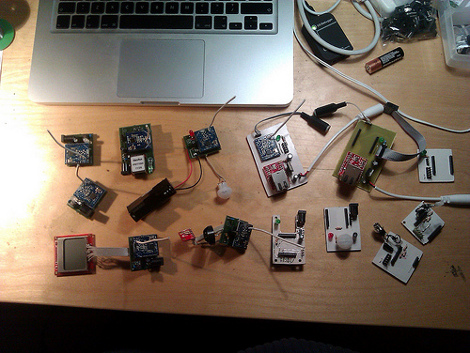
Ever wonder what happens to those digital price tags you see in stores once they run out of juice? In what is a prime example of e-waste, many of those digital price tags are made with non-replaceable batteries, so once their life is over they are discarded. Seeing an opportunity to breathe new life into these displays, [Tylercrumpton] went about converting them to be the official badge of the Phreaknic 26 conference.
Looking for a solution for a cheap display for the upcoming conference badge, [Tylercrumpton] recalled seeing the work [Aaron Christophel] did with reusing electronic shelf labels. Looking on eBay, he picked up a lot of 100 ZBD 55c-RB labels for just $0.70 a piece. When they arrived, he got to work liberating the displays from their plastic cases. The long-dead batteries in the devices ended up being easily removed, leaving behind just the display and the PCB that drives it.
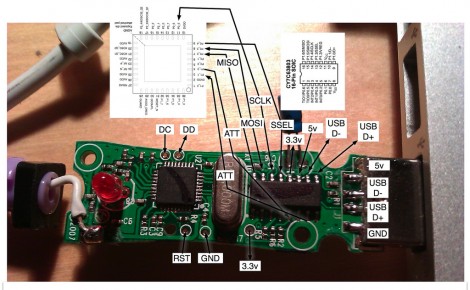
 Another hacker assisting with the badge project, [Mog], noticed that the spacing of the programming pads on the PCB was very close to the spacing of a DB9/DE9 cable. This gave way to a very clever hack for programming the badges: putting pogo pins into a female connector. The other end of the cable was connected to a TI CC Debugger which was used to program the firmware on the displays. But along the way, even this part of the project got an upgrade with moving to an ESP32 for flashing firmware, allowing for firmware updates without a host computer.
Another hacker assisting with the badge project, [Mog], noticed that the spacing of the programming pads on the PCB was very close to the spacing of a DB9/DE9 cable. This gave way to a very clever hack for programming the badges: putting pogo pins into a female connector. The other end of the cable was connected to a TI CC Debugger which was used to program the firmware on the displays. But along the way, even this part of the project got an upgrade with moving to an ESP32 for flashing firmware, allowing for firmware updates without a host computer.
The next challenge was how to handle customizing 200 unique badges for the conference. For this, each badge had a unique QR code embedded in the back of the 3D printed case that pointed to an online customization tool. The tool allowed the user to change which of the images was used for the background, as well as input the name they wanted to be displayed on the badge. Once finished, the server would provide a patched firmware image suitable for flashing the badge. The original intent was to have stations where attendees could plug in their badge and it would update itself; however, due to some 11th hour hiccups, that didn’t pan out for this conference. Instead, [Tylercrumpton] ran the update script on his machine, and it gave him a great opportunity to interact with conference attendees as they stopped by to update their badges.
For the Phreaknic 27 badge, the plan is to once again use electronic shelf labels, but this time to utilize some of the advanced features of the tags such as the EEPROM and wireless communications. We’re eager to see what the team comes up with.
Continue reading “Shelf Life Extended: Hacking E-Waste Tags Into Conference Badges”