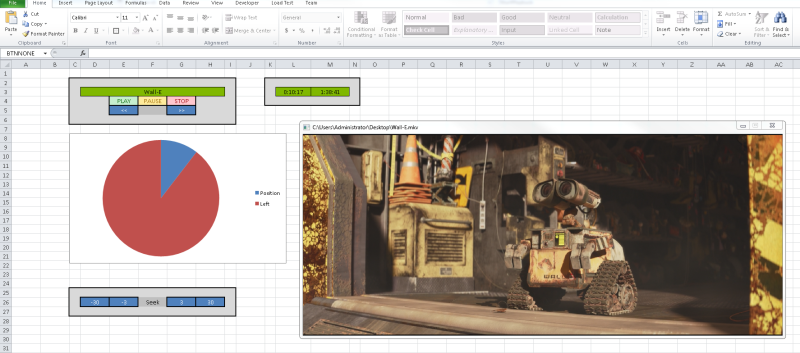
The Excel subreddit exploded earlier this week when redditor [AyrA_ch] shared his custom spreadsheet that allowed him to play video files on a locked-down work computer. How locked down? With no access to Windows Media Player and IE7 as the only browser (all plugins disabled, no HTML5), Excel became the unlikely hero to cure a 3-hour boredom stint.
Behind the cascade of rectangles and in the land of the Excel macro, [AyrA_ch] took advantage of the program’s VBA (Visual Basic for Applications) functions to circumvent the computer’s restrictions. Although VBA typically serves the more-complex-than-usual macro, it can also invoke some Windows API commands, one of which calls Windows Media Player. The Excel file includes a working playlist and some rudimentary controls: play, pause, stop, etc. as well as an inspired pie chart countdown timer.
As clever as this hack is, the best feature is much more subtle: tricking in-house big brother. [AyrA_ch]’s computer ran an application to monitor process usage, but any videos played through the spreadsheet were attributed to Excel, ensuring the process usage stayed on target. You can download it for yourself over on GitHub.















Monitoring process usage at work? That sounds particularly draconian.
Actually, I remember Wal-mart doing such a thing. They also kept track of every website you visited, and your boss checked in once a week to ask what every non-corporate URL was for.
Geesh… seems a bit too much. At my work, our system admin gave me local administrator rights for my workstation. Also, I am allowed to bring my own devices to connect to isolated wifi network.
I love how powerful excel actually is, when you get right down to it.
Seriously, people do all sorts of crazy crap with excel- a particular favorite of mine is the game of life, and someone else remade 2048 in excel too.
Not uncommon in Fortune 500 companies, particularly those in the financial arena. I love this workaround though.
Reminds me of high school days when we’d embed exe files into Word and play comet busters during AP CS class.
Great hack! Until you get caught. Somehow I don’t think the PHB will have the same appreciation for your creativity as we do. :-)
PHB’s are a blight on modern culture. Creative and intelligent people should leave companies with PHB’s and let them rot.
very old browser and scripting active? there are conditions that almost make that acceptable. i do not want to go anywhere near that network unless i had to. hopefully if they ever hire a pentester, they’ll like LOTS of paperwork.
I would go crazy at a job that restricted access that heavily. I spend a good part of my day surfing the internet and reading tech forums. And it makes me MORE productive than if I had someone watching over my shoulder all day and I didn’t have some time to think about problems and take a break. Then again my measure of being productive is not the same as someone that has to crank out a certain number of widgets an hour between the hours of 9am and 5pm, so that doesn’t apply to everyone.
Almost all fortune 500 companies log everything that all employees do. Normally it is mentioned somewhere in the pre-login splash screen in some obscure legalese style language, usually involving the word “may”. Most do not restrict what employees can do too much, just log. And all web access is usually logged via proxy servers – time and date, source IP, destination URL. Mostly the log files just sit there for years, and are only accessed when there is a “problem”.
E.g. HP used the log files to document Mark Hurd’s obsessive interest and continual hiring for obscene amounts of company money a “adult” movie actress over several years.
I used to have an excel speadsheet with a flash version of sonic the hedgehog embedded for school. Though I guess that relied on IE having flash installed.
hahahaha GJ
That reminds me of the “chains” that my boss put on our still working dial phone pbx that muted the first 30 seconds of the outgoing sound to hassle people from calling out from the shop phone, only the office was normal. Now everyone has a cellphone.
$17 shipping for a teensy 3.1, international. You must be kidding!
Some restrictions are there to protect the company’s IT-infrastructure and I’ve seen so many times how people have ignored these restrictions and introduced viruses etc in the corporate intranets… I particularly remember an incident at one of the biggest mobile operators quite a few years ago where we couldn’t bring data in to the office, nor use corporate laptops to connect to the public internet from home, only vpn to work.
It took less than 3 minutes after his laptop was plugged into the network at work on the Monday before the network showed congestion and a couple of minutes later virtually all computers were infected and continued to flood the intranet – globally.
We couldn’t work for more than three days and the costs were massive to say the least…
Think about the implications before ignoring some of the hurdles corporate IT has put in place. It can be very costly…
I too have been behind locked systems now and then throughout my life and there’s always a way around. Installing VMWare and using a separate (unrestricted) image is one solution, so is dual boot. This imposes little threat and risk of discovery. IP tunneling is an old bread-and-butter go-to solution which used to be a norm in the past.
Excel can hide telnet and ssh sessions, but who’s playing MUD nowadays? ;)
I am surprised such a tight security scheme would allow VB scripts. I ran into an issue with excel the other day at work with a VB macro and was told I needed to forget about using VB scripts due to our security policy.
They allow VB scripts because many companies have an entire infrastructure is built on top of Excel and VB. This happens because the only “development environment” made available to the drones is Excel, and they use it to make programs to make their jobs easier. Other people start building tools on top of those programs or linking them to other sheets, which reduces the number of people needed to do the job, and management starts hiring less people. Fast forward 20 years and you end up with a company that is entirely dependent on Excel from everything to cutting payroll to filling the vending machines. If someone from IT tries to put restrictions on Excel, some bauble somewhere in the interlocking mass of spreadsheets fails, nobody knows how to fix it, all the people that know how to do the job by hand are fired or dead, and there are two few employees to do the job manually anyway. On payday nobody gets their paychecks because the payroll system does not work anymore, the bosses go crazy with rage, and the IT guy gets canned for breaking payroll.
(And yes, this has actually happened at a company I work at!)
Every time somebody used excel for anything more than a shopping list, a puppy dies. People who use it to create mission critical functionality should be shot.
Agreed, now if there was only an Excel script to handle the firing…
You’re fired.
When I worked at citigroup, my main morning task was to remote desktop into over 3000 terminal servers and make sure that all the services were running properly. This took hours. So, enter VBA and excel. First column was the names of the servers to check, each column after that was for a specific service that needed to be queried. WMI connections to each of the remote servers gave me the status of each service and I simply changed the background of each cell for the respective service to red (stopped), yellow (delayed), or green (started). Start the macro, go have a smoke, come back and the checks were done. Saved me TONS of time. Ended up giving it to some other teams which had similar tasks. They just change the server names and services and ran it.
Great job! I’ve seen places that lock a PC down like this, and more. Only problem is many places WILL install some type of monitoring software, like net nanny, that records what you do. So, you can get caught. My work places did this, probably still does, so we have to keep in mind that it is their equipment, their time that is being paid for. Hell, for a long while, many many sites were blocked (hackaday being one), and you had to submit a physical form, signed by management members, in order to get access to sites. Took days if you were lucky. Ones we needed to access some site that was located in Cummings, Georgia, it was blocked, and it took weeks to not only get TEMPORARY access, but to prove we were not looking at porn! Hell, our internet usage is currently throttled to barely above 56k modem speed. So yeah, there are places and people out there with THAT many control issues.
Had a boss tell me to check a hq user computer for anything wierd has we had a report of it having teamviewer connections in the middle of the nigth (2-3AM) frequently.
Remoted to the machine, found lots of games, porn, a running torrent client, teamviewer in service mode, the pc was on a server restricted subnet (hence torrents and teamviewer possible), local admin on the user account and a external hdd filled with piracy and virus.
Removed all non work related programs and files (lots of porn), formated the external hdd, blocked USB, full virus cleanup, fixed the network settings and set the user to our special “guest” restricted account. The boss got a “little” upset when i submited the report that i did a so heavy cleanup on a hq computer without informing the user… the user was pissed… really pissed, told him if he didn’t like what i’ve done that he should submit a report to his boss complaining about me, it was the last i’ve heard of this incident.
tldr; we put these restrictions because people abuse the systems
I’m surprised you didn’t show the boss just what was on the computer before you removed it.
This was usually the sales guys at a previous job. Didn’t even try to hide it — “well, he’s on the road a lot, so I don’t see what’s wrong with pr0n and pirated gamez on the company laptop. We can’t expect him to travel with two!”
Oh, also, this would not work with my company, vb scripts, macros are disabled on our pcs
It’s interesting how people always find solution how to do something like this.
That’s really impressive hack.
However many of companies have remote administration applications installed into workers PCs so main supervisor can always see what they’re doing, so it’s good until they get caught.
Thanks for share!
Adam
A thought experiment I have put to co-workers numerous times over the years is to come up with clever ways to surreptitiously extract data from a locked-down work machine (no USB ports etc). The responses have been quite interesting, from the obvious (audio port sending data to a set of headphones containing a secret MP3 recorder) to the absurd (e.g. modulating an ethernet LED with the data and recording it with a photo-diode).
Not as absurd as you might think, old modems usually had their data light tied directly to the data output so you could with a small bit of work actually read the serial stream of that “secure” modem by simply watching the blinking light :)
Another particular nasty data leak the monitor.
Lookup up stuff on TEMPEST, keyboards causing RF spikes, power supplies, grounding issues, microwave emissions.
If a PC has a firewire port, that’s a direct path to memory totally bypassing ANY security on the system if the port is active for any reason. including internal ports that may have been overlooked when the security boys filled the USB ports with epoxy.
Try copying everything you want into ram, then while its on, pull the ram, spray down the ram with a coolant, liquid nitrogen or canned air and then place that in a insulated thermos containing the coolant, take it offsite, then extract the contents.
http://www.zdnet.com/blog/security/cryogenically-frozen-ram-bypasses-all-disk-encryption-methods/900
If you’re going to the trouble of taking out the RAM might as well take the hard drive too.
Much harder to smuggle out undetected, and if anyone tries to use your machine in the mean time you’re busted. You could, however, sneak out a RAM board without the entire machine stopping altogether.
not the ethernet diode, but close:
http://hackaday.com/2012/10/30/extracting-data-with-keyboard-emulation/
Who would block a keyboard :)
I work for a large company, over 100k employees just in the UK. We get told about fair use and all that with some sites blocked but we can stick youtube on, plug our own devices in and not one problem has ever happened.
Back in high school I used VBA’s access to winapi to make a registry editor and re-enable stuff. Fun times!
Also embedding activex controls such as an IE frame were no brainers
I did something similar on one of the schools at my former college… lasted about a month until the sysadmin did a log check and noticed something was up. Said sysadmin was one of my professors. He was very impressed, but not very happy.
Excel is a very powerful tool, if you know how to use it. I’ve built full SCADA system in It with VBA and DDE. It’s my goto system bypass tool on restrictive systems. Can in real handy several years ago at ShmooCon. Whipped up a quick we browser and file explorer in Excel and completely bypassed the kiosk. Then grabbed Firefox portable and was good to go.
But where do the movies come from? I assume they are from the internet. Do they really go through so much trouble to lock things down but not watch the network?
Or are you bringing them in on some physical media? Did they not block that too?