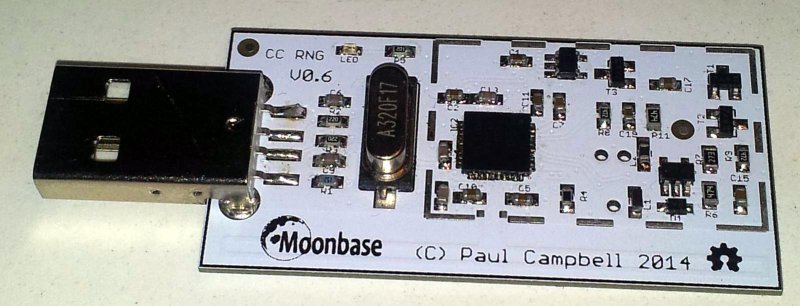
[Paul] designed a new open-hardware RNG (random number generator) that includes two sources of entropy in a small package. The first source of entropy is a typical avalanche diode circuit, which is formed by a pair of transistors. This circuit creates high-speed random pulses which are sampled by the onboard microcontroller.
What makes this design unique is a second entropy source: a CC2531 RF receiver. The RF receiver continuously skips around channels in the 2.5Ghz band and measures the RF signal level. The least-significant bit of the signal level is captured and used as a source of entropy. The firmware can be configured to use either source of entropy individually, or to combine both. The firmware also supports optionally whitening the entropy byte stream, which evens out the number of 1’s and 0’s without reducing entropy.
The OneRNG uses the USB-CDC profile, so it shows up as a virtual serial port in most modern operating systems. With the rngd daemon and a bit of configuration, the OneRNG can feed the system entropy source in Linux. [Paul] also has a good writeup about the theory behind the entropy generator which includes images of his schematic. Firmware, drivers, and hardware design files are open-source and are available for download.
















Interesting project. I would like to see a lot more test results prior to using this for anything critical however. Ent is a good start, but it needs to be run on multiple independent data sets from different test runs for each mode. And the same needs to occur with the dieharder tests. Which takes a LOT of random numbers. Which is why three years after starting, I am still generating data for tests. Look forward to hearing more about this project.
I was glad to see the whitening support, but I’d have definitely used the AES capability of the chip to do better whitening than CRC16. Still, I’ve had plans for 9 months to do a dongle exactly like this and never finished. I admire the execution of this one, especially the dimming of the LED when you pull data. Simple and brilliant.
(I’m the designer) – like the recent posting on HN this one’s a little early, we weren’t planning on doing a full release for about 6 weeks, after our beta testing is done, at that point we’ll be doing a kickstarter, we hope people will support us then – meanwhile I guess all publicity is good publicity ….
we avoided using the internal AES because we can’t reasonably verify it – CRC16 can be verified by running a parallel well understood algorithm. We expect our data will normally be passed through a real whitener when it’s used, it’s an entropy source, not a high quality RNG – by default when you install the linux .deb/.rpms then when the device is plugged in it automatically runs rngd, a daemon that feeds the kernel entropy pool – the kernel RNG does the whitening for you.
More generally we provide raw data (unwhitened) from both sources so there’s greater transparency all around.
AES in the cc2531 has to match that used for encrypting zigbee so one assumes it’s meeting a more global standard but our more general worry of course is some external subversion.
The board is programmable (it requires an external programmer) and the source (hardware and software) will be on github when we start our kickstarter. We encourage people to hack on it and write their own code – we have examples of how to use AES if you feel the urge (so you can encrypt the data going over the USB).
For code examples the general code base is based on the code from our IoT project – source and hardware designs at:
http://www.moonbaseotago.com/cheaprf/
The chip is by TI to support ZigBee which operates on the 2.4Ghz band, not 2.5Ghz as noted in the article.
In addition, the source doesn’t look random if I can influence the source, what if I put a constant RF signal generator while you are collecting randomness? Would I be affecting your collection?
You’d have to skip around and be able to influence the least significant bit of the signal. Being able to bias the number generation is possible, but how much depends how it’s mixed in with the source from the avalanche diode. I’ve not RTFA yet.
I’m not sure he would have to be able to skip around, he could just use a wide bandwidth to blanket the whole 2.4Ghz spectrum. As for the least significant bit, what if the signal from the signal generator completely swamps the chip? If the signal is ‘off the charts’ does the least significant bit still move?
Of course, that still doesn’t eliminate the randomness from the diode.
Yeah, the page actually says that it’s susceptible to external noise, so it’s not a great choice.
He might’ve actually just been able to terminate the antenna to ground using some large resistor, thus making it a ton less susceptible to external interference, essentially just measuring the thermal noise of the resistor. Add a cheap board-level shield and it should be pretty safe.
Just using the LSB would worry me, though – the LSB of an ADC is usually not particularly random since many ADCs have decent differential non-linearity, so adjacent bits aren’t equivalent widths. In the theory page it says they measure slightly more 1s than 0s – so at a very basic level, it’s not very random at all.
More I was trying to say it was potentially susceptible – we’re dealing with security stuff here so a modicum of paranoia is required, I’m just trying to put all the cards on the table so people can make choices – we skip around in freq and don’t allow the demod PLL to lock. I actually expect a strong interfering signal would still have random noise in the LSBs (remember we’re reading the input to the demod, not the output) – however, in the interests of appropriate paranoia the RF source is by default
We measure more 1s than 0s on the avalanche diode because it’s sampled in the analog domain (not the cc2533 RF) – the RF source is actually much better, it has a tiny bias the CC253x data sheets actually have some analysis of this method of creating random data which looks quite good (and matches my experiments)
Broadband jamming is standard military issue across the planet. I’d be curious to see tests done against this system with a signal generator just to see if it could even be statistically influenced.
What’s the practical chance that somebody is going to use a military jammer, smart enough to influence the LSB? I’d worry more about somebody breaking into the computer and tracing all USB traffic
The chance go up considerably, the more important your use of the device is. Cryptography is rarely broken now days, but poor habits and weak points (such as potential radio interference) are how work arounds are discovered.
First of all, people would have to know that you’re using a device like this, and how it works, then they would have to care enough that they can set up their equipment, and have it tuned enough so that it can influence the last bit.
Unless you’re going to use this as a launch code for your nuke, nobody’s going to care enough to go through all this trouble. And even if they do, it will be more effective to waterboard your sister until you give them the secret key.
Avalanche noise circuits exhibit a great deal of change over time. Which can significantly change the bias in the system. I am curious as to how thise circuit will perform over a period of a year or so.
The RF based sampler is disabled by default. The end user has to specifically enable the RF based RNG output. In the article (RTFA right?) he states that this is on purpose as the RF sampler can be biased by the environment, though he shields this with the EMI shielding can, which provides some (read ‘very little’) protection.
Reportedly, a microwave oven gives about -40dB attenuation.
just for the record we do not shield the antenna for sampling RF noise – there’s a folded dipole under the copyright message, I’m not convinced that one could easily (or at all) jig the RF generator with an external signal – but I think that people are right to be paranoid about it which is why we disable it by default – if you’re running this on a web server in a co-housing environment the amount of other extra noise is going to make the LSBs of any signal pretty impossible to predict (especially if you also can’t predict the clock it’s being sampled on)
Could two identical OneRNGs produce similar results if they were put next to each other in a strong MW field?
Unlikely. 2.4 GHz signals have a wavelength of just 4 inches, and in typical environments there will be plenty of reflections causing wild fluctuations in signal strength if you move the antenna just an inch or two. That’s why good WiFi devices have multiple antennas.
That’s another reason why outside influence is mostly a paranoid dream. You have to know exactly all the reflections and attenuations.
I’m actually deeply interested in knowing all those reflections and attenuations. I think it would be a really cool visualization.
Computational tomography shows an efficient algorithm for deriving spatial data from one-dimensional measurements. Iterative reconstruction preserves even more information, costing more compute.
MIMO techniques discuss a ‘Q/R matrix’, the properties which I admit escape me. It appears to involve the modern techniques related to belief propagation; for our purposes a generalization of efficient, iterative techniques which preserve information as it passes through noisy channels. I believe MIMO, when electrically rotated, results in a series of one-dimensional measurements from which one can derive spatial data, just like in computational tomography.
If you have a WiFi signal strength meter, and use that to drive a colored LED, you could move it around the room, and take a picture with long exposure. Sounds like a fun project.
Of course, by walking around with it, you influence the patterns with your body.
That would be a very neat approach! Perhaps a job for a micro quad-copter? =)
Has anyone noticed how awesome their choice of name was?
To put it simply: it rules them all.
Hasn’t this already been done multiple times?
http://ubld.it/products/truerng-hardware-random-number-generator/
http://www.entropykey.co.uk/
http://en.wikipedia.org/wiki/Comparison_of_hardware_random_number_generators
Your point?
he learned to google and he’s showing off
Insane prices for some of them. LOL.
Nice project. Iam working on similar version using
a low gamma sensor with scintillator and 40K as this is
not in any way regulated :-)