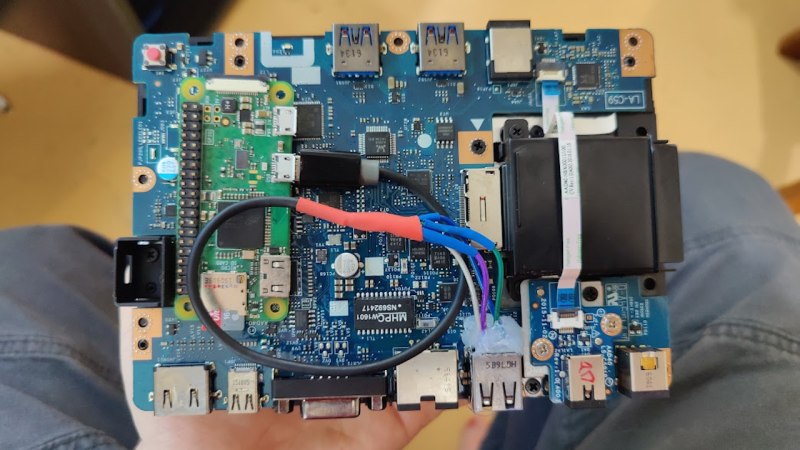
In today’s installment of Betteridge’s law enforcement, here’s an evil USB-C dock proof-of-concept by [Lachlan Davidson] from [Aura Division]. We’ve seen malicious USB devices aplenty, from cables and chargers to flash drives and even suspicious USB fans. But a dock, however, is new. The gist is simple — you take a stock dock, find a Pi Zero W and wire it up to a USB 2.0 port tapped somewhere inside the dock. Finding a Pi Zero is unquestionably the hardest part in this endeavor — on the software side, everything is ready for you, just flash an SD card with a pre-cooked malicious image and go!
On the surface level, this might seem like a cookie-cutter malicious USB attack. However, there’s a non-technical element to it; USB-C docks are becoming more and more popular, and with the unique level of convenience they provide, the “plug it in” temptation is much higher than with other devices. For instance, in shared workspaces, having a USB-C cable with charging and sometimes even a second monitor is becoming a norm. If you use USB-C day-to-day, the convenience of just plugging a USB-C cable into your laptop becomes too good to pass up on.
This hack doesn’t exactly use any USB-C specific technical features, like Power Delivery (PD) – it’s more about exploiting the convenience factor of USB-C that incentivizes you to plug a USB-C cable in, amplifying an old attack. Now, BadUSB with its keystroke injection is no longer the limit — with a Thunderbolt-capable USB-C dock, you can connect a PCIe device to it internally and even get access to a laptop’s RAM contents. Of course, fearing USB-C cables is not a viable approach, so perhaps it’s time for us to start protecting from BadUSB attacks on the software side.















“Buy Now” is a suggestion. The button doesn’t actually do anything.
>Of course, fearing USB-C cables is not a viable approach,
I’d suggest it really is! USB-C is so much more hazardous than regular USB and you shouldn’t be using strange ones of those really! That whole ‘trust but verify’ type concept really should apply, don’t know where this cable/drive whatever came from so don’t actually trust it until you have tested it as best you can. Might even be packed with explosives…
More software protections would I think be rather difficult to do without rendering the entire computer practically unusable – especially with all the negotiation events PD can lead too and the number of USB devices that in normal operation change modes or reset periodically… Popup box the nth in the last 2 mins, ‘device x changed status y. USB stack in lockdown mode, all current operations cancelled – unlock?’. Just how long do you think people would last before turning the protection stuff off as it is making their life impossible! In the same way most folks aware enough that websites are full of potentially mallicious scripts might run browser plugings to stay safer. For perhaps a whole min on any particular website before it being completely broken leads them to turn the scripts back on… You can’t fix inherent physical security and hardware problems in software effectively most of the time – those are back to the drawing board make the next revision of your security practices or hardware tougher.
And in the case of PD what protection can you offer in software! The hub or its internal parasite decides it is malicious and dumps whatever the max power it can source is down the power pins – nothing the computers software can do about that, either the hardware can take that abuse or it fries. And unlike the massive capacitor dump approach that can work on regular USB sometimes a PD device is potentially in an entirely different league of power delivery while still being entirely in spec – it can likely do more harm than the capacitor dumping method while being able to operate entirely normally, until the negotiation is not listening to the device in question as it turns hostile…
Oh come on, it’s you again with your wild ‘summaries’ of USB-C =D
> More software protections would I think be rather difficult to do
Nope, there’s quite convenient routes like whitelisting/blacklisting through user interaction, *and*, PD doesn’t add attack surface to BadUSB in any “especially” way, those are handled at way lower level than the BadUSB needs to operate. The way you describe your hypothetical software protections, indeed, intrusive, which is why it makes no sense to implement things the way you describe – there’s other ways, with way better UX and smarter heuristics as opposed to ask-on-literally-everything, and I urge you to take a look at actual BadUSB vectors. As it stands, it’s trivial to implement whitelisting for new input devices and network adapters in a higher-security environment, and even for laptops it’s not much of a hassle. Also, I know people who run no-script as a rule, and they have their own ways to approach script-less operation, that don’t lead to the frustration you describe.
> dumps whatever the max power it can source is down the power pins
Think I didn’t consider this angle? =D If you’re adding an implant to the dock, you can literally add a FET to the USB-A port’s VBUS from the dock’s power input – and unlike USB-C, feeding 20V into the USB-A VBUS is guaranteed to fry your stuff. Hell, if you’re doing an implant and you want to kill the computer in question, you can literally just add a USB killer onto the data rails, like the article suggests. That’s why I didn’t add such a sentence/two into the article after thinking it through for a fair bit.
This is nothing against USB-C – its against ALL such unknown devices and cables! You shouldn’t blindly trust any of them! As recently reported with some USB sticks packed with explosives targeting journalist.
USB-C does makes the situation somewhat worse than regular USB with no PD – as USB-C can be PCIe, the devices often will be full of many hub like chip parts (so the output of lsusb won’t flag that this one as suspicious as easily – the one device is expected to have many things built in), and it can dump heaps of sustained power entirely legally. So your bad USB-C cable between a good device and PD power source COULD easily man in the middle, which is something you can’t do with regular 5V only USB. Not saying you can’t maliciously abuse the 5v only stuff, just that being able to dump super high voltage for 100w delivery is rather easier.
Any attempt to protect such a plug and play bus with devices that are very mutable in their own right either HAS to ask on every change or WILL miss many malicious changes. A whitelist is pretty pointless as its not hard to pretend to be a whitelist device, or trick the user into whitelisting the malicious device – this hub you just connected intentionally has ports for everything, reports it has HID and networking. Which means you are expecting the prompt, so when the software asks you hit OK. The protection offerable in software has to be comparatively low for computer operation to not become impossibly annoying.
And I myself do run mostly script-less, and it really is a massive annoyance at times as vast amounts of the web are entirely broken without the scripts. The techie user can manage this, turn on the sources of only the scripts they absolutely must have. But 99% of users won’t be doing that, and most of those that know enough to concerned about the security still won’t be cherry picking. It is a substantial amount of extra effort just to get the page to load the bit they need, and actively impossible to avoid scripts you don’t like anyway if you must use certain websites… So the first thing most users are going to do is moan at tech support to fix it or know enough to turn it off themselves.
“This is nothing against USB-C – its against ALL such unknown devices and cables! You shouldn’t blindly trust any of them! As recently reported with some USB sticks packed with explosives targeting journalist. ”
Back in the day it would have been serial port bombs with power to spare.
The more I think on it the worse USB-C looks for this sort of malicious intent and being hard to spot. Old USB or Serial generally one device per port, one function per device, everything input/output from one device that needs action on another ALWAYS goes through the host devices CPU, with fairly stable/predictable power draw in use. But as that one USB-C dock is expected to have so very much on it, and not all functions will be powered all the time its in use its just a huge mess to actually notice its bad.
And as perhaps the most common use beyond basic charging is connecting a portable into your display and desk setup.. So the dock has all the hardware on it including stuff like it may well be your Ethernet link, probably has the keyboard and mouse plugged in – that is a direct ability to dump everything you are sending to your display and all your HID inputs straight to the the internet with the computer not even knowing its happening.
You would be entirely reliant on your network security raising eyebrows and looking into it, which doesn’t apply if its a convient hub out in the wilderness. And spotting it at all, even under ideal home network situations doesn’t seem very likely either – Too many folks doing the remote meeting video link and the like that high traffic in the out direction isn’t a flag in and of itself, and the destination those packets are addressed to isn’t likely to be enough of a redflag either. Not to mention a little openCV processing and you can just send tiny burst containing all the important details and none of those repeat frames or youtube videos they are watching.
The USB-C docking world of everything on one big dongle hub external of the device just means the device can’t even know what the dongle is doing with all the data it has – as long as it continues to pretend to be a plain and simple display, USB-hub etc. So you really should be way way more paranoid about USB-C docks than other devices, as entirely be design they have everything they need to be really malicious and not tip their hand to the user.
“as long as it continues to pretend to be a … USB-hub”
It is a hub. A hub with several other devices hanging off of it: A display adapter, an Ethernet adapter, etc.
The problem is, you don’t know what “etc” includes, because it’s hidden inside the unit.
Of course, there could be unknown devices hidden inside what otherwise appears to be just a hub.
So, we all need a pile of Raspberry Pis to check all of our USB devices and cables before connecting to our PCs.
>So, we all need a pile of Raspberry Pis to check all of our USB devices and cables before connecting to our PCs.
Nice idea, but much as I love a Pi none of the currently available ones are able to test and verify that many USB-C devices directly. I think the best price currently available device that can test most USB-C things at least is the Steamdeck. Though I’d hope there are cheaper and more capable options out there I don’t know what they are… USB-C with all these potential to use for hostile reasons alt-modes is still a bit too new for there to be lots of lower end cheap stuff that can do it all, and actually finding out what a devices USB-C port can actually do isn’t always easy before purchase either… Some Phones might be a good choice if you can get them to run a real OS…
And while you can try and be cunning and test in place with external monitoring for which a Pi can be handy it still can’t do it all on its own. Maybe a Pi can manage many of those with the extra hardware, and it can certainly be the data gathering and collating computer).
This! And your first comment!!
In the last 25 years, I’ve found it harder and hard to mitigate the risks of devices vs my desired threat posture. It used to be I could head down to ye old device manufacturer for a day or two and follow my part through the manufacturing process. I mean I still found to need to remove some to most of the ICs. I was booted from my favorite IC manufactures site in the early ’80s, but I’ve found that with a little Si, Ge, Sb, P, As, B, Ga, and In I can fairly easily be certain what my (un)IC do. Usually. when I work past sundown I find I don’t always notice when I’ve connected the wrong leads, but at least that presents a threat surface so bespoke as to meet my security needs.
I’m currently working on getting my mm fab process down to at least 500μm. I’m actually having more trouble getting the constituent wafer layers sputtered on the die with a consistent depth. I think having to work with such large chips is the primary issue in the area, and I’m hoping the transition to μm will reduce the issue. If it doesn’t, then it’s back to the flint quarry and calcium carbonate mine to work out a new process.
I did need to find new Cu and Au veins anywho, so maybe a supply run is just what I need to clear my mind.
Security these days is harder than hand quarrying marble for materials. SMH.
Long live the barrel jack! Center-negative of course.
Well, if you don’t trust the USB dock at your local coworking flex-desk.. there is an easy solution. Bring your own.
If you don’t trust your own USBC dock either?
Well then you are completely out of luck, since you probably got it at the same place where you got the laptop.. if you where a malicious actor, would you place this in the dock, or the laptop itself?
Just as if it wasn’t possible to do the same hack with more classical docking stations…
I’m surprised we haven’t seen more malicious mains plug sockets. They are coming fitted with usb charging ports, more and more these days. It wouldn’t take much to have the data cables shared between ports or even a wireless single board computer built in.
They are actually out there commonly with USB now?!?! I know I’ve seen such things exist but I’ve never seen one in the wild. Doesn’t seem like a sane thing to me either – most buildings tend to have sockets way down near the floor or even in the floor, you want your USB device on your desk more often than not…
Some places, yes. Often transportation like trains and airports where you may want to use a mobile device.
I don’t understand why in the proof-of-concept you would use a Pi Zero, it’s slow because it has to boot Linux. A Pico would be a far better choice.
Where will you get a “pre-cooked malicious image” that will run on an RP2040?
Most people don’t connect a host powered USB-C Dock then disconnect immediately but I’d also guess that an awful lot of workplaces (like mine, we’ve got nearly 400) have permanently powered docks on desks ready and waiting for users to sit and connect their device so boot times are irrelevant.
..And just watch every company ban them because their cyber sec person,- with their certificate in reading articles and CVE’s from some no name school and there is nothing you can do except work there for a year and job hop to next clown installment.
Buy. Buy more now. Buy… and be happy.