If you’ve been holding off on upgrading your kindle, this project might inspire you to finally bite the bullet. [WarriorRocker] recently saved quite a few dollars on his Kindle upgrade by using a demo unit. Of course, it’s not as simple as just finding a demo unit and booting it up. There’s some hacking involved.
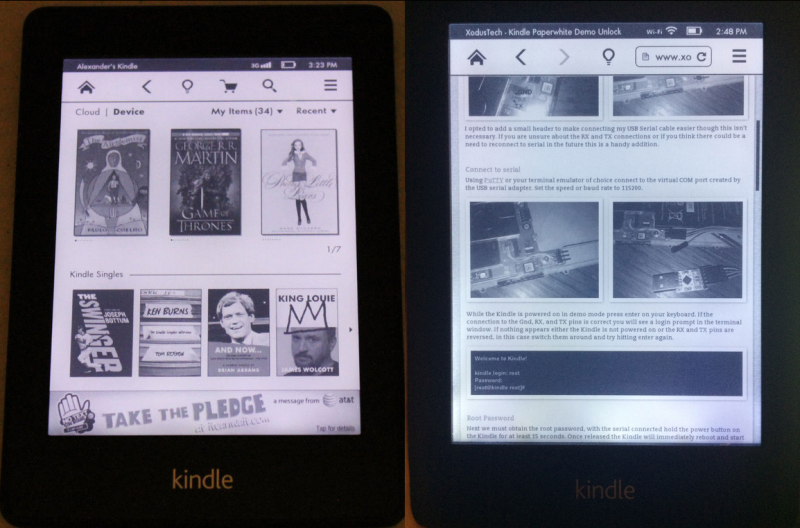
[WarriorRocker] found his Kindle Paperwhite demo unit on an online auction site for just $20. Kindles are great for reading but also make popular displays for your own projects. This used display model was much less expensive than a new unit, which makes sense considering it had probably received its share of abuse from the consumers of some retail store. The problem with a demo unit is that the firmware that comes with it is very limited, and can’t be used to sync up with your Amazon account. That’s where the hacking comes in.
 The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The next step requires root access. The root password for each unit is related to the unit’s serial number. [WarriorRocker] obtained the serial number by rebooting the Kindle while the Serial connection was still open. The boot sequence will spit out the number. This number can then be entered in to an online tool to generate possible root passwords. The tool is available on [WarriorRocker’s] project page linked above.
Next, the Kindle needs to be rebooted into diagnostic mode. This is because root logins are not allowed while the device is booted to the system partition. To enter diagnostic mode, [WarriorRocker] had to press enter over and over during the boot sequence in order to kill the automatic boot process. Then he checked some environment variables to locate the memory address where the diagnostic mode is stored. One more command tells the system to boot to that address and into diagnostic mode.
The last step of the process begins by mounting the Kindle as a USB storage device and copying over the stock Kindle firmware image. Next [WarriorRocker] had to exit the diagnostic menu and return to a root command prompt. Finally, he used the dd command to copy the image to the Kindle’s partition bit by bit. Fifteen minutes and one reboot later and the Kindle was working just as it should. [WarriorRocker] even notes that the 3G connection still works. Not bad for $20 and an hour or two of work.















Excellent! Nice clean work.
“The problem with a demo unit is that the firmware that comes with it is very limited, and can’t be used to sync up with your Amazon account. ”
Kindles can easily be loaded with offline mobi files without even bothering with the Amazon crap in the first place. I’m assuming the demo firmware has other limitations?
In demo mode you cannot access the web browser or access the device over USB.
Pretty interesting read. Actually sounds doable too :) Good job, WarriorRocker
Nice! Now all I have to do is find a demo unit!
It would be neat to get a bunch of demo units, use his guide to install the stock firmware, then donate them to a library.
When I started to read your comment I thought you were going to say selling them on ebay instead of donating to the library ;)
Warrior Rocket Advises “In demo mode you cannot access the web browser or access the device over USB”
Beyond that in general really don’t want to be involved with hacked commercial products directly. Many don’t have the time to load requested files. However they may will wiling to direct patron to hacker spaces or individuals or hacker spaces, who would volunteers loan out the units along with loading requested media. All in all I can’t see book readers being a viable lending device, even new ones. Flash memory has limited delete cycles. For patrons who borrow them may need the password for the device to use the unit I don’t know.
Flash memory has limited delete cycles of 100K or a million or so, depending. It’d take a hell of a long time to wear it out, and even when one block goes the firmware can cover it up by paging in a different one. Flash memory is awesome! Hence why it gets used so much for storage. Your average flash drive will, I bet, outlive any magnetic media.
Looks like the Demo unit on the Bay is going for more than the non-demos. Ahh the true cost of hacking. :)
No that’s the true nature of auctions anywhere. Bidders get afflicted with tunnel vision. what one person perceives of common sense may not prevail.
I hope someone is able to root the Kindle Voyage.
I did it long time ago: http://www.mobileread.com/forums/showpost.php?p=2576462&postcount=1242
Do you try to register kindle with amazon account ?
Yes I was able to register and even make purchases through my amazon account.
Anyone know how to fix a ‘your kindle needs repair’ screen? Can’t find anything on it.
I was able to follow the walkthrough all the way to the point of attempting root access, I am unable to log onto root. The two demo unit’s I have will both allow me to get to the same point, however the root passwords generated do not work for either of them. has anyone else had this problem?
May I ask a stupid question?
How do I create a virtual COM port (under Win7x64)?
Or do I need a hardware USB-Serial adapter?
Thanks.
At least on the KT2 (the 2014 all-touch, nonilluminated Kindle) it’s enough to type “;demo” in the search box to access the secret menu where you can reach settings or USB mode — or choose “Resell” which will factory reset it and disable demo mode!
By the way, it can be enabled at the initial setup by long-pressing a language for about 15 seconds (this only works if certain files are on its memory, i.e. only the first time on an unmodified system) or by another search bar command I don’t remember at the moment!
A lot of people did it a long time ago, and MUCH easier than cracking it open to use the serial port:
http://www.mobileread.com/forums/showthread.php?t=170929
And interestingly, the demo kindles I tried all had working 3G internet already registered to some internal amazon account (anonymous 3G internet), though I would not recommend making any ebook purchases to that account. I unregistered and reregistered them to my own amazon account, with no compliants from amazon.
But for the latest PW2, it seems that a serial port is required:
http://www.mobileread.com/forums/showthread.php?t=254400
I ended up finding a 7th gen Paperwhite cheap that was a factory built store demo model.
Someone told me to search for the book ;demo
Bang bang bang, a few clicks later, it reset and is now in full home user mode.
I have a demo unit that I bought for my wife to study i would like to know how did you unlock it ??
thanks in advanced for your help
Can you explain to me how you have unlocked it? Thank you!
I follow this Tutorial , seems all have ben installed whir no problems justthe hardware and software are not compatibles, because i got this error Message:
Hit any key to stop autoboot: 0
## Booting kernel from Legacy Image at 80800000 …
Image Name: Linux-3.0.35-lab126
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 2420480 Bytes = 2.3 MB
Load Address: 80008000
Entry Point: 80008000
Verifying Checksum … OK
Loading Kernel Image … OK
OK
Starting kernel …
[ 0.094280]
[ 0.253849] LPDDR2 MfgId: 0x1 [Samsung]
3.0.35-lab126 #1 Wed Sep 4 16:00:40 PDT 2013 armv7l
Press [ENTER] for recovery menu… 0 //dev/mmcblk0p4:
CHS=4/16/102976 size=3374317568 bytes
flag type first last lba first lba size
Partition p1:
0x00 0x0b 16 16 6590448
CHS: 0/1/1 –
Partition p2:
Partition p3:
Partition p4:
BOOTING DEFAULT.
IP-Config: no devices to configure
kinit: Mounted root (ext3 filesystem) readonly.
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
info system:emiting_event:mounted_proc:
info system:emiting_event:mounted_sys:
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
info firsttime:mount_rw:time=5720:Mounting root RW for first boot
info firsttime:mount_ro:time=6040:Mounting root RO
info system:emiting_event:mounted_dev:
info system:emiting_event:mounted_tmpfs:
modprobe: FATAL: Could not load /lib/modules/3.0.35-lab126/modules.dep: No such file or directory
init.exe: system pre-start process (628) terminated with status 1
init.exe: network main process (708) killed by TERM signal
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: recevent pre-start process (712) terminated with status 1
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process (723) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process (734) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process (746) terminated with status 2
init.exe: syslog main process ended, respawning
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: system_monitor main process (719) terminated with status 255
init.exe: syslog main process (753) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
init.exe: syslog main process (760) terminated with status 2
init.exe: syslog main process ended, respawning
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process (767) terminated with status 2
init.exe: syslog main process ended, respawning
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process (774) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
init.exe: syslog main process (781) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
init.exe: syslog main process (788) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
init.exe: syslog main process (795) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog main process ended, respawning
init.exe: syslog main process (802) terminated with status 2
crit hardware:bad_id:id=02722011336703U9:bad board ID, defaulting to yoshi !!!!! !
init.exe: syslog respawning too fast, stopped
Any Idea to reset it back to Demo Mode?? i still can join to Diagnostic Mode.