[Mariano] owns a late 90’s Jeep Wrangler, and had no idea just how easy it was to steal. Unfortunately for him, the guy who made off with his Jeep was well aware of the car’s vulnerabilities. The problem lies in the ignition – it can be broken out with a screwdriver, after which, the car can be started with a single finger. How’s that for security?
[Mariano] decided that he would take matters into his own hands and add a remote-controlled switch to his car in order to encourage the next would-be thief to move on to an easier target. He describes his creation as a “remote kill” switch, though it’s more of a “remote enable” switch, enabling the engine when he wants to start the car rather than killing it on command.
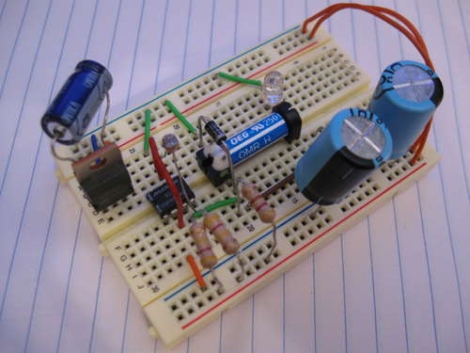
The switch system is made up of two pieces – a server inside the car’s engine bay, and a remote key fob. The server and the fob speak to one another using IPv6 over 802.15.4 (the same standard used by ZigBee modules). Once the server receives a GET request from the key fob, it authenticates the user with a 128-bit AES challenge/response session, allowing the car to be started.
It is not the simplest way of adding a remote-kill switch to a car, but we like it. Unless the next potential car thief digs under the hood for a while, we’re pretty sure [Mariano’s] car will be safe for quite some time.