Of all the ways to open up a lock, there are some tried and true methods. Keys, combinations, RFIDs, picks, and explosives have all had their time and place, but now someone else wants to try something new. [Erik] has come up with a lock that opens when it is shown a pattern of colors.
The lock in question uses a set of color coded cards as the “keys”. When the cards are inserted in the lock, a TCS230 color sensor interprets the pattern on the cards and sends the information over to an Arduino Uno. From there, the Arduino can command the physical lock to open if the pattern is a match, although [Erik] is still waiting on the locking mechanism to arrive while he continues to prototype the device.
This is a fairly unique idea with a number of upsides. First, the code can’t be “stolen” from inside a wallet like RFID cards can. (Although if you can take a picture of the card all bets are off.) If you lose your key, you can simply print another one, and the device is able to handle multiple different keys and log the usage of each one. Additionally, no specialized equipment is needed to create the cards, unlike technologies that rely on magnetic strips. Of course, there’s always this classic way of opening doors if you’d rather go old school with your home locks.

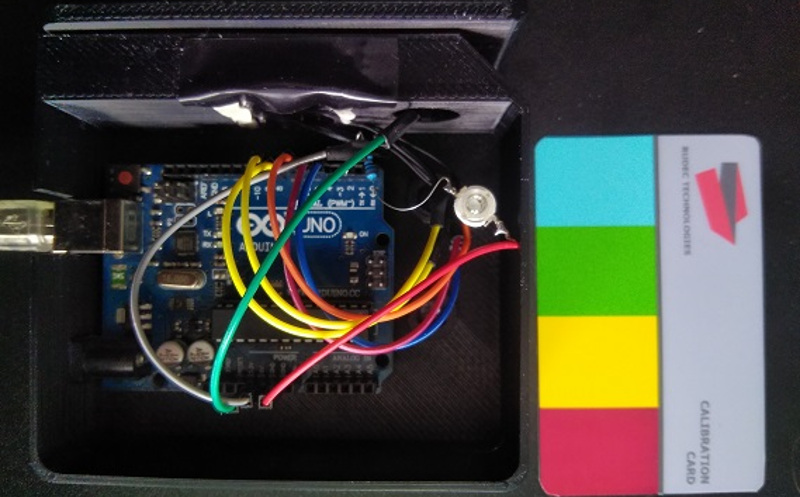














Hm. Effectively a color barcode?
I already know about the 2D “High Capacity Color Barcode”.
And I guess the early KarTraks were color.
Are there others?
Worst idea since ages !
Quoted from the site : “The idea behind this system is to avoid using RFID authentication, as it can be ‘stolen’ without contact”.
It’s a well-known fact people around all have an RFID ready with them, but no one carry a camera…or just their own naked eyes…
That said, locking the bird food dispenser may be one purpose.
I was thinking something like this too. Also, what happens if the colour on the card fades with time? I think an active device with a RGB LED would be more secure as you could only activate it when it’s against the sensor and you’d be able to have multi-band rolling codes. Different key pairs for each colour, etc.
Why not use a QR code? Seems more secure, harder to duplicate with just a simple picture.You could even make a card and reader in such a way that the code would not be read until it were inserted into the reader.
Correction: could would not be s/read/visible/
Interesting concept, and i agree itd probably be a better route in some or even many cases. I think the project was more of a proof of concept about solutions that could be acheived with simple/cheap hardware and relatively simple code.
Or just a barcode.
Granted, QR codes look cooler.
eink display; with qr code that changes randomly; https://hackaday.com/2016/08/23/compact-epaper-business-card/
Anyone remember those old hotel keycards that had a pattern of holes in them? Yeah, that idea was pretty good.
Color me a dim bulb if you must, but I never did figure out exactly how the reader works. I’m guessing it’s something like pogo pins or leaf switches or (most likely) an array of ball bearings on springs, i.e. mechanical contacts rather than anything else… especially since the cards always seemed (to me at least) to make a little mechanical ‘scrunch’ noise when you stuck ’em in the lock… sort of like pins aligning in a Yale (regular, modern door) lock, but bigger and more of them.
Of course, I could be wrong about that. Various bits of optical trickery come to mind — arrays of little ‘grain of wheat’ bulbs and CdS cells, or (for newer stuff) LEDs or even laser diodes and photodiodes/phototransistors… hmmm… I don’t think a hall effect sensor array would work, even with a metal card, and — although I’ve got that little niggling ghost of a memory in the back of my head tickling me like I’m forgetting something — I can’t remember seeing a card like that that wasn’t plastic…
I remember hearing and feeling the pins (or whatever) when I put the card in the lock.
Apparently one major vendor (were there multiple?) was VingCard.
Many years ago, my uni student identification card was a credit card sized piece of plastic with my 8-digit student number punched into it across the card in 8 rows of 10 columns. Even at that time I could not believe they had not added any extra digits for some sort of checksum. This card amongst other things was used for borrowing books from the uni library, which was an automated card reader and (IIRC) scanned a barcode on the book, no human interaction.
It would have been a trivial – and I mean, trivial – thing to cut a piece of plastic card the right size, and using nothing more than a hobby knife and a ruler, cut any student number I liked… crazy.
By ‘no human interaction’ I meant to say ‘no library staff interaction’. This was not meant to imply that librarians aren’t human.
RFID can use rolling codes or challenge/response systems that make stealing the code while the card is in your pocket nearly impossible, even though attacks exist against car keyfobs that use those (jamming and replaying codes mostly).
I’ve seen sliding magnetic keys before, and one-wire devices or other contact-based smartcard would be very secure, considering the need for electrical connection and the power available which is one of the factors limiting the complexity of cryptography you can use in the key.
Forgot: it is kind of funny for anything not so serious. I once but a system for a university project to use similar color codes in stripes on the floor for a navigation system for dementing elderly people in retirement homes.
I see 6 distinct colors on the cards; assuming 4 more colors can be used (orange, purple, pink, gray? No card probably reads as black so you can’t use that as a color), and it is restricted to 4 bands with no two identical adjacent bands and the reverse order considered the same, the number of combinations would be 10 * 9 * 9 * 9 / 2 = 3645. Not quite as terrible as I expected, a brute-force attack (where the attacker would need to test each card in either direction, so 7290 swipes) seems unlikely.
Maybe an extra layer could be added, that uses non-visible light, like UV or IR, to prevent the obvious camera attack? The colored bands seem rather useless then, because the can’t be considered secret, but maybe the colored ones should be the username (needed but not secret) and the invisible bars would be the password? This would greatly decrease the chance of collisions.
Great idea! It could be an integration of barcode sith nice colors printed. Already thinking about using brand colors! Love it!
We have a storage basement separated from the house which we want to keep locked. It was frustrating to go out and find out that you forgot the key or at night that you forgot to lock the door.
I didn’t want to use any cards or keys, so I installed a door bell button connected to an Arduino and a solenoid operated lock. The door only opens when the correct morse code is entered. Simple and convenient.
Why not an optical/chromic version of a rolling code using the screen of a smartphone?
Color sensors are pretty easy these days and it’d be pure heck to try and replicate it on the fly “Was that pink then orange then black or….?” You might be able to eavesdrop with a video camera but I’d bet it’d be a low percentage of success.
This would actually not be that bad if the color was measured in non RGB wave lengths and some non trivial colors or colored material were used. People often assume that there are only the colors we can see and though they are easy to reproduce. But there are much more different colors, we just can’t tell them apart and neither can regular cameras.
The problem with this idea is that you can’t just use a normal printer to generate the code. But you have to have different colors e.g. one orange made from the pure orange wave length and one that is mixed yellow and red.
“Honey, I lost the house keys!”
“Here, I just xeroxed a copy of mine”
I was thinking like others with the card being inserted to hide the code until reading OR using something akin to the holograms printed into driver’s licenses; more expensive to print, but a bar code scanned while illuminated by an IR LED would be hidden under most circumstances.
I liked the eInk idea someone suggested. Use either that or smartphone to display QR code that is a time-based OTP code generated by local app; read by door camera; open sesame. Even double bonus if security camera on the porch could act as some sort of backup reader, if not primary (assuming something you built and more secure than the normal crap that becomes the next botnet).