A moment’s inattention is all it takes to gather the information needed to make a physical copy of a key. It’s not necessarily an easy process, though, so if pen testing is your game, something like this Flipper Zero key copying toolchain can make the process quicker and easier when the opportunity presents itself.
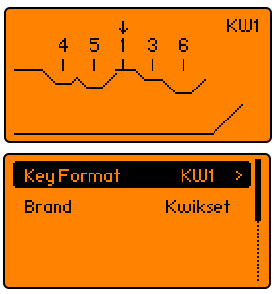 Of course, we’re not advocating for any illegal here; this is just another tool for your lock-sports bag of tricks. And yes, there are plenty of other ways to accomplish this, but using a Flipper Zero to attack a strictly mechanical lock is kind of neat. The toolchain posted by [No-Lock216] starts with an app called KeyCopier, which draws a virtual key blank on the Flipper Zero screen.
Of course, we’re not advocating for any illegal here; this is just another tool for your lock-sports bag of tricks. And yes, there are plenty of other ways to accomplish this, but using a Flipper Zero to attack a strictly mechanical lock is kind of neat. The toolchain posted by [No-Lock216] starts with an app called KeyCopier, which draws a virtual key blank on the Flipper Zero screen.
The app allows you to move the baseline for each pin to the proper depth, quickly recording the bitting for the key. Later, the bitting can be entered into an online app called keygen which, along with information on the brand of lock and its warding, can produce an STL file suitable for downloading and printing.
Again, there are a ton of ways to make a copy of a key if you have physical access to it, and the comments of the original Reddit post were filled with suggestions amusingly missing the entire point of this. Yes, you can get a key cut at any hardware store for a buck or two that will obviously last a lot longer than a 3D printed copy. But if you only have a few seconds to gather the data from the key, an app like KeyCopier could be really convenient. Personally, we’d find a smartphone app handier, but if you’ve got a Flipper, why not leverage it?
Thanks to [JohnU] for the tip.



 What you see here is a Raspberry Pi shoehorned into a power strip. The idea is to
What you see here is a Raspberry Pi shoehorned into a power strip. The idea is to