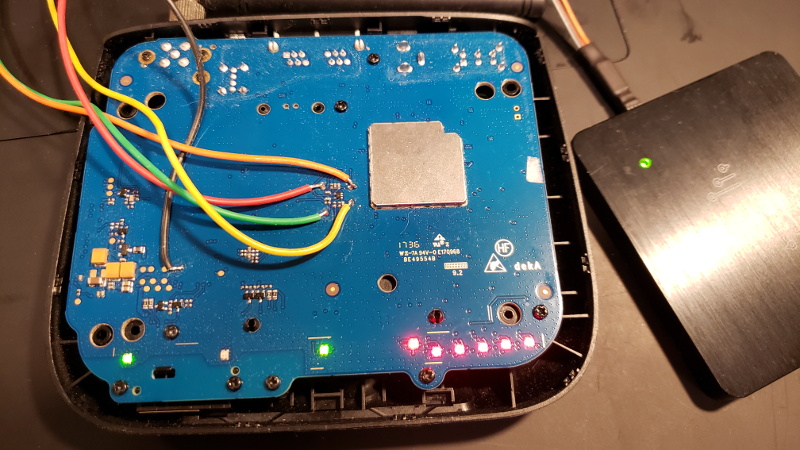
[Jason Gin] wanted to reuse the SIM card that came with a ZTE WF721 wireless terminal he got from AT&T, but as he expected, it was locked to the device. Unfortunately, the terminal has no function to change the PIN and none of the defaults he tried seemed to work. The only thing left to do was crack it open and sniff the PIN with a logic analyzer.
This project is a fantastic example of the kind of reverse engineering you can pull off with even a cheap logic analyzer and a keen eye, but also perfectly illustrates the fact that having physical access to a device largely negates any security measures the manufacturer tries to implement. [Jason] already knew what the SIM unlock command would look like; he just needed to capture the exchange between the WF721 and SIM card, find the correct byte sequence, and look at the bytes directly after it.
Finding the test pads on the rear of the SIM slot, he wired his DSLogic Plus logic analyzer up to the VCC, CLK, RST, and I/O pins, then found a convenient place to attach his ground wire. After a bit of fiddling, he determined the SIM card was being run at 4 MHz, so he needed to configure a baud rate of 250 kbit/s to read the UART messages passing between the devices.
Once he found the bytes that signified successful unlocking, he was able to work his way backwards and determine the unlock command and its PIN code. It turns out the PIN was even being sent over the wire in plain text, though with the way security is often handled these days, we can’t say it surprises us. All [Jason] had to do then was put the SIM in his phone and punch in the sniffed PIN when prompted.
Could [Jason] have just run out to the store and picked up a prepaid SIM instead of cracking open this wireless terminal and sniffing its communications with a logic analyzer? Of course. But where’s the fun in that?

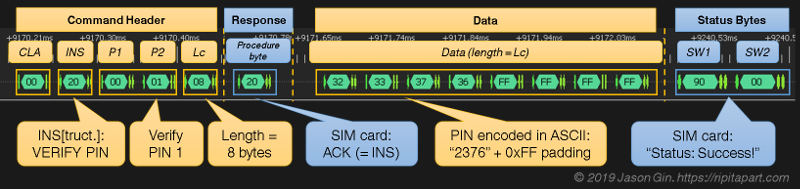














All communication to SIM card is “plain text”. No encryption or authentication, etc. You can sniff everything.
But you might hope the data was stored in an encrypted state so that this method of sniffing wouldn’t give up the keys to the kingdom on a silver platter.
Don’t forget, it’s designed as a PIN – a personal identification number, identifying the human “subscriber”; there’s little sense in assuming the communication between the user’s device and its SIM is being intercepted. That link is just as trusted as saying the keypad on the good ol’ brick phones this was designed for. Model yo threats, brother!
I might find this useful at some point. Got SIM cards around that have been in use decades, PIN completely forgotten.
Though sometimes you can turn up devices that seem to have a permanent low rate data connection, alarm boxes, monitors, devices that report data, with a SIM in. Might be you could repurpose one of those.
You need to have devices around these SIM cards that still remember the PIN, otherwise this won’t help you.
Whoops, good point… though now I’m puzzling as to why these SIMs haven’t needed a PIN entry since they were installed in the original 20th century brick nokias…. though maybe we had to PUK them and SIM based security hasn’t been used since. Ppl go on about how reliable those bricks were but the damn things barfed on the SIM somehow every dozen or so months and you had to reset everything through the provider.
I have a cricket Moto G 7 Supra and I am trying to unlock the SIM I can’t seem to do it it’s getting on my nerves I don’t want to he with this company for 6 months when the phone is none and I want Google Fi. If I had any smarts like you I would’ve tried what you did. Hell in having the worst luck trying to get the sim card out of my broken j2 phone. It’s ANNOYING
Keep in mind this is a rare corner case where the PIN was embedded in the firmware of the host device.
For a phone SIM where the PIN was always entered by the user, this won’t help you.
Well, it wont unless you can get the user to enter their pin while you’re doing it.
Re: Plain Text
I had a similar discussion in a professional environment, we were discussing how to lock down RFID tags so only tags supplied by our company would work with our equipment. It seemed to be a grand idea to just define a password on the tag until we realized it’d be trivial for someone to sniff the CAN bus and find the password we’re using. It didn’t help that the RFID reader’s command set was publicly published. Oh well, onto more asinine solutions!
add a cryptographic signature of the card ID in the tag’s data area? won’t prevent duplicates, though, as there are cards where ID is rewritable.
That’s pretty much what we settled on. The idea was to hash a key into the EPC of the tag since it has 96 bits of data of which we really only need the lower half. That said, I think I’ve talked management off that cliff.
Though you could attack the cheaper versions of the rewritable cards by sending the magic sequence and erasing it.
Harder though the write once ones where they no longer Res pop one to the magic reprogramming packet.
Either way you can program an Arduino or one of the many sniffers to pretend to be that NFC card. (Usually mifare 1Ks)
The only way IIRC is to get a custom java EMV NFC type card and do some PKI … Though that would make things prohibitively expensive in comparison to mifare 1Ks :/
Would this be similar to unlocking an iPhone or ami being too dumb?
Not the same, since the iPhone request the pin-code.
He could have bruteforced it tho trying a pin twice then let it unlock by the device again, rinse repeat. But could have taken a long time 😅
It would be similar if you unlocked the iPhone by entering the passcode you previously watched the owner enter.
Is there any use of a SIM card once the corresponding suscribption has been resigned?
Not much, but in my case I just used it as a tool to get a network-locked cell phone unlocked; the phone just cares more that a SIM card that belongs to another network is inserted, regardless of whether or not it has active service.
I’m keeping some old SIMs from various providers just to be able to do that too. But i was wondering if it could be useful for anything else.
I guess if you wanted to hide data in the SIM card’s contacts/SMS storage, you could. Alternatively, you could use the GET CHALLENGE command (0x00 84 00 00 08, the 08 meaning 8 bytes), you can turn a SIM card into a random number generator.