Sometimes we see projects whose name describes very well what is being achieved, without conveying the extra useful dimension they also deliver. So it is with [Prasanth KS]’s Windows PC Lock/Unlock Using RFID. On the face of it this is a project for unlocking a Windows PC, but when you sit down and read through it you discover a rather useful primer for complete RFID newbies on how to put together an RFID project. Even the target doesn’t do it justice, there is no reason why this couldn’t be used with any other of the popular PC operating systems besides Windows.
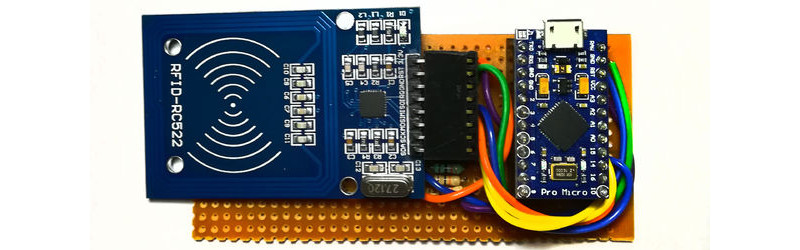
The project takes an MRFC-522 RFID module and explains how to interface it to an Arduino. In this case the Arduino in question is an Arduino Pro Micro chosen for its ability to be a USB host. The supplied code behaves as a keyboard, sending the keystroke sequence to the computer required to unlock it. The whole is mounted in what seems to be a 3D printed enclosure, and for ease of use the guts of the RFID tag have been mounted in a ring.
As we said above though, the point of this project stretches beyond a mere PC unlocker. Any straightforward RFID task could use this as a basis, and if USB is not a requirement then it could easily use a more run-of-the-mill Arduino. If you’re an RFID newbie, give it a read.
Plenty of RFID projects have made it here before, such as this door lock. And we’ve had another tag in a ring, too.



















I’m wary of wireless unlock methods. I use a mechanical key to start my desktop.
It’s more for looks.
I just hit the power button, then stare very hard at it – presuming it recognizes me and logs me in automatically bcz ‘we cool’ with each other — that and I use analog world methods of fear shd any one even consider touching my computer.
This is actually a sort of neat idea. Do you just use a lock as a way to short two wires? Or do you activate a device with the mechanical key which sends a crypto key to another device to turn on the PC?
USB-HID not Host.
Nitpicking. :)
It’s not nitpicking. USB HID is slightly easier to do than USB-HOST.
USB-HID is used when the Arduino is to be connected to a computer.
USB-HOST allows the Arduino to talk to a device like a Mouse, Keyboard, or the serial port of another Arduino.
I wish the Leonardo or the Atmega 32U4 would do USB Host natively. Instead, a MAX3421E must be connected to the SPI pins of an Arduino and a whole bunch of code will serve as a USB driver to make the whole thing work.
I learned this the hard way when interfacing two Arduinos through a USB cable.
https://www.instagram.com/p/BXVK_BChVLh/
Ok, so this is for convenience rather than security right? Because the Arduino micro has to store the password, most likely in flash. Granted, someone would have to read the Arduino with a suitable programmer, but displaying the flash contents would reveal the password if its displayed in ASCII (as many hex editors allow)… but even so, you’re giving up security for convenience, which means.. why password protect your PC in the first place?
The fob could contain up to 4K of information. More than enough for even a large password.
Except it doesn’t. He’s depending on the totally-insecure 32-bit card-ID.
I built a very similar system with the same parts. I used a few methods of security. First, the MiFare classic key was used to protect the data (merely a delay, like the ‘this lock has to last at least 30 seconds’ kind of thing) rather than using the UID of the card which should NEVER be used for anything other than communication with the card. Second, the password was not stored on in the data on the card but a chunk of encrypted data. A second chunk of encrypted data was stored in the pro-micro. When the card was swiped, the key was used to read it’s data and then the 2 between them were used to get the actual password used to unlock the PC.
In order to break this system a hacker would require physical access to both the card and the reader ,neither alone would get them my password. The various security methods such as the MiFare key, encrypted and split data password along with code read protection should cause it to take long enough I would notice the card/reader missing.
It’s by no means “secure” but as long as I hold onto my card the odds of anybody getting my password that way are low enough I don’t need to worry.
No mention of the obvious flaw here that activating it with a text editor open reveals your password in plain text?
Also, I’m guessing that re-flashing the Arduino would discourage regular password changes.
That all being said, I’ve got a few RFID rings and a reader, I might just have a play :)
See my comment above, there are many ways to improve this but yes, a text editor would reveal the password but NOT on a windows box. My device presses ctrl+alt+del before entering the password. On windows that puts the machine into a state (when unlocked already) that it doesn’t enter the text into any open text editor. You would need to remove the box and card from my machine and setup a system designed to capture the text input so even if I was careless enough to leave my card laying around with the reader by my PC alone with somebody who wanted to hack it, they couldn’t easily do so unless they snuck in their own dedicated system to capture the text.
There are many other ways to improve this system and I would love more people to do this and post on HaD with their results!
Quoted from the project page : “I can’t guarantee any security”… aaaaah ok then !
I remember the “security” password on the IBM PS/2 which was easy to by-pass simply by removing the BIOS backup battery then replace it.
LKWPETER
AMI
AWARD
…. I still remember that it was not even needed to remove a battery.
I remember how you did it by adding a battery.
It was AWARD_SW and AMIAMIAMI wasn’t it?
RFID? NAAAAAAAAAAAAAAAAAAAAAA Dat’s an inductively coupled tag bro.
the case is not 3d printed.. it is a expanded pvc board used to make boxes.. nice project though!
I have got the same thing for my desktop and also for the garage door at home, same key opens both.
here is the garage door thing, in spanish https://www.youtube.com/watch?v=Rl_rbQglnkA
it activates an optocoupler that press the button at the motor side
I did something similar, but with a custom reader optimised for an implantable tag.
https://0xfred.wordpress.com/category/electronics/nfc/
The is some protection from the “type into a text editor” attack by sending Ctrl-Alt-Del first. Of course you’d also have to force me to put my hand against the reader to get it too.
By the way, I’ll be the first to admit that my device (much like the one featured here) is a convenience device rather than a security device. Anything which adds another way to log in can only make security worse.
So much wrong here. First, it’s not RFID, it’s NFC, and RFID is infamous for being totally insecure. While NFC *can* be secure, this is horrifically insecure for a number of reasons: the windows password is stored in the device, and it only uses the card ID to identify the card. Those IDs are trivially spoofed and have no security whatsoever. You should have heard the endless howling on infosec-twitter about this project when it appeared on the arduino website.
There are a couple of good ways of doing NFC unlock: the readers usually have a serial-port mode and follow an ISO standard for interacting with smartcards… and there are Windows drivers that support them! So you can basically plug together a fairly-secure smartcard authentication solution, WITHOUT the arduino, without the plaintext password in the arduino and without implementing a USB keyboard. But that’s no fun.
If you insist on rolling your own NFC authentication scheme, you gotta do more than just read the ID. You need to use a secure card like a DESFIRE, and mutually authenticate between the card and reader.
When doing this though, I found that those cheap blue RC522 boards (as pictured) have an improperly designed antenna that will not provide sufficient power to anything but the most basic and low-power, insecure chips (MIFARE and NTAG); they will not boot a DESFIRE. You need to buy a better reader to talk to a secure card, which has higher power consumption.
The RC522 chip itself is probably fine and has all the right protocol support (except of course the Arduino library everyone uses can’t do much more than read the card ID!) but the antenna design on those cheap boards is a failure. In theory you can improve them by changing some of the inductors on the board (they look like SMD caps but are black), but it’s easier to just buy a better-designed board like the PN532 from dfrobot, which has a full-size and properly-coupled antenna.