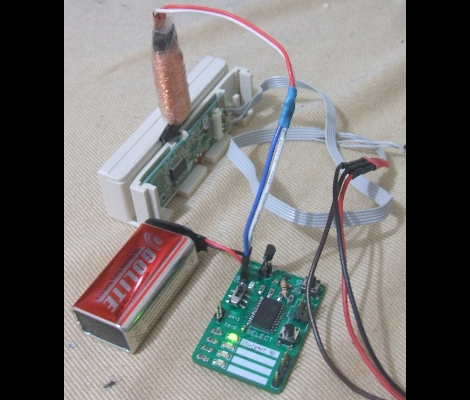
Here’s an open source RFID cloner design that is about the same size as a standard RFID key card. It doesn’t need a battery to capture key codes, just the magnetic field generated by an RFID reader. You can see the functionality demonstrated in the video after the break. By holding the bottom button as the cloner is moved in range of the RFID reader, the microcontroller goes into learning mode. Now just hold up the card you wish to clone and the LED just above the buttons will light up when it has captured the code. Now the device will act just as the original RFID tag did.
This was developed by [Ramiro], the same person who built the barebones RFID emulator we saw a few days ago. When researching that story we complete skipped over this gem. He’s posted a ton of information on the tag itself. It doesn’t look like he has any PCBs or kits left, but the schematic and code are available for download. You should check in on the design considerations section because it discusses the read/write function that isn’t built into the current version. That’s why you see some add-on components on the hardware used in the demo video.
It seems like this is a lot more user-friendly than the last RFID spoofer we looked at.