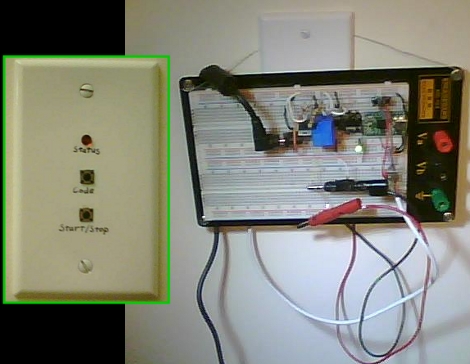
[over9k] used his Arduino to set up a laser trip wire. The laser is mounted along side the Arduino, reflects off of a mirror, and shines on a photoresistor that interfaces via a voltage divider. The signal from the voltage divider is monitored for a change when the laser beam is broken. [over9k] set things up so that a webcam snaps a picture of the intruder and Twitters the event for easy notification. Video after the break walks through each of these steps.
This build is a bit rough around the edges but unlike other laser trip wires this keeps all the electronics in one place. The laser interface could be a bit more eloquent, and we’re wondering just how much current it is pulling off of the Arduino pins. But if you’re bored and have this stuff on hand it will be fun to play around with it. Continue reading “Arduino Security With Frickin’ Laser”