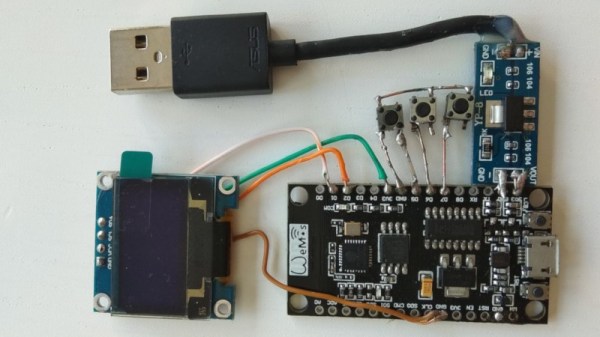
WiFi is one of those technologies that most of us would have trouble living without. Unfortunately, there are several vulnerabilities in the underlying 802.11 standards that could potentially be exploited. To demonstrate just how simple this can be, [] developed the ESP32 Wi-Fi Penetration Tool that runs on cheap dev boards and can execute deauthentication and Denial of Service attacks, and capture handshakes and PMKIDs.
The main challenge in this project is to implement these attacks while using the ESP-IDF development framework. The closed source WiFi libraries of the ESP-IDF block specific arbitrary frames like deauthentication frames. To get around this [] used two different approaches. The first is to bypass the declaration of the blocking function at compile-time, which is borrowed from the esp32-deauther project. The second approach doesn’t require any modifications to the ESP-IDF. It works by creating a rogue access point (AP) identical to the targeted access point, which will send a deauthentication frame whenever one of the devices tries to connect to it instead of the real AP.
WPA/WPA2 handshakes are captured by passively listening for devices connecting to the target network, or running a deauth attack and then listening for when devices reconnect. PMKIDs are captured from APs with the roaming feature enabled, by analyzing the first message of a WPA handshake. ESP32 Wi-Fi Penetration Tool will also format the captured data into PCAP and HCCAPX files ready to be used with Wireshark and Hashcat. To manage the tool, it creates a management access point where the target and attack type is selected, and the resulting data can be downloaded. Pair the ESP32 with a battery, and everything can be done on the go. The project is part of []’s master’s thesis, and the full academic article is an educating read. Continue reading “WiFi Penetration Testing With An ESP32”