The RADIUS authentication scheme, short for “Remote Authentication Dial-In User Service”, has been widely deployed for user authentication in all sorts of scenarios. It’s a bit odd, in that individual users authenticate to a “RADIUS Client”, sometimes called a Network Access Server (NAS). In response to an authentication request, a NAS packages up the authentication details, and sends it to a central RADIUS server for verification. The server then sends back a judgement on the authentication request, and if successful the user is authenticated to the NAS/client.
The scheme was updated to its current form in 1994, back when MD5 was considered a cryptographically good hash. It’s been demonstrated that MD5 has problems, most notably a chosen-prefix collision attack demonstrated in 2007. The basis of this collision attack is that given two arbitrary messages, it is possible to find a pair of values that, when appended to the end of those messages, result in matching md5 hashes for each combined message. It turns out this is directly applicable to RADIUS.
The attack is a man-in-the-middle, but not against an authenticating user. This attack is a man-in-the-middle between the NAS and the RADIUS server, and a real user isn’t even required. This elevated position does make an attack harder to achieve in some cases, but situations like RADIUS providing authentication for administrative access to a device is squarely in scope. Wrapping the RADIUS backend communications in a TLS layer does protect against the attack.
Gitlab
It’s once again time to go update your Gitlab instances, and this one sounds familiar. It’s another issue where an attacker could run pipeline jobs as an arbitrary user. This comes as one more of a series of problems in Gitlab, with at least one of them being exploited in the wild. It’s not surprising to see a high-visibility vulnerability leading to the discovery of several more similar problems. With this latest issue being so similar to the previous pipeline problem, it’s possible that it’s actually an incomplete patch or additional workaround discovered to exploit the same issue.
Exim
There’s a bug in the Exim email server, that impacts the processing of attachment blocking rules. Specifically, the filename in the email header is broken into multiple parts, with some confusing extra bytes in between. It’s technically compliant with the right RFC, but Exim’s mime handling code gets confused, and misses the right message name.
Exim server can be configured to block certain file types, and this vulnerability allows those blocked attachments through. The original CVSS of 9.1 is a tad insane. The latest update drops that to a 5.4, which seems much more appropriate.
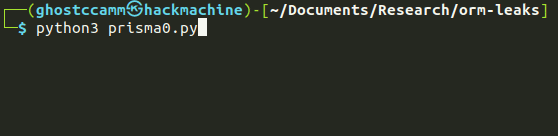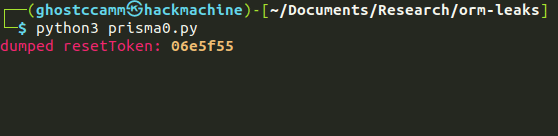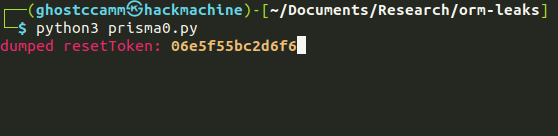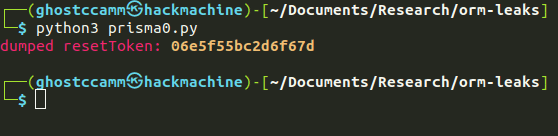
Plormbing Your ORM
Prisma is a “Next Generation ORM (Object Relational Mapper), that takes database schema, and maps it to code objects. In other words, it helps write code that interacts with a database. There’s some potential problems there, like using filters on protected data, to leak information one byte at a time, in a very Hollywood manner.
This brings us to a second approach, a time-based data leak. Here a SQL query will execute slowly or quickly depending on the data in the database. The plormber tool is designed to easily build attempts at time-based leaks. Hence the pun. If you have a leak in your ORM, call a plORMber. *sigh*
Internet Explorer Rises Again
When Microsoft finally obsoleted Internet Explorer in 2022, I had some hope that it wouldn’t be the cause of any more security issues. And yet here we are, in 2024, talking about an exploitation campaign that used a 0-day in Windows to launch Internet Explorer.
A very odd file extension, .pdf.url, manages to appear as a pdf file with the appropriate icon, and yet opens IE when executed. This finally got classified by Microsoft as a vulnerability and fixed.
Bits and Bytes
There’s another SSH issue, related to regreSSHion. This time a vendor patch makes a call to cleanup_exit() from a signal handler function, calling more async-unsafe code. If that doesn’t make any sense, circle back around to last week’s installment of the column for the details. This time it’s Fedora, Red Hat, and other distros that used the patch.
One of the security barriers that most of us rely on is that traffic originating from the WAN side of the router should stay there. When that paradigm breaks down, we have problems. And that’s exactly what the folks at Claroty are working to defeat. The trick this time is a vulnerability in a router’s Dynamic DNS service. Manage to spoof a DNS lookup or MitM that connection, and suddenly it’s RCE on the router.
And finally, we’ve covered a pair of outstanding stories this week here at Hackaday. You should go read about how Ticketmaster’s app was reverse engineered, followed by a brilliant and completely impractical scheme to get your Internet connection for free while flying.
















> It’s a bit odd, in that individual users authenticate to a “RADIUS Client”, sometimes called a Network Access Server (NAS).
I think you got it backwards. Network Access Server is something that end users connect to. Imagine a dial-up service. The users provide their names and passwords to gain access to the network. Uploading data of each and every user to each and every Network Access Server is not feasible nor secure now and definitely wasn’t in the nineties [1]. So instead, the Network Access Servers delegated authentication to a central RADIUS server. Since Network Access Servers contacted RADIUS server, in terms of RADIUS protocol they were clients, obviously.
[1] I worked in a local ISP with a hundred users and a single Livinston Portmaster, but I imagine that nation-wide ISPs could have millions of users and thousands of NASes.
Yeah, that’s what I was trying to describe. The naming convention makes it difficult.
In the Plormbing snippet: What’s that symbol after ghostcamm (presumably an “@”) and how do you get it to look that cool in a terminal?
I hope it’s more than just the old “hack teh font so [common character] looks really cool” trick. But if it is, hat’s off to the creator for sheer hack-simplicity.
Huh. Password slot machine channeling the Library of Babel. Certainly didn’t have that on my 2024 bingo card.
RADIUS is one of those old legacy security protocols that should of been retired years ago, but clings on because it is the lowest common denominator.
We were “encouraged” to go that way some years ago to provide a centralised user authentication, but it has been nothing but a pain. For example it has no concept of role, meaning we needed to extend ours, which of course means it is now not compatible
In terms of solutions, dTLS would require some manner of key distribution service, so is not suitable for many applications. Adding a key in the Attribute to support HMAC-MD5 would again make it non-compliant with 3rd party implementations
The major issue with all those is that any RADIUS client/server would still be FIPS140-2 non-compliant meaning it would be banned from US government usage, since MD5 is a prohibited hashing algorithm and just having openssl with MD5 included makes PC’s not suitable