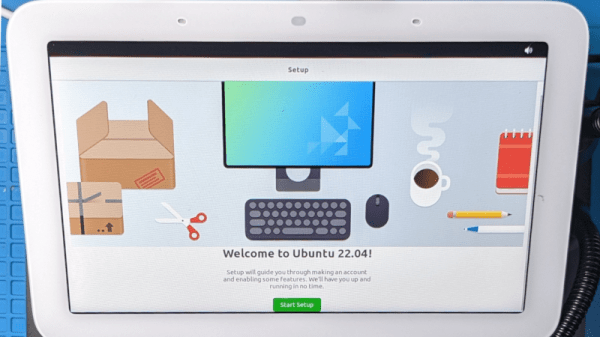
[frederic] tells a story about their team’s hack of a Google Nest Hub (2nd generation) — running Ubuntu on it, through bypassing Google’s boot image signature checks. As with many good hacks, it starts with FCC website pictures. Reverse-engineering a charger and USB daughterboard pin-out, they found a UART connection and broke it out with a custom adapter. With a debug console and insights into the process, they went on hacking, slicing through hardware and software until it was done with.
This story gives plenty of background and insight into both the code that was being investigated, and the way that attack targets were chosen. Through fuzzing, they found a buffer overflow in the bootloader code that could be triggered with help of a non-standard block size. USB flash drives tend to have these hard-coded, so they built a special firmware for a Pi Pico and shortly thereafter, achieved code execution. Then, they hooked into uboot functions and loaded Ubuntu, bypassing the boot image signature checks.
This is a wonderful documentation of a hacking journey, and an exciting read to boot (pun intended). The bug seems to have been patched for half a year now, so you probably can’t flash your Google Nest into Ubuntu anymore. However, you might be able to run an up-to-date Linux on your Amazon Echo.
We thank [Sven] for sharing this with us!