We love a good deep-dive on a specialized piece of technology, the more obscure the better. You’re getting a sneak peek into a world that, by rights, you were never meant to know even existed. A handful of people developed the system, and as far as they knew, nobody would ever come through to analyze and investigate it to find out how it all went together. But they didn’t anticipate the tenacity of a curious hacker with time on their hands.
[Eduardo Cruz] has done a phenomenal job of documenting one such system, the anti-piracy mechanisms present in the Capcom CPS2 arcade board. He recently wrote in to tell us he’s posted his third and final entry on the system, this time focusing on figuring out what a mysterious six pin header on the CPS2 board did. Hearing from others that fiddling with this header occasionally caused the CPS2 board to automatically delete the game, he knew it must be something important. Hackaday Protip: If there’s a self-destruct mechanism attached to it, that’s probably the cool part.
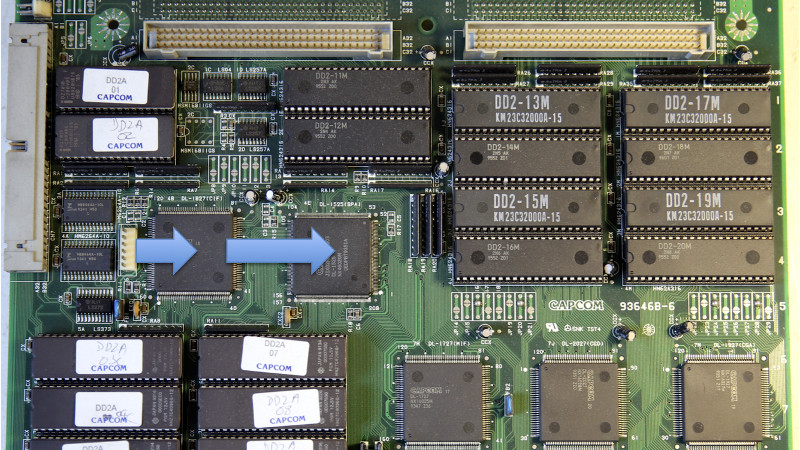
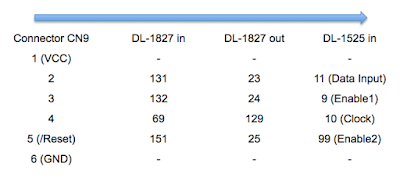 He followed the traces from the header connector, identified on the silkscreen as C9, back to a custom Capcom IC labeled DL-1827. After decapping the DL-1827 and putting it under the microscope, [Eduardo] made a pretty surprising discovery: it wasn’t actually doing anything with the signals from the header at all. Once the chip is powered up, it simply acts as a pass-through for those signals, which are redirected to another chip: the DL-1525.
He followed the traces from the header connector, identified on the silkscreen as C9, back to a custom Capcom IC labeled DL-1827. After decapping the DL-1827 and putting it under the microscope, [Eduardo] made a pretty surprising discovery: it wasn’t actually doing anything with the signals from the header at all. Once the chip is powered up, it simply acts as a pass-through for those signals, which are redirected to another chip: the DL-1525.
[Eduardo] notes that this deliberate attempt at obfuscating which chips are actually connected to different headers on the board is a classic trick that companies like Capcom would use to try to make it harder to hack into their boards. Once he figured out DL-1525 was what he was really after, he was able to use the information he gleaned from his earlier work to piece together the puzzle.
This particular CPS2 hacking journey only started last March, but [Eduardo] has been investigating the copy protection systems on arcade boards since 2014.
[Thanks to Arduino Enigma for the tip.]















why dont they go to capcom to get the info?
if the hacking is being done as part of hame preservation society then capcom should be happy to allow it.
unless capcom or who ever bought out capcom intends to or is still using that security method on their latest titles.
just in the same way that are dusting off old phishing methods like the 900 number dialer capcom or it’s new owner may intend to bring back the same protection
Sometimes companies are forthcoming with the info, and sometimes they aren’t. If there are any intellectual property rights at stake and any unknowns (such as questions about who holds rights), companies tend to get very tight-lipped. Also, like others have said, sometimes information gets lost.
Having heard how Capcom treats its employees, I’d be very very surprised if they were willingly giving out information about their copy protection.
Name a Good / Publisher / Dev Studio in 2018 Can’t think of one that’s involved in games that are.
CD Projekt Red? Tell Tale? Obsidian?
Guess it depends on how you define “good”, and I fully admit even the above “off the top of my head” list is embarrassingly tiny, but there are still some good studios and dev houses out there.
Paradox Interactive as well!
And sometimes (well most of the times) the original info is lost due to lack of archives, regular cleanups, server obsolescence, acquisitions/merger.
To clarify, I did go to Capcom about a decade ago. I spoke to someone quite high up within Capcom, with stints in both Japan and the USA. The following came to light:
1. Capcom did still have “the info” at that point, as they were still actively servicing CPS2 hardware in Japan at that point.
2. They would only service Japanese region hardware.
3. They would only accept service requests from addresses within Japan.
4. They were very aware that there was no means of servicing non-Japanese region CPS2 hardware, since Capcom’s coin-op divisions in the USA, in the UK/Europe and in Mexico were either no longer servicing CPS2, or the divisions had closed entirely. They were also quite apologetic about this.
5. They absolutely would not release any info. They could only suggest that dead non-Japanese region CPS2 titles are either replaced with working boards from resellers or, curiously, an “unofficial repair” is sought.
So it took over ten years, but we eventually devised the method of “unofficial repair” ourselves. If you’d have asked me back then though, I’d never have thought that I’d be partially responsible for it, however! :)
Oh I can think of a lot of reasons:
– They just aren’t bothered to reply to someone asking for what basically is abandon ware
– CapCom doesn’t want to spend time and money to dig it out of the archives, if it’s in the archives at all
– Patents, need I say more?
– Licencing, maybe the protection was outsourced, disclosing it may lead to a legal battle
– The information is lost, archives, files, degradation of media, hardware/software that contains the info doesn’t work anymore etc get lost over time.
Once the game is no longer supported, Capcom has no reason to keep any documents relating to it. Any documents they do have are likely in a dusty file cabinet or on backup tapes that would take serious effort to restore.
The game may be no longer supported, but the “gaming engine” within that game may be used in current “supported” products.
Really, really, really, incredibly unlikely 20-odd years later. Modern hardware almost certainly has nothing in common with it. CPS2, as far as I remember, is Motorola 68000 series with a tile mapping / sprite engine. Modern arcade games, such as they even make any more, are often modified console hardware, which is cheaper.
There must be some almost-pensioned guy over at Capcom, of whom nobody knows anymore what he’s doing there, but who’s still on the payroll, who resides in a lab that has all the supplies that anyone could wish for, and who knows where to find all the stuff that he ever worked on in the past. I’m sure of it.
Yeah but he’s Japanese, and they have weird things about company loyalty. It’s like life or death to them, vs the begrudgement and mistrust more enlightened peoples feel towards their companies.
I did get a guy at Moog-Animatics to dig up all the info on an old Animatics servo controller, as used in a Light Machines PLM 2000 benchtop CNC bed mill. He was with Animatics before Moog bought the company. They’d kept old backup hard drives from before. One of these days I may explore some of the functionality Light Machines (and later, Intelitek) never used. The controller has some internal program storage for running G-Code without an external control computer. Set it up right and one need only poke a button to repeatedly run the code.
You are over-thinking it. Most legal departments take a reasonable position on risk mitigation:
void request_info (details)
{
if (revenue opportunity)
return boilerplate();
else
return “no”;
}
The return type is not a mistake….
Security doing what it does best. Delaying the inevitable till it’s no longer of any value.
What a fascinating read! I had read his first post on trying to figure out that long-lasting security measure and was wondering when he would manage. He even shared a way to reconfigure/de-suicide CPS2 board using an arduino. So many boards will be able to be saved/repaired now that this is available. Truly in the spirit of Hack-A-Day!
Concerning the CPS2 security reverse engineering project, there is also a non-technical story to tell.
It was mostly by chance that a few of us whom had either the right skills and knowledge, the right contacts, or even a few scraps of information that (from a friend of a friend of a friend who may have once dealt with Capcom, or some such scenario) or a combination thereof! The fact that it all came together is indeed a tale of ups and downs and minor miracles over quite a long, drawn-out period.
The fact is, at one point, I had to put money down to secure some clues which would later turn out to be the very starting point of the project. I took a gamble which could either have lost the information forever, or revealed a few secrets. Fortunately, it was the latter. I sat on this info for some time, not really knowing what to do with it or who to talk to about it. A few people came along, discussions started, arguments were had (as is always the case when very intelligent people, with very different ways of working, get together), and people left. The project had stalled.
Eventually, a long-time contact pointed me in the right direction of some others who were keen to work on it. And indeed, work began.. Analysis was done. Test equipment travelled in various directions between the UK, Australia, Spain, Mexico and Brazil. Some of it remained in the hands of other team members for a considerable time while real life took priority. More disagreements to work through, team members left the project, time passed, team members returned… Somehow, through all this, things kept moving. By now, Eduardo was on the case and this was well and truly an Arcade Hacker project. Worked continued, but now with some pace.
Postage of test equipment between continents also took time, and it was often unsettling not knowing if the test equipment would even arrive at all. Fortunately, it did, and nothing was lost.
In short, things could easily have gone very wrong at so many points, but thankfully everything somehow worked out just fine!
Eduardo did some great work on this, and I am very pleased to have been put in touch with him. But really, there were a whole bunch of others who acted as intermediaries (and in some cases mediators) all of whom helped to pull this all together.