade doesn’t do mixing, and this is most likely the reason it works so well. Can M3D pull it off? This is a very, very, very hard problem.
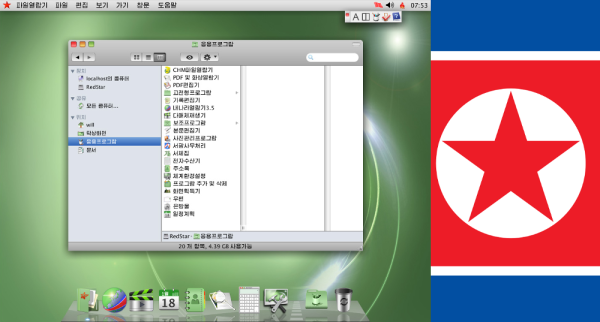
34C3: North Korea’s Consumer Technology
[Will Scott] and [Gabe Edwards] shed some light on the current state of consumer computing technology at 34C3 in their talk DPRK Consumer Technology. The pair has also created a website to act as a clearinghouse for this information — including smartphone OS images up at koreaComputerCenter.org.
Not a whole lot is known about what technology North Korean citizens have available to them. We have seen Red Star OS, the Mac-like Linux based operating system used on PC based desktops. But what about other systems like smartphones?
[Will] and [Gabe] found that cell phones in North Korea are typically manufactured by Chinese companies, running a custom version of the Android Operating system. The phone hardware is common — the phone sold as the Pyongyang 2407 in North Korea is also sold in India as the Genie v5. If you can get your hands on the Genie, you can run the Korean version of the Android OS on that hardware.
Hackaday Links: December 25th, 2016
You should be watching the Doctor Who Christmas special right now. Does anyone know when the Resturant at the End of the Universe spinoff is airing?
We have a contest going on right now. It’s the 1 kB Challenge, a contest that challenges you to do the most with a kilobyte of machine code. The deadline is January 5th, so get cracking.
A few years ago, [Kwabena] created the OpenMV, a Python-powered machine vision module that doesn’t require a separate computer. It’s awesome, and we’re going to have his talk from the Hackaday SuperConference up shortly. Now the OpenMV is getting an upgrade. The upgrades include an ARM Cortex M7, more RAM, more heap for less money. Here’s a link to preorder.
E-paper displays are fancy, cool, and low-power. Putting them in a project, however, is difficult. You need to acquire these display modules, and this has usually been a pain. Now Eink has a web shop where you can peruse and purchase epaper display modules and drivers.
[Kris] built a pair of STM32L4 dev boards that are easily programmed in the Arduino IDE. Now he’s putting these boards up on Kickstarter. The prices are reasonable – $15 for the smaller of the pair, and $25 for the bigger one. Remember, kids: ARM is the future, at least until RISC-V takes over.
This is how you do holiday greeting cards.
Didn’t get what you want for Christmas? Don’t worry, Amazon still has A Million Random Digits with 100,000 Normal Deviates in stock. It’s also available on audible dot com. Sometimes we don’t have time to sit down and read a million random digits but with audible dot com, you can listen to a million random digits in audio book format. That’s audible dot com please give us money.
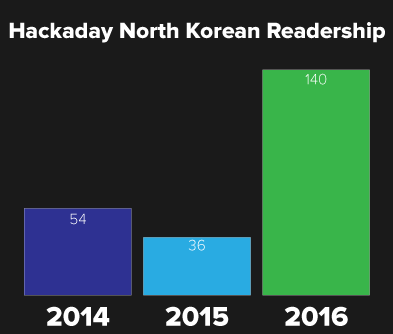 This is the last Hackaday Links post of the year, which means it’s time for one of our most cherished traditions: reviewing our readership in North Korea.
This is the last Hackaday Links post of the year, which means it’s time for one of our most cherished traditions: reviewing our readership in North Korea.
It’s been a banner year for Hackaday in the Democratic People’s Republic of North Korea. The readership has exploded in 2016, with a gain of nearly 300%. To put that in perspective, in 2015 we had thirty-six views from North Korea across every page on Hackaday. In 2016, that number increased to one hundred and forty.
That’s a phenomenal increase and a yearly growth that is unheard of in the publishing industry. We’d like to tip our hat to all our North Korean reader, and we’re looking forward to serving you in 2017.