In the movies, the most-high tech stuff is always built into a briefcase. It doesn’t whether whether it’s some spy gear or the command and control system for a orbiting weapons platform; when an ordinary-looking briefcase is opened up and there’s an LCD display in the top half, you know things are about to get interesting. So is it any surprise that hackers in the real-world would emulate the classic trope?
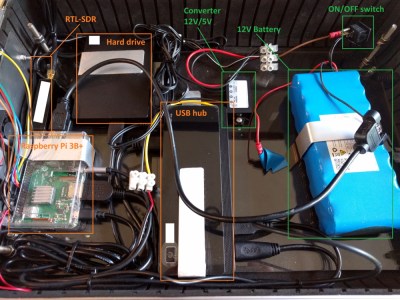 As an example, take a look at the NightPi by [Sekhan]. This all-in-one mobile penetration testing rig has everything you need to peek and poke where you aren’t supposed to, all while maintaining the outward appearance of an regular briefcase. Well, admittedly a rather utilitarian aluminum briefcase…with antennas sticking out. OK, so it might not be up to 007’s fashion standards, but it’s still pretty good.
As an example, take a look at the NightPi by [Sekhan]. This all-in-one mobile penetration testing rig has everything you need to peek and poke where you aren’t supposed to, all while maintaining the outward appearance of an regular briefcase. Well, admittedly a rather utilitarian aluminum briefcase…with antennas sticking out. OK, so it might not be up to 007’s fashion standards, but it’s still pretty good.
[Sekhan] has crammed a lot of gear into the NightPi beyond the eponymous Raspberry Pi 3B+. There’s an RFID reader, an RTL-SDR dongle, an external HDD, plus the 12V battery and 5V converter to power everything. All told, it cost about $500 USD to build, though that figure is going to vary considerably depending on what your parts bins look like.
To keep things cool, [Sekhan] has smartly added some vent holes along the side of the briefcase, and a couple of fans to get the air circulating. With these cooling considerations, we imagine you should be able to run the NightPi with the lid closed without any issue. That could let you hide it under a table while you interact with its suite of tools from your phone, making the whole thing much less conspicuous. The NightPi is running Kali Linux with a smattering of additional cools to do everything from gathering data from social media to trying to capture keystrokes from mechanical keyboards with the microphone; so there’s no shortage of things to play with.
If you like the idea of carrying around a Pi-powered security Swiss Army knife but aren’t too concerned with how suspicious you look, then the very impressive SIGINT tablet we covered recently might be more your speed. Not that we think you’d have any better chance making it through the TSA unscathed with this whirring briefcase full of wires, of course.
















You might want to add some cooling there…
…and maybe a fuse on that big lithium battery with uninsulated crimp connectors (rear of the on/off switch). And with that loose crimp connector wrapped in insulating tape. It only needs to just brush against the other terminal and short for a moment!
I’m looking at it and my very first through is “good luck going through a airport with that”.
It looks fun, but not enough spit and polish.
I don’t think “will it get through airport security” is a good way to gauge efficacy of most projects featured on Hackaday.
It is in a briefcase for transport, if is was not in a case for travelling then I would not use it as a gauge.
I did like the Sherlock software that it uses which pulls username information across 140 social media networks (A tiny bit surprised that hackaday.io was not included, but probably a tiny user base when compared to the other 140 websites).
There is space between each component, good cablemanagment, so easy for security staff to identify approximately what is what.
Remove the battery and it should go through European airports without issues.
Quite true. I regularly have problems getting a normal laptop with one spare battery and one external hard drive through US airports. But that is usually when I have to fly through LAX and San Diego. LAX is TSA’s “everybody here is a new-hire trainee” airport on west coast, and San Diego is one of TSA’s “problem child” airports. Never had any problems in the rest of the United States, Japan, Australia, Europe, Africa, or the Middle East. Just LAX and San Diego. O’Hare is always nightmare, but that is not the TSA’s fault.
First time I’ve seen “good luck getting through airport/tsa” on Hackaday…
Full time red team here with multiple years of experience. Never been stopped by TSA for anything other than wire clippers and a “badge” I made in resin because they thought the resin was “gel.” When i knocked on it and it was hard as a rock they just sort of went… uhh ok. I’ve worked with DHS in multiple ways and they are not looking for “hacking” tools. Even a savy line agent, (which I have not run into with 50k plus a year miles for multiple years) would be diverted with a business card that says “security engineer” or even just “engineer.” I cant tell you how many times my bag of deviance has passed through security, carry on. I once had 1 person ask me about it out of curiosity after I said I was working with partnership with DHS on something and at the end of the convo I said: “Honestly it doesn’t even matter much because the most destructive thing is that *points to laptop*…
Caveats: Traveling US domestic. Nothing that is “store bought” like a hak5 pineapple or etc.
Anyone actually get pulled out of line for hacking tools? Also please know I understand that if you make a briefcase look like a bomb (above article) or play into movie tropes you will have much higher risk to be flagged.
I carried 5x20m of Ethernet cable in carryon. Was pulled out of the line but could take it after explaining what it was. I guess it looks atypical on the x-ray scanner.
I used to work on medical equipment. Along the way, a customer gifted me with an old black leather bag like doctors used to carry. It became my tool bag that I often took through airports.
On one occasion, a young agent asked me to open it and then began to examine the contents. She found lots of optical equipment, forceps, clamps and tubing. But then her eyes opened wide as she lifted out a 2 foot long chain wrench. She looked me straight in the eyes and asked, “What kind of a doctor are you?”
It took incredible willpower to resist saying, obstetrician, but I didn’t want to miss the flight.
This made me genuinely laugh out loud. What a great story! And your willpower… I’d have said “Proctologist”!
You never know when you have to open up a jar of pickle, jam, honey etc that your “patient” may want to eat. :)
Marvelous!
A friend of mine who is a doc in the ER used to play “guess what this is designed to extract, and from where” with us on poker night. Truth is often stranger than fiction.
Is the cost not a bit high?
I would properly have gone for an old low-power laptop + new/extra battery to reduce the BOM a bit.
“It doesn’t whether whether”. That’s if it’s open.
Guys (and gals): I’m not in your business so could someone tell me the purpose(s) of the RFID reader in this set-up?
Useful for copying passive RFID devices (such as credit cards and some keycards), for one thing.
Why didn’t you use rpi4