[Roberto] recently discovered a clever way to gain root access to an HP t520 thin client computer. These computers run HP’s ThinPro operating system. The OS is based on Linux and is basically just a lightweight system designed to boot into a virtual desktop image loaded from a server. [Roberto’s] discovery works on systems that are running in “kiosk mode”.
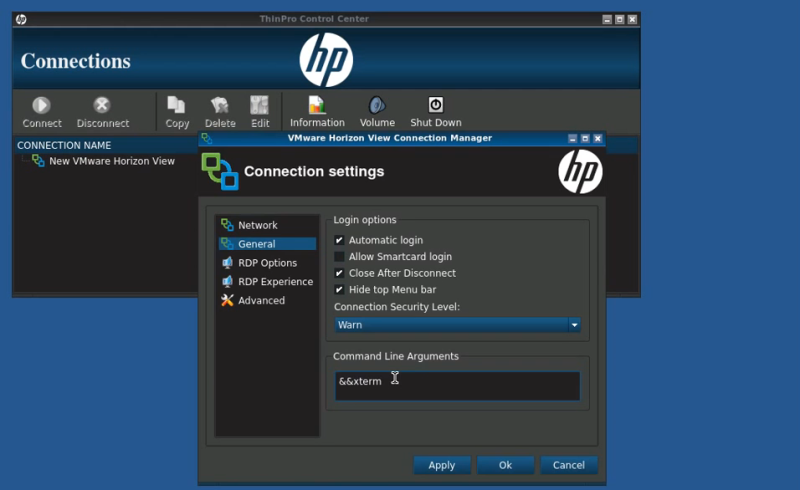
The setup for the attack is incredibly simple. The attacker first stops the virtual desktop image from loading. Then, the connection settings are edited. The host field is filled with garbage, which will prevent the connection from actually working properly. The real trick is in the “command line arguments” field. The attacker simply needs to add the argument “&& xterm”. When the connection is launched, it will first fail and then launch the xterm program. This gives the attacker a command shell running under the context of whichever user the original software is running as.
The next step is to escalate privileges to root. [Roberto] discovered a special command that the default user can run as root using sudo. The “”hpobl” command launches the HP Easy Setup Wizard. Once the wizard is opened, the attacker clicks on the “Thank You” link, which will then load up the HP website in a version of Firefox. The final step is to edit Firefox’s default email program association to xterm. Now when the attacker visits an address like “mailto:test@test.com”, Firefox (running as root) launches xterm with full root privileges. These types of attacks are nothing new, but it’s interesting to see that they still persist even in newer software.
















LOL good ole’ security.
“Security”
This is first-grade stuff here HP. Comeon!
What is here the fail of HP? Is it common to prevent adding additional commands like && xterm ? Or is the real fail that hpobl can be started as sudo?
Both really. User input (the “&&xterm”) should be sanitized so that it doesn’t end up executing additional commands, and processes running as root should be minimised to reduce the attack surface. It’s a set of chained vulnerabilities, so multiple failures had to occur in order for someone to get root.
One could argue that xterm shouldn’t even be installed on a “kiosk” machine.
Since he Had physical access to the box why not boot a Linux distro and set the root password. I have done this myself on other Hp terminals.
Because he wanted to show that its possible to gain root without physical access to the box.
“The point of this blog post is to demonstrate that a malicious actor can compromise such thin clients in a trivial and quick way provided physical access, a standard prerequisite in an attack against a kiosk.”
I wonder if he could just type && sudo /usr/bin/hpobl into arguments.
Brutus indice the staff ?
Well, I am going to ask a silly question:
The attacker first stops the virtual desktop image from loading.
To me, that is a string of words and I have no idea how to do that.
Granted I am not of linux background, but I know a bit about computers.
Just a passing question. Thanks.
Reading the article, the closest thing I can find is “Select the connection profile, and edit the profile (if it auto-starts, then you should cancel the connection)”, as in “The attacker first stops the [profile] from [connecting].” I can assume from the context that there would be a “cancel” button at this point.
The usua purpose of a thin client is to load its real OS from a image on a remote server. One of the potential formats for these images is the VDI, or Virtual Desktop Image, usually named with the extension *.vdi.
Instructions unclear. Ended up loading and running Crysis at 1020p@60Mhz. All jokes aside. If you are interested in old school thin clients. There is GREAT resources out there. AKA I had bought a used HP t5745 with the express purpose to run PFsense & Untangle on it. However I imagine folks driving up ebay prices to retarded levels for deprecated gear.
I will tell you this much. There is a nice fellow out there in the U.K. that has repurposed OVER 50+ FUQIN Thin Clients. INCLUDING THE HP THIN CLIENT FAMILY. With FULL documented efforts.
PARK Y ur vw bus.
TOWERS are intended to fall.
U.K. has some really innovative people.
Get it together HaD this article belonged in reddit reverse engineering.
I recently bought a t5325, arm architecture, works beautifully, but I can’t connect with RDS 2012 onwards. I was wondering if you have new repositories, to update thinclient, or another O.S. that has already been ported to it.