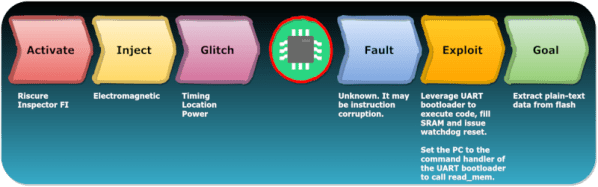
The RP2350 has a few advantages over its predecessor, one of which is the ability to load firmware remotely via UART, as [Thomas Pfister] has documented on his blog and in the video below.
[Thomas] had a project that needed more PWM than the RP2350 could provide, and hit upon the idea of using a second RP2350 as a port expander. Now, one could hard-code this, but dealing with two sets of firmware on one board can be annoying. That’s where the UART bootloader comes in: it will allow [Thomas] to program the port-expander RP2350 using the main microcontroller. Thus he only has to worry about one firmware, speeding up development.