We all understand the risk of someone taking over our computers or phones for nefarious purposes. But remote access to printers and fax machines was something most people took a little less seriously. After all, you might get some obscene printouts or someone wasting some paper, but in general, those are not big deals. Some researchers however have lately been pondering what might happen should someone break into your 3D printer. Of course, you could bring a printer down to deny service, or cause things to malfunction — maybe even in ways that could be dangerous if the printer didn’t have sufficient safety features. But these researchers are more crafty. They are studying how you know what you’ve printed hasn’t been subtly sabotaged. They also think they have an answer.
If you are printing another Benchy at home this probably isn’t a real concern. However, according to the paper, 3D printing now accounts for over $6 billion of revenue with 33.8% of all parts having some function. This includes a recent FAA approval for a 3D-printed fuel nozzle for a jet engine. So indulge us in a little science fiction. You are about to fly your drone to take video of an important social function. You are worried about one of your props, so you 3D print a new one. Too bad your competitor has hacked your computer with a phishing e-mail and modified your STL files so that the new prop will have built-in weak spots internally. The prop will look fine and you’ll be able to install it. But it is going to fail right when you are taking those critical shots.
Did we say that’s science fiction? Actually, it is only a bit of an embellishment on an actual demonstration attack cited in the paper. So what do you do about it? The proposed solution is an audio fingerprinting method that knows what it sounds like to print the object.
Of course, that fingerprint isn’t going to be perfectly the same every time, so the paper describes how to compare the audio and how certain parameters like microphone location affected results. They were able to detect when things were maliciously modified.
Honestly, to us, this seems like a solution looking for a problem. Despite media hype about the security of 3D printing, the real attack here for most printers is on a computer that is generating the codes destined for the printer. You could also attack anywhere back in the chain. Remember the Ken Thompson hack? You could easily modify a slicer or any other tool in the chain to add your defects.
If you are really worried about this it seems that you would cryptographically sign your STL files, and part of the printing process would be to verify the signature and a digest of the file. That would make much more sense. Can you break a crypto signature? Probably. But it isn’t easy. And we are guessing you could fake out the audio fingerprinting at least as easily.
Still, it is an interesting subject to think about, and more proof that whatever you do, bad guys will find a way to make it a bad thing. If you think only big computers get hacked, think again. Some of these are possible because designers just aren’t paying attention to security.

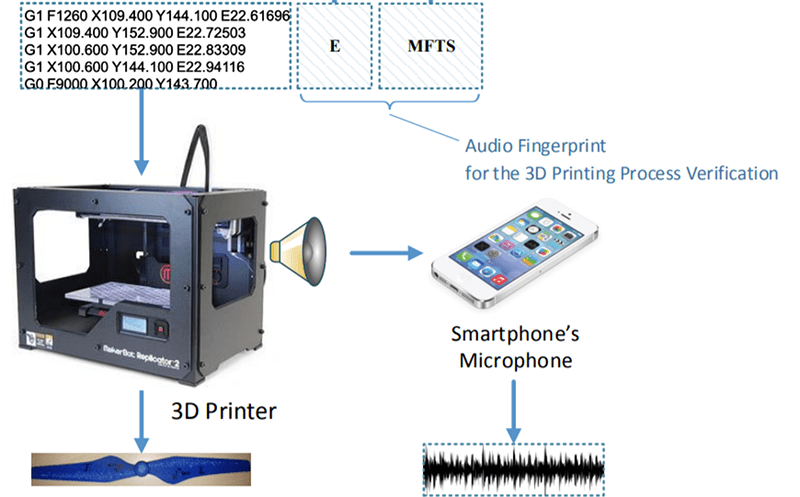














“Some researchers however have lately been pondering what might happen should someone break into your 3D printer. ”
Print obscene things.
I can just imaging it now the kids wonder into my work shop and come out playing with some interesting object they just pulled off the printer …. lol
Joke’s on them, I’m already printing dongs 24/7.
Of course the real concern is whether they can bypass all your thermal runaway protection. If you have an Anet hooked up to a network, then yes, they can literally burn you down.
Back in the day of fax machines every morning we would come in to the office and find a bunch of junk mail faxes laying on the ground. For a few days I decided to strike back since the junk fax’s had a fax number printed on the header I tapes some black paper in a circle as it was feed in to the fax machine and sent it to the sender of all the junk faxes.
It turns out that after talking to a friend from OKI faxes were notorious for burning out their thermal heads when they received continuous black :)
Except, the vast majority of junk faxers didn’t have a human dialling and feeding pages to a fax machine. Much like the people here at HAD, they’d use a computer to do that job. Your all black fax would come into their fax modem and get stored like all the other responses.
Whomp whomp. How can we get back at VOIP spoofers these days? That’s something I’d be very down for.
There was a lawsuit regarding a man who was fed up the auto dealer and the “lemon” he had bought from them.
He sent the dealership a fax (after hours) that had the beginning and end taped together into an endless loop, thereby consuming all the paper loaded into the dealership’s fax machine. The dealership won the lawsuit and a new law criminalizing such action hit the books.
“They are studying how you know what you’ve printed hasn’t been subtly sabotaged.”
Well that’s called quality control and I hope any part that end up in a plane is QC checked and not directly bolted from the printer…
I guess they need the hype and buzz to fund their research for more money
Plan to have a standalone network, not connected to the outside world……
Just like a Jeep Cherokee, oh wait, it has cellular capability built in…
The nuclear scientists in Iran can attest that air-gapping isn’t the end of computer security.
So it’s basically a MD5 Hashsum for the print itself?
Huh … can’t we verify the integrity of the file with proper certifications and stuff and NOT put every single machine on the WWW? Seperate critical machines with hardware barriers. If you Printer is printing critical parts, disconnect it from your network and feed it via USB. get a proper checksum for the file so you know it’s legit and the person mailing you the file via the horrible and dangerous internet can encrypt or secure it.
The article mentioned it: This “solution” is looking for a problem.
Why can’t the hacker change the sounds of the printer aswell or if he can intercept your precious 3d print attachment from the mail, he can do the same with audio and change it.
Consider how many 3D printers have been built with non-standard components, and are continuously modified by their owners. I think an audio file of a printing will be relevant only between the same prints by the same printer.
I imagine even acoustis from the room and placement of the mic would have an effect. You could solve all that fairly easily with auto-calibration, though. Give the acoustic monitoring system control of the steppers for a moment and have it listen to the print head being moved in every direction, then use that data to monitor further moves.
Its a black hat attack but with 3d printers!
Seriously, this solution is pointless because it requires you to have a microphone near your printer at all points in time. This wont be your cellphone on any of the larger prints due to the time length of printing and if the attackers have already found a way to change your stl file (which is dumb and easily checkable in any 3d modeling program) then they are already on your computer and thus can get past this security measure as well.
Also why do they assume that people will go change the STL file, that is the easiest to check! Just load it up into the 3d modeling program of your choice and set the transparency to a level where you would be able to see any holes in the design. Either a serious attacker is going to change the G-code itself or they are going to mess with the printer to destroy the printer. In the first case it seems like a whole lot of effort, more than the amount needed to go after the control systems of the device that is using the printed part in the first place.
Maybe they could use it as a “watchdog” on cheapo printers that have no feedback/sensors to speak of and stop the print if the nozzle is clogged, printer runs out of filament or some steps are skipped? Not the cool 007 scenario, but this could actually be useful.
I was thinking the same thing; if this system can be used to determine if the print head is printing a part as prescribed by the gcode, even being able to reliably detect a defect, then could it not be used in some fashion as a super simple method of closing the loop? Perhaps not the most precise method, but it might be good for certain things like detecting print failures or determining where a failed print left off so it could be resumed.
The malicious attack scenario seems a bit like fantasy, but I screw up my prints all on my own plenty often. Maybe it could be used to further improve that situation as well.
If you get taken down by a phishing email, you deserve what happens to you.