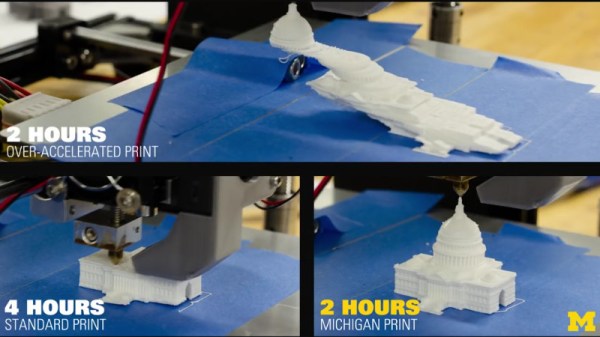
Recently, a YouTube video has been making the rounds online which shows a rather astounding comparison between two printed models of the US Capitol. Starting with the line “3-D PRINTERS CAN NOW PRINT TWICE AS FAST”, the video shows that one print took four hours to complete, and the other finished in just two hours by virtue of vibration reducing algorithms developed at the University of Michigan. The excitement around this video is understandable; one of the biggest limitations of current 3D printer technology is how long it takes to produce a model of acceptable quality, and if improvements to the software that drives these machines could cut total print time in half, the ramifications would be immense.
In only a few weeks the video racked up tens of thousands of views, and glowing articles popped up with headlines such as: “How to cut 3D print times in half by the University of Michigan” and “University of Michigan professor doubles 3D printing speeds using vibration-mitigating algorithm“. Predictably, our tips line lit up with 3D printer owners who wanted to hear more about the incredible research that promised to double their print speed with nothing more than a firmware update.
The only problem is, the video shows nothing of the sort. What’s more, when pushed for details, the creators of the video are now claiming the same thing.