You might be surprised to find out that it’s actually not a good idea to put all of your credit card information on a little Bluetooth enabled device in your pocket. Oh, what’s that? You knew already? Well in that case you won’t find the following information terribly shocking, but it’s still a fascinating look at how security researchers systematically break down a device in an effort to find the chinks in its armor.
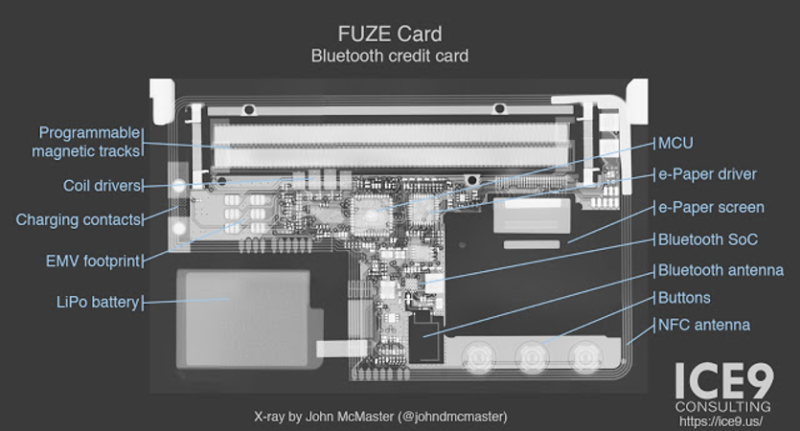 [Mike Ryan] of ICE9 Consulting has recently published an article detailing the work done to examine and ultimately defeat the security on the FUZE Card. From using an x-ray machine to do non-destructive reconnaissance on the device’s internals to methodically discovering all the commands it responds to over Bluetooth, it’s safe to say the FUZE Card is cracked wide open at this point.
[Mike Ryan] of ICE9 Consulting has recently published an article detailing the work done to examine and ultimately defeat the security on the FUZE Card. From using an x-ray machine to do non-destructive reconnaissance on the device’s internals to methodically discovering all the commands it responds to over Bluetooth, it’s safe to say the FUZE Card is cracked wide open at this point.
To be clear, the attacker must still pair with FUZE, so physical access is required. But as pointed out by [Mike] in the blog post, handing your card over to a merchant is standard operating procedure in many cases. It isn’t as if it would be hard to get a hold of one of these FUZE cards for a minute or two without the owner becoming suspicious. Pairing FUZE to the Linux device to continue to the next step of the attack only takes a few seconds, as demonstrated in the video after the break.
Once paired, the attacker can simply send a BLE command to FUZE which disables the lock screen. It’s really that simple. The attacker can also send commands to dump credit card info over Bluetooth, meaning they could download your information even when the card is “safely” back in your pocket. The inherent failure in the FUZE design is that you don’t need to provide any sort of authentication to pair it to a new Bluetooth device. It makes the (very dangerous) assumption that the person holding it is entitled to do so.
Even if you know better than to ever buy a device like this, the post [Mike] has written up is really a must-read for anyone who’s ever looked at a device and tried to figure out what was going on in its little silicon brain. We especially liked his assertion that reverse engineering a device essentially boils down to: “staring, thinking, a little experimentation, but mostly staring and thinking.” We’re having an internal debate here at Hackaday HQ about making that the site’s tagline.
Incidentally, this is very similar to the Bluetooth gun “safe” that was cracked not so long ago. At this point, it might be wise to just stay away from anything with that little blue logo on it if you intend to trust it with your identity and/or deadly weapon.
















Some things that don’t need wireless connectivity:
Credit cards
Passports
Condoms
Your house
Car
Actually pretty much everything.
I think that NFC can make sense in many situations, IE passports, but ideally they would need to be open to get good reception.
Or require individual authorization like mobile payments.
Scientists might argue for the last.
I don’t know wireless connected Condom could have benefits sync it with your fit bit data just have a spare Mac addy for other ones in case activity is not always with the same partner
Somehow I think a wireless condom would still be preferable to a wired one…
Just my 2 cents… Would it not be difficult to add a spot on a credit card which would require pressing or squeezing before it becomes wireless? Some say the chip in the card is a miniaturized computer with a processor and some memory, but they just can’t add a freaking “enable wireless” button into a hollow or shallower spot on the card. No, not a thick momentary switch, but one of those slim buttons on things like phone keypads. But on the other hand, if that was a good idea, they’ve probably would have done it by now…
It’d be completely easy, I’m sure. Although a possible source of failure, and moreso, possibly falsely blaimed for other failures. It all adds up in support calls.
I think the problem is, much of the public genuinely get confused even by a single button. And more importantly, when you add security measures, people panic, alerted to a danger they previously weren’t aware of, and stay away from your product. You’d probably find people preferred a competitor’s card, without the button, even though that obviously would have the same problem. Denial, cognitive dissonance, are powerful forces in the modern idiot’s brain. This is why the world doesn’t work properly.
Hopefully, we’ll be able to pick these up for a buck apiece at surplus stores in the near future.
Then you’ll have recovery hacks that can find the previously stored cards
Hell yeah, I’d love a reprogrammable magstripe
I’m glad they did it the right way and gave Fuze a couple months heads-up. It’s still staggering that a company would allow another researcher to drop the mic before they release a statement to the public, including their own customers, with details and response time-line. The potential PR damage to Fuze seems way higher now.
Well… y’know… good.
Even IF this didn’t have great big gaps, we really don’t want people trusting Bluetooth credit cards, or Bluetooth money-anything. Simplicity is an important part of security. At least, the right amount of simplicity, but ideally, as much as possible.
Bluetooth is already wobbly and badly-implemented in practice. And the idea that any credit card should ever transmit it’s details is insane.
I believe the NFC cards transmit actual money, or at least encrypted tokens that are interchangable with money. There’s a limit to how much you can store on the card at once, so even if someone steals that, assuming a leak, they don’t get the heart of the card, your account details. They don’t get owner’s information. This was built into the design, designed so that EVEN IF the security fails, there’s a limit to the damage.
This, though, seems based around “Nah, who’d ever try hacking a credit card?”. Why does it need commands to spit the card details back out? Why would any crazy bastard make a wireless credit card? What problem is it supposed to solve? If it did solve a problem, it’d have to be a hell of a benefit to compensate for the risks just in principle, never mind the ones found here.
Hopefully this story might make the public a bit more skeptical about technology. People are encouraged to buy and use all this high-tech stuff, but often aren’t even aware information security is even a thing. We’re going to need information security awareness ever more in the future.
The basics are just a few simple principles. Wouldn’t be too hard to teach the public, if anyone wanted to. Unfortunately though advertising wants to know everything about you, and banks won’t tell you about the need for security, because that implies that risks exist, and that makes people unhappy.
The card is wireless to allow adding credit cards into it. It has NFC for tap to pay, but i’m not certain that the NFC is used to program the card. A single card that stores every card you own is sort of cool, but it should require the owners smartphone to provide a Bluetooth private key, along with its own public shared key, to allow a card to be readable at all. In other words, the data on the card is encrypted and useless without the smartphone nearby to provide the other half of the key to decipher the information on the card. This way, nobody can read out the data on the card in any usable way without having both keys.
The complete list of useful bluetooth devices:
* Headphones
As far as I’m concerned Every Blue tooth device is a pain and not worth it.
Ever since Blue tooth has been around I have had nothing but trouble with them.
I’ve got all most all the dongles you could get your hand on, And they all have given me problems.
Every device I’ve had has given me nothing but trouble.
Damn straight, Bluetooth has always been rubbish they just keep pushing turds up a hill, The first of the Keyboard and mouse combos I heard of people unable to control their machines and lose work / assignments and requiring the Host machine reboot the OS to enumerate the devices again for it was really just poorly implemented.
Sloppy software stacks (so what else is new?)
* Keyboard / mice / controller
* Serial adapters
*printers
Ends at headphones and depending on the brand or Chipset used some are not transmitting the complete sound, Those Lamestation Bluetooth controllers would have to be the most laid back waiting in a queue for button presses.
Nah the only REAL Bluetooth-device I want and really need is a hands-free in my car.
Everything else I can live without. Yeah my Fitbit Tracker is neat, but not a necessity. Bluetooth Audio for hands-free communication is a MUST because otherwise we would still be stuck with 20 adapters for each car that is crazy expensive (think the old nokia-adapters to couple your phone and car).
What’s next? Bluetooth Toilet Brush?
Even a Bluetooth Toothbrush is way to much crap.
You hand your card to a merchant? Normally here, the merchant hands you the card terminal. You handle the merchants point of sale equipment, not the merchant handling your personal cards.
POS terminals are still possible attack vectors … How many card skimmers are active in North America in any given day? This would just give a new way for a compromised terminal to access card data.
Not in the US: at a restaurant for example, you’ll hand your card to the waiter after filling the bill and he’ll do his stuff at the counter, it’s not uncommon to wait for few minutes befor you’re given your card back.
You don’t have to handover your card, you simply say you keep it and go with them to the terminal. Handing over your card is also in some TOS from issuers and falls under you are responsible for the card and don’t give it to a 3rd party.
you must be fun at restaurants
Its funny because i live near the border, and in Canada they bring you a mobile terminal. The first time i ever paid by credit card in the us the server was suprised when i got up to follow them to the POS. They also asked about the chip contacts on the card as well. Suffice to say, the only reason that people do things as they do in the US is a lack of education about it. That is something i try and change every time i encounter it, like with the tap to pay trend. Just call your bank and have it disabled, its just safer to maintain physical domain of your cards and enforce the use of a secure pin to use it.
if I ever get over there and am short of cash…
Different countries, different SOP. US never properly got EMV because our liability laws were different. We never got portable card terminals whatsoever, they’re mostly all wall-powered and bolted to a post at a cash register or integrated into the register itself. Sometimes you get passed a PIN dongle connected over modular jack serial but that’s about the limit.
There has to be more to the story about the lack of portable payment terminals in the USofA. Perhaps it is their cost?
The bank owns them and they cost a lot of money monthly to lease, not to mention that the credit card company keeps a few % points for themselves of all your hard earned transactions. The terminals are cellular connected and considered secure at that level.
Every other country manages. Maybe it’s the endemic ignorance Americans have about the outside world, and they just don’t know there’s an alternative to giving your card to random shop employees. Or even that it’s a bad idea. Maybe banks think it saves money to use horribly outdated equipment from the Bronze Age, or maybe it gives them some advantage in screwing somebody somewhere. There’s probably a reason.
Modern portable card terminals aren’t a lot different from smartphones. Just with a keypad and a chip reader. Maybe a magstripe reader too. They can’t cost much to make, banks could afford to give them away free with a small business account, and make the money back in a higher % transaction charge. Larger businesses would negotiate as they always have.
Quick search…
https://startups.co.uk/small-business-credit-card-machines/
Yep they cost almost nothing to purchase outright. 59 quid British, or 15 a month for another one. Lots of choice in where to get one. There’s even one that plugs onto your smartphone, Apple or Android!
I think Americans are being ripped off here.
I really enjoy going on vacation to USA, however, I don’t like the way credit cards are handled there.
2/3 of the road trips I been on resulted in unauthorized credit card transactions after I got back. So I’ve started to replace my credit cards after each trip.
Pairing with a new device should mandatory force a wipe of the current users data. There is no reason to pair to a new phone unless it also has the app and at that point you can already assume you can re-download fresh card credentials.
New pairing=New owner. I suspect a firmware update will fix this shortly, but your article makes it sound like it’s already the end for this product.
it should be the end of such a product. This is one of the cases where people designing the product were asking CAN we do it and not SHOULD we.
Now I’ll have to buy one for the arbitrary code execution.
Having a programmable magnetic strip would come in handy. And a cute little e-ink!
True, it’s pretty nifty, as long as it goes nowhere near anything with money in it.
The next challenge to get DOOM to run on…..
Maybe a dumb question, but, should we care about credit card security issues? I mean, over my life so far, owning various credit cards from the late 80’s until now, I’ve experienced fraudulent charges on my cards on at least 3 different occasions that i can remember, and I’ve never even been close to being on the hook for them. As far as I can see, if a new technology makes using my credit card more convenient, why shouldn’t i use it? If my card info gets compromised, the credit card company has me covered. The way i see it, I’ll eventually be on the hook for it through increased prices as the cost of fraud is passed from the cc company to the merchant to me, but, I’d like to think that cc companies will take responsibility for their cards’ security so they don’t have to increase merchant costs and risk losing merchants. So, why should i worry about it?
What if it only charged you a little bit of money, at irregular intervals? Would you notice? What if it did the same to thousands of people?
Even if you don’t care, banks need to. This doesn’t affect most of us here in a practical way because we’re probably all smart enough not to use such an obvious fraud-magnet. But as a geek it’s a very interesting subject. So, bankers and geeks.
And it is nifty hardware. Terrible idea, but nifty. Now to wait for some genius to port Linux to it. Or Doom.
Condom Wi-Fi ?
Fucking stupids !
So we can say that “s” in Bluetooth stands for “security”?
They have analyzed the issues and have already come up with the action plan and resolution. Visit website at https://fuzecard.com/security_notice.html