The proliferation of FPV drones has brought a flood of cheap wireless video tech. After flying and crashing a cheap FPV drone for a bit, [GreatScott] decided to try his hand at building his own video transmitter, which turned out to be a lot harder than expected.
While digital technology has caught up to the FPV world, a lot of systems still use analog video, especially for drone racing. The video quality isn’t great, but it has the advantage of very low latency. The technology is very similar to the old analog TV broadcasts, but mainly uses the 5.8 GHz license-free bands. It is essentially analog video signal, frequency modulated onto a 5.8 GHz carrier signal transmitted through an appropriately sized antenna.
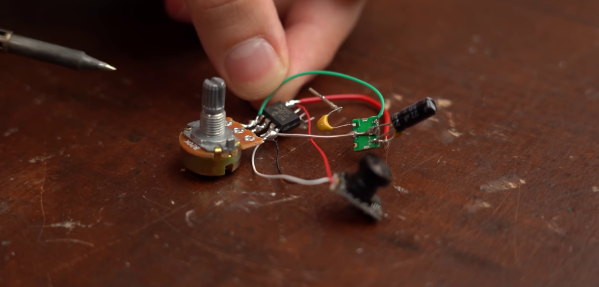
After a brief failed experiment with a simple circuit built from discrete components, [GreatScott] turned his attention to voltage-controlled oscillators (VCO). He bought a couple of 5.8 GHz VCOs from Aliexpress, and created and used a simple opamp circuit to boost the FPV camera video signal to the required input level for the VCO. This failed to produce any identifiable image on his video receiver goggles. In an attempt to confirm that the VCOs produced the desired frequency, he ordered a similar 2.4 GHz VCOs and built a short range (20 cm) WiFi jammer. With a signal generator to create a simple input signal, and confirmed that it interfered with his laptop’s WiFi connection.
After more experimentation with other VCOs, the closest [GreatScott] came to success was a barely identifiable image transmitted using a Maxim 2.4 GHz VCO. If you have any ideas on what is missing in the VTX circuit, drop them in the comments below.
Building RF circuits that interfere with the legitimate signal around you, or broadcasting out of band, is generally not a great idea, and could earn you an unpleasant visit from the authorities. If you want to build your own digital video transmission, take a look at the Wifibroadcast project.