[Alexander Graf] gave an absolutely hilarious talk at 32C3 about the security flaws he found in cable modems from two large German ISPs. The vulnerability was very serious, resulting in remote root terminals on essentially any affected cable modem, and the causes were trivial: unencrypted passwords in files that are sent over TFTP or Telnet to the modems, for instance.
While [Alexander] was very careful to point out that he’d disclosed all of these vulnerabilities to the two German cable ISPs that were affected, he notably praised one of them for its speedy response in patching up the holes. As for the other? “They’d better hurry up.” He also mentions that, although he’s not sure, he suspects that similar vulnerabilities are present in other countries. Oh dear.
A very interesting point in the talk is the way that [Alexander] chose to go about informing the cable ISPs. Instead of going to them directly and potentially landing himself in jail, he instead went to the press, and let his contacts at the press talk to the ISPs. This both shielded him from the potential initial heat and puts a bit of additional pressure on the ISPs to fix the vulnerability — when the story hits the front page, they would really like to be ahead of the problem.
There’s even a bone for you die-hard hardware hackers out there who think that all of this software security stuff is silly. To get the modem’s firmware in the first place, at minute 42 of the talk, [Alexander] shows briefly how he pulled the flash chip off the device and read it into his computer using a BeagleBone Black. No JTAG, no nothing. Just pulling the chip off and reading it the old-fashioned way.
If you’ve got an hour, go watch [Alexander]’s talk. It’s a fun romp through some serious vulnerabilities.

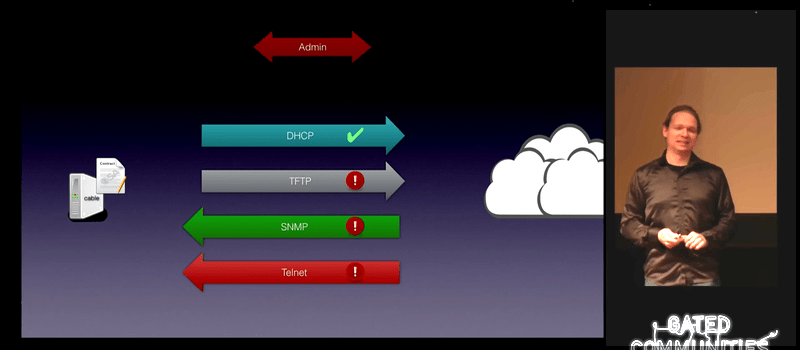















The best thing you can do with the modem your provider gives you is to immediately switch it to bridge mode and use some open-source powered router (or some with reliable frequently updated firmware) behind it. Problem with “misfortune cookie” is present (and known) for more than 14 years, and most manufacturers and ISPs hasn’t yet fix it. Check out this video for more information : https://www.youtube.com/watch?v=gFP5YcvQsKM
or exploit and post instructions and even tools to exploit so it forces the isp’s hand so they will fix it.
In practice they won’t, because the customers haven’t got a clue and won’t complain even when their systems are compromized, because they’re none the wiser as long as the intruder doesn’t use it for constant mass-spamming.
The ISP basically doesn’t give a shit whether their customers are being spied on, or are part of a huge botnet, as long as it doesn’t touch their bottom line.
Point being that in making the exploit public, you’ve simply thrown millions of people under the bus because the ISPs won’t do anything about it.
Exactly. I wrote comment earlier, but it didn’t get approved, I guess HaD has some sort of filtering system for posting too much URLs, so here it is again, without URL :
TP-Link’s firmware from the year 2014 uses flawed (and they know it) web server dated 2002. So you can see how fast are they when it comes to fixing exploits. Watch video I linked above if you want to know more about that problem. More details about the bug can be found here : …
Seconded. I generally don’t buy multi-purpose, combination devices. I buy best-of-breed for the cable modem, router and wifi.
Some providers don’t even allow you to bring your own modem and force a shitty router/modem combo on you. In many areas shitty ISPs are the only ones available so you can’t always just chose one that doesn’t do this.
Is there a version in English?
In the download links.
The version I see in the viewer (and the original) are in English. It seems strange that you’d get the dubbed version.
Anyway, as you mentioned, there’s many options in the download tabs.
I thought someone finally did an analysis of DOCSIS interception and design
Well about 10 other countries have this model and make of this modem.
Mine ISP included. Funny thing my ISP has an online tool to modify WiFi password and such, sends snmp strings to modify them.
I would not be suprised if this has the same thing going on.
Someone Also managed to Get root access to this kind of modem.
If Your ISP has association with liberty global. You might have the same issue.
The company Compal that made the modem isnt that secure either…
The thing is hardware and firmware are irrelevant.. Nobody writes their own protocol stacks.. Also it’s just firmware attacks it’s nothing new..
I ranted about this exact scenario last year on slashdot !
Here in Belgium there is basically only one cable provider, Telenet NV.
When my old DOCSIS 2 modem died, they gave me (without any options) one of their all-in-one fancy new ‘modems’, with built in router with private + public wifi. To manage my modem settings i had to go to their webpage to change MY modem/router/lan/wifi settings, which would then be pushed to my modem locally. So if their site is down (which happens quite regularly imo, for ‘maintenance’), i can’t manage my own LAN ! Can’t change the wifi pwd. Can’t check what MAC’s are authenticated on the wireless interface. etc. Running services behind NAT is also a no go for me.
Heaven forbid if someone ever finds an exploit in those modems, all of their customers’ LAN’s will be compromised !
I re-disabled the public wifi several times, after it got mysteriously re-enabled. Forget about calling support, you always get brain-dead morons that won’t deviate from their silly ‘please reboot your modem’ flowchart even though you can provide perfect logical reasoning to locate the problem and tell them your an EE. Power users are a nuisance to them. Repeated calls to support to ask for a normal modem as a consumer were all fruitless. I later played my cards different with the business support desk (as a business owner) and with some social engineering was able to get someone to give permission(!) for me to get a normal modem (just modem, no router, no wifi crap) at my local telenet supplier.
As of 2013, Liberty Global own a 57.8% stake in Telenet NV.
A USA telecommunications and television company that is buying up broadband providers worldwide.
With recent revelations this is also worrisome.
TL;DR
Your ISP should not manage YOUR LAN !
Seriously people, call your ISP and demand a normal modem and get your own router.
Power users are left in the cold, especially by the big companies.
Well someone needs to manage people’s LANs and the majority of humans have no clue at all how to go about it. Which is exactly why ISP routers exist. People want plug and play.
Going to be interesting to see what happens when IPv6 becomes standard part of ISP rollouts.
I mean, there are folks pushing for no NAT in IPv6 on the basis that everyone should have enough IPs to not require it, but then that means you effectively need to open up the mapping of your internal LAN to the outside world (firewalled of course, but the internal addresses will be determined by the outside without NAT)… not sure if I’m a fan of that idea regardless of the protocol benefits.
Some people? My understanding was that this was pretty unanimous among IPV6 proponents. Many times I have considered setting up an IPV6 tunnel but I have come to like the added security of being behind the NAT.
The IPv6 equivalent would be called a firewall. They exist for IPv4 too. Only difference with IPv6 is you aren’t *required* to have one in order to save addresses.
Here in Serbia most of the people use Telekom Srbija as their ISP, and get the ADSL modem from them. On all of them the admin password is the same and there is some sort SSH server on them too. Not very capable of doing anything, however you can send pings from it.
Youtube link:
https://www.youtube.com/watch?v=XGmDBo-00mY