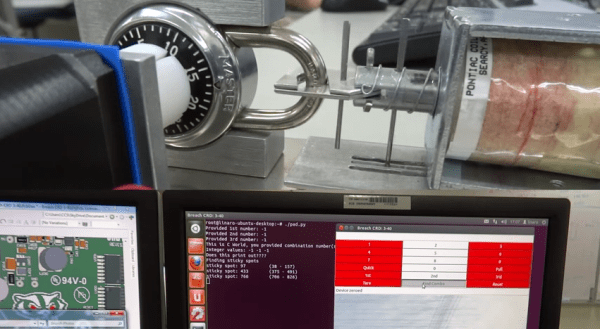
We love the beginning of May because the final projects for college coursework start rolling into our tips line. Here’s one of the latest, it’s an automatic Master lock combination cracker which was built by [Ross Aiken] and his classmates as part of their ECE453 Embedded Microprocessor System Design class at the University of Wisconsin – Madison.
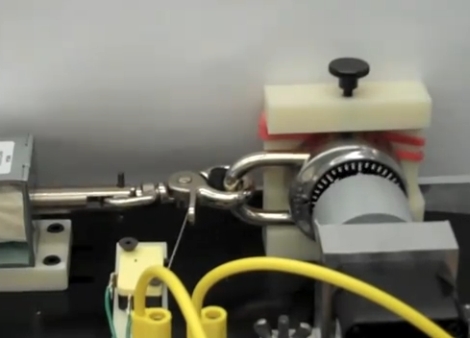
We’ve talked about the ease with which these locks can be cracked. But [Ross] points out that the resources we linked to before are flawed. To get the combination as quickly as possible the team has implemented an algorithm discussed here. Their machine uses a stepper motor to turn the dial with a big solenoid to pull on the shackle. The system is sensitive enough to detect the “sticky” spots of the lock, which are then used to narrow the number of possible combinations before brute forcing the combination. As you can see in the video after the break, the shackle moves slightly when pulled after an incorrect combination. The long vertical pin near the solenoid will pass through an optical sensor when the correct combination is found.
Do you have your own final project to show off? What are you waiting for, send us a tip about it!
Continue reading “Master Lock Auto-cracker Built As Coursework At University”