Ever wanted to sniff USB device communications? The usual path was buying an expensive metal box with USB connectors, using logic analyzers, or wiring devboards together and hacking some software to make them forward USB data.
Now, thanks to [ataradov]’s work, you can simply use a Pi Pico – you only need to tap the D+ and D- pins, wire them to RP2040’s GPIOs, and you can sniff communication between your computer and any low-speed (1.5 Mbps) or full-speed (12 Mbps) devices. On the RP2040 side, plug the Pico into your computer, open the virtual serial port created, and witness the USB packets streaming in – for the price of a Pico, you get an elegant USB sniffer, only a little soldering required.
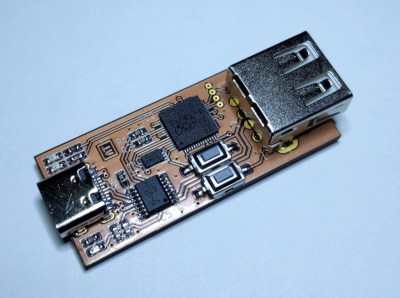 [ataradov] also offers us a complete board design with a RP2040 and a USB hub on it, equipped with USB sockets that completely free us from the soldering requirement; it’s an open-source KiCad design, so you can simply order some sniffers made from your favourite fab! This project is a great learning tool, it’s as cheap and easy to make as humanly possible, and it has big potential for things like reverse-engineering old and new systems alike. Just couple this hack with another Pico doing USB device or host duty, maybe get up to date with USB reverse-engineering fundamentals, and you could make a Facedancer-like tool with ease.
[ataradov] also offers us a complete board design with a RP2040 and a USB hub on it, equipped with USB sockets that completely free us from the soldering requirement; it’s an open-source KiCad design, so you can simply order some sniffers made from your favourite fab! This project is a great learning tool, it’s as cheap and easy to make as humanly possible, and it has big potential for things like reverse-engineering old and new systems alike. Just couple this hack with another Pico doing USB device or host duty, maybe get up to date with USB reverse-engineering fundamentals, and you could make a Facedancer-like tool with ease.
Need to reach 480 Mbit/s? [ataradov] has a wonderful board for you as well, that we have covered last year – it’s well worth it if a device of yours can only do the highest speed USB2 can offer, and, it offers WireShark support. Want WireShark support and to use a Pico? Here’s a GitHub project by another hacker, [tana]. By now, merely having a Pi Pico gives you so many tools, it’s not even funny.
We thank [Julianna] for sharing this with us!















Small correction: Low-speed USB is 1.5Mbps, not 1.2Mbps.
https://en.wikipedia.org/wiki/USB#USB_1.x
Several years ago I also did a short experiment with Sigrok / Pulseview and the USD 5 Saleaeae clone and capturing low speed USB worked. Combined with the built in USB decoders in Pulseview / Sigrok it showed an amazing variety of low level details of the USB protocol. From T states and checksums to keep alive packets and meanings of other types of packets. This is extremely nice if you want to study how USB actually works. And all of course captured with the timing accuracy / resolution that is expected of a logic analyzer.
Ben Eater also has some nice video’s of low level USB protocols, inclusive decoding with a nice scope.
I would really like to see some more life in Sigrok / Pulseview. Progress is going extremely slow for the last few years. But I don’t know what to do here. Due to… personal things I can’t focus anymore on programming or other attention demanding tasks.
Yes, Sigrok/Pulseview would benefit from more attention and more developpers. Last time i tried it wasn’t even possible to register to the bug tracker (something in the backend must be broken)… For myself i have a huge pile of projects that i *really* need to get done, but maybe one day i will be able to help.
With a ~40€/USD Saleae 16 clone (i.e. one with a tiny FPGA), you can also sample 2 channels @ 50 MS/s (max: ~3 channels @ 100, or 6 @ 50), which gives you the required resolution for 12 Mbit/s (USB FS).
Sigrok-cli also allows to feed the decoded data directly into TShark (CLI) or Wireshark, using a named pipe.
thank you, fixed!
Why would you use such hardware, instead of running Wireshark with USBPcap? The only use case I can think of is USB OTG, but even that would imply a reasonably powerful microcontroller that could probably just log the traffic internally.
-reverse engineering/glitching/side-channel-attacks
-debugging USB stacks and stuff like this (sounds fun…)
-completly custom/closed hardware where you can’t install Wireshark (does this even work on Windows?)
-…
USBPcap is fine when everything works, such as when reverse-engineering the protocol of an existing device. But when your own device doesn’t work, operating system level USB captures will just show “request timeout” or similar, no matter what really happened.
As mentioned before, this only works if your device already works. If you are writing microcontroller firmware for an USB device and your PC does not even recognize your uC because the handshaking fails then wireshark is of no use.
Exactly. I once found out using a USB sniffer that the JZ4730 USB host violates the spec by not resetting the error counter when tokens are received without CRC errors. In Linux all you could see was that IN URBs aborted very quickly even when the device (USB serial adapter) had no reason to return any data.
This is really interesting!
Yes!
Please ping me when there will be a batch produced.
Are there any BOM and CPL files?
How can i order it assembled from a fab service like JLCPCB or similar?
You get the KiCad sources so you can output any file you need, plus, look in the repo, it could have JLC files already!
I don’t see JLC files in the repo, but i will try to export them from KiCad + the appropriate plugin for JLC, with the project loaded.
I just hope they will have the part numbers as per the JLC catalog after that, so there are no extra fees for components.
Thanks for your work!
Got it, thanks!
While USB sniffing has been possible for a while, the now obsolete Firewire interface remained pretty inaccessible. There was CATC FireInspector hardware capture, but limited to FW400. And there is Bus Hound software, but limited to Windows. Wireshark doesn’t even support decoding IEEE 1394 protocol.
Wondering if the pre-made “Adafruit Feather RP2040 with USB Type A Host” could not be used with minimal software change.
It is already used for USB HID Remapper https://github.com/jfedor2/hid-remapper
just adding the HID remapper project is awesome, as shown. The developer has even time to reply to me helping me make the web interface local, and I know such a little about this.
I now have a game mouse that does what I what with no bloatware.
Nothing to do with this project as such but if it helps someone cut the year or trying to do this myself and looking for Low Cost USB sniffers I am happy to add this. (I got so lost with Wireshark and I used to use that at work (I have forgotten so much) . Would the sniffer here help, well I sure as heck would have tried
Please add the “Raspberry Pi Pico” tag. Hackaday makes it really hard to find projects by tag.
done, thank you for reminding! WP’s tag system is quite uncomfortable to use, especially with the amounts of tags we have by now, sadly
Thank you as well!