It might be hard to imagine now, but there was a time when the average home had only a single Internet connected device in it. This beige box, known as a “desktop computer” in those olden days, was a hub of information and productivity for the whole family. There was a good chance you might even need to wait for your turn to use it, since it’s not like you had a personal device in your pocket that let you log on from the bathroom whatever room you might be in at the time. Which is just as well, since even if you had broadband back then, you certainly weren’t shooting it around the house with the Magic Internet Beams that we take for granted now.
Things are a lot more complicated today. Your computer(s) are only part of the equation. Now there’s mobile phones and tablets sharing your Internet connection, in addition to whatever smart gadgets you’ve brought into the mix. When your doorbell and half the light bulbs in the house have their own IP address, it takes more than a fresh copy of Norton AntiVirus to keep everything secure.
 Which is precisely what Cigent Technology says the Recon Sentinel was designed for. Rather than protecting a single computer or device, this little gadget is advertised as being able to secure your entire network by sniffing out suspicious activity and providing instant notifications when new hardware is connected. According to the official whitepaper, it also runs a honeypot service Cigent calls a “cyber deception engine” and is capable of deploying “Active Defense Countermeasures” to confuse malicious devices that attempt to attack it.
Which is precisely what Cigent Technology says the Recon Sentinel was designed for. Rather than protecting a single computer or device, this little gadget is advertised as being able to secure your entire network by sniffing out suspicious activity and providing instant notifications when new hardware is connected. According to the official whitepaper, it also runs a honeypot service Cigent calls a “cyber deception engine” and is capable of deploying “Active Defense Countermeasures” to confuse malicious devices that attempt to attack it.
It certainly sounds impressive. But for $149.99 plus an annual subscription fee, it better. If you’re hoping this teardown will tell you if it’s worth springing for the $899.99 Lifetime Subscription package, don’t get too excited. This isn’t a review, we’re only interested in cracking this thing open and seeing what makes it tick.
Well…That Was Easy
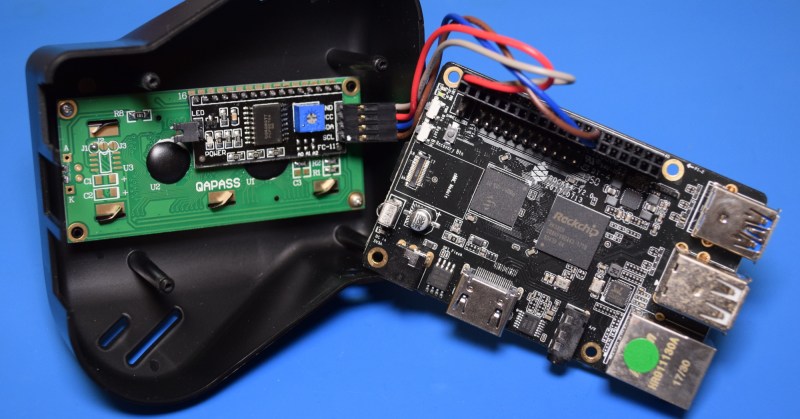
Folks, this is a first. Inside the Recon Sentinel’s oddly shaped injection molded enclosure is a ROCK64 board from Pine64 and the same I2C 16×2 LCD that we’ve all got kicking around our parts bin. That’s it. Beyond the enclosure, the only custom made component for the Recon Sentinel is the adapter cable that goes from the 40 pin Raspberry Pi style expansion header down to the four wires that connect to the display. It’s even packing a run-of-the-mill SanDisk 8 GB micro SD, at least the one in the Wonder Bible was branded.
It’s no exaggeration to say that the hardware for this product is only one step above a DIY weekend build. You could go on Thingiverse right now, find a printable case that could take this identical LCD and whatever flavor of Linux board you’re fond of, and be half-way there. Which would be fine if this was some kind of prototype, but this is what they’re actually shipping out to customers.
While calling it “easy” might be a stretch, building a single board computer (SBC) that runs Linux is now within the reach of the dedicated hacker. We’ve also seen a number of individuals create custom carrier boards for the Raspberry Pi Compute module. In short, there’s no technical reason that even a small company couldn’t pump out a custom board that would be a better fit for this application. Something with dual Ethernet interfaces would have been ideal, and there’s no reason to include USB and HDMI ports if they’re never going to be used.
That said, it looks like Pine64 was clearing out stock of the entry-level ROCK64, selling them for just $25 USD in single quantities. The Recon Sentinel might be the product of some bulk-order deal that brought the unit cost even lower. It wouldn’t be the first time one company’s fire sale lead to the creation of a new product.
Doing Recon on the Recon
We don’t normally concern ourselves with the software side of things during these teardowns, but frankly, there’s usually more hardware to look at. So in this case, it seems appropriate to take a closer look at the Linux system running inside the Recon Sentinel. Clearly that’s where all the time and effort was spent on the product anyway.
I searched online a bit and didn’t find any indication of what the root password for the Recon Sentinel is out of the box, but of course it’s not hard to gain access when you can just pop the micro SD card out. I mounted it on my desktop, wiped the hashed root password from /etc/shadow, and then replaced the sshd_config file with a minimal version that allowed root logins and blank passwords. I didn’t want it phoning home, so I plugged it into an unused wireless router that allowed it to pull a DHCP lease without getting a link to the Internet. The LCD showed an error message about connectivity, but I was able to log in over SSH with no issue at that point.
The system appears to be the standard Debian Stretch image that Pine64 distributes for the ROCK64, with the addition of some Raspbian packages. It looks like most of the custom software developed for the Recon Sentinel was developed in Python, so it’s easy to open up the files and see what its up to. There’s also a handy tool called lcd_display that allows you to push two lines of text to the screen which is used extensively throughout the system.
While it’s easy enough to pop in and poke around (and convenient that the LCD is already set up and working), there’s a few issues with the OS that make repurposing it impractical. For one thing, it appears that local logins have been disabled entirely. I also noticed that after a few minutes the device reboots, probably because it can’t connect to the Internet. Of course you could identify and undo these changes, but I think your time would be better spent wiping it and starting fresh.
Putting the Sentinel to Work
Ultimately, the Recon Sentinel may be one of most unusual commercial devices we’ve ever looked at. Sure we’ve uncovered boards we recognized before, such as the Electric Imps that are often found hiding inside of Quirky’s line of oddball IoT gadgets, but nothing quite like this. If there’s a more eminently reusable device for hardware hackers, I can’t imagine what it would be. Just wipe the SD card, do a fresh install of Debian, and you’ve got a handy little Linux box with a built in LCD display that you could use for literally anything.
In fact, some enterprising company has apparently gotten their hands on a bunch of surplus Recon Sentinels and started offloading them on Amazon as development kits. Prices seem to fluctuate, but overall it looks like you can pick one up for less than 15% of the original price. It seems like a safe bet that things aren’t going so great for the company, so personally, I’d skip the Lifetime Subscription. It’ll probably end up being a lot shorter than you hoped for.

















Run some throughput and latency tests with and without and let us know if this thing slows you down.
If I had to guess what it’s actually doing… Wait, it only has one Ethernet port? So it can’t even filter traffic!?!? I thought maybe they had a blacklist of known bad IPs, and were blocking those in real time. Really struggling to see what it’s actually doing, then.
Sounds like something similar to Pi-Hole (https://pi-hole.net/), which does nothing more than providing a filtered DNS service and a dummy webserver for unwanted, redirected host names.
And yes, for an efficient filter, the device needs two network interface. You could get away with a single network interface and a VLAN switch (like many, many home routers do), but that’s not what the developers intended.
Yeah, given most people are going to plug this into a consumer router and not something they can mirror traffic to, its not like they can do any traffic monitoring. My guess is they let it connect to the network with a bunch of unpatched services running and hope someone gets in the network and does a scan. Then they find the low hanging fruit, throw a metasploit package at it and this device detects the hack (hopefully?) and throws up an alert maybe.
Cool, it’s advertised as a plug-n-play spyware device to scan your network and upload it’s contents to some nebulous server somewhere. Just like google or alexa! Does it constantly record audio too? I guess it’s better than some freeware app you install on your phone that does the same thing but pretends to be something else.
Well, technically it could do ARP poisoning on the local switch to see all the traffic.
Either way it’s a crap solution though.
It might be using ARP poisoning to redirect all the traffic through itself.
from the description, it’s not a firewall or anything like that but just a NIDS, so no need of “multiple” ethernet port… I wonder how a NIDS like that work in our current all switched networks…
I’d assume it’s working along the lines of Disney’s circle, and running ARP poisoning to stick itself in between you and the router surreptitiously.
Wait, no detail at all on what it actually does? Sheesh. I mean my guess would be “basically nothing” but it would be nice to at least mention what those python scripts seem to do, aside from update the LCD screen. Or is that it?
Why would there be? It’s a hardware teardown, the software is inconsequential. It sounds like you need a subscription for the software to do anything anyway.
I guess I don’t see the point of a hardware teardown on something that is almost solely a software-based device. It’s just a pine64 board. The software is the only thing of consequence here at this point. This doesn’t tell us anything about what it actually does.
The software isn’t of interest to this audience, it’s just going to get wiped and replaced with straight Debian anyway.
But they didn’t know it was just a pine64 board until they performed the hardware teardown.
>I mean my guess would be “basically nothing”
This or “just” what is called telemetry today…
Can’t help, this thing makes me remember those tools (software) from the Windows 95-98 time that were advertised as increasing your RAM somehow, speed up your computer and stuff but basically did nothing except showing a fancy GUI with lots of numbers. The difference is they weren’t phoning home and the subscription thing was not yet a thing. Well…
Would be really interesting to dig into the software of this thing or at least connect it to the internet and run Wireshark to see how much telemetry it sends. Or make a test network and put Kali to work and see if the device does sth. But the company probably has lots of nasty laywers so…
Those RAM savers did work in the sense that they periodically created a large memory reservation that forced the OS to put everything to disk cache. If nothing used that stuff at the moment, then you got “free” RAM out of it because it wouldn’t instantly pull it back up. That had the minor effect that programs would load marginally faster without the OS first doing the same thing.
The other effect was basically de-fragmenting memory by forcing the OS to re-allocate everything in it. Back in the days when you only had megabytes of RAM, fragmentation was an issue because even if you had free RAM, it could be in such small pieces that the OS would have to take things down to swap anyways to make room for a new allocation. Doing this “manually” before it was actually needed made the system slightly more responsive with less swapping.
I made the entry for this on https://wikidevi.wi-cat.ru/Recon_Sentinel in October of 2019, so I’d say these have been available via clearance for over a year! Never thought to post my teardown here though.
I disagree on one point. A small company could not make something better suited. Cheaper, maybe, or maybe not. But these are standard parts that will still be usable, and actually practically usable in 25 years. They have all the extra features that a custom board would lack, but are very cheap in mass production.
Sure, those features might not be relevant here, but they will be relevant when this winds up at a thrift store.
In a decade, the custom board would be in the E-waste pile. This will not, unless something throws it there anyway for no good reason.
If it were up to me, there’d be ISO standard form factors for this kind of off the shelf module, and custom boards would mostly only be used for ultracompact things, or small add-ons for the unique functionality, controlled by the standard modules.
It’s like designing your own power supply instead of using a wall wart or USB. Not only does it cost money, and lose the mass production advantage, it makes it non-replacable by the end user, and prevents direct DC operation.
I agree axcept for the PSU part.
Todays PSUs are cheap and noisy.
Call me oldschool, but as a hobbyist I’d rather use my homebuilt PSU on a transformer basis anytime.
It might not be as efficient, but would have a fuse and it would provide clean DC without RF, ripple, voltage peaks or any other annoyances. :)
A few months ago I needed to get a Pine64 SMB. Amazon of all places had one for $7.00 and came with an odd chaped case, LCD and power supply. When it came in the mail it was a RECON SENTINEL. Played around with it and went back and ordered six more for future projects.
I purchased two of these when they were $7.99 on Amazon. I have been having fun with it using it as a Pine64 board. Some reviewers on Amazon claim that they have issues with the HDMI output. Could be that these boards are seconds but I have not run into any issues.
From what I remember (it’s been a while since I used mine,) the HDMI issue is common enough on the Rock64 that there are posts complaining about it; that might not be specific to the Recon thing.
I just picked up one of these and it’s the same as the author’s There’s no HDMI Transient Voltage Suppressors between the HDMI port and the Rock64 SOC. This open is what’s causing everyone to complain that the HDMI isn’t working. The PN that’s missing is something like this. CTLTVS5-4 TR PBFREE
Or you can short the traces together and hope for the best like what I plan on doing.
Nevermind. The traces aren’t open. It was a red herring.
So can I reuse it like a raspberry pi?
Yes. This said, you can just buy this board “standalone”. If I remember it cheaper this way.
Wow I, one of the most surprising articles I’ve read here, and that is saying something. I suppose it makes sense to implement this type of board in some cases, but I was really not expecting that.
Actually funny device. Though a bit overpriced. And I’d say you can make it actually securing your network, assuming you know Linux well. Um, well, Linux box on the way can improve network security a lot – if you do it right.
Certainly seems like it would be a good candidate to run Pi-Hole. Wonder if the project already has some support for 16×2 character LCDs like this.
Not sure what Pi-Hole is – but I’ve creates self few “network guards” that act as custom gateways and “teleporters” – and I think not just it halts unrequested network activity, it even stands chance against BIOS/UEFI/Management Engine initiated traffic, that would be well outside of “normal” OS control since it either runs before OS or side-by-side. Same applies to any network-able devices as well.
It can also enforce e.g. tor-only mode without any DNS/MAC/… leaks at all if desired. Though it surely implies some inconveniences. Long story short, idea itself haves its point. Implementation is another story.
This certainly seems oversold at best and outright scammy at worst; but because of the flimflam about the cyber-deception-engine-something-something rather than the hardware reuse.
It’s honestly pretty normal to find obviously-stock hardware(sometimes just a straight Dell or Supermicro with a custom faceplate, otherwise hardware identical to a product in their lineup; sometimes something identifiably off the shelf but a little more obscure, like Caswell) in network appliances with reasonably intimidating sticker prices(when new, often quite the bargain once out of support, since comparison shoppers often miss that they are identical to better known gear).
And honestly that doesn’t seem like a problem: it takes considerable volume(or the need for specific accelerator ASICs or similar) before a vendor whose expertise is in software can do better with a custom board than they can with a readily available board from someone who actually knows how to do hardware; and it certainly makes repurposing easier.
This won’t work if they have a Recon Sentinel Busta.
You’ll need to also use a Recon Sentinel Busta Busta.
I just ordered a couple of these from the Amazon link in the article for $17.99. It looks like all they did was pull the cardboard sleeve off the box and ship it. It still had the setup pamphlet inside for the Sentinel. Mine came with a 16gb sd card.
Armbian + a whole bunch of scrips with “(c) 2003-2016 CORE Security Technologies” in the header, port scan scripts, windows reg scan & hash grab scripts, some LCD scripts & executables, HDMI on/off, etc….mostly sh & py.
Save off the hardware management ones for LCD & HDMI and so on, start over with a clean OS (dietpi runs nicely) and have fun.