Leading edge computer security is veiled in secrecy — a world where novel attacks are sprung on those who do not yet know what they need to protect against. Once certain tactics have played out within cool kids’ circles, they are introduced to the rest of the world. An IBM red team presented what they’re calling “warshipping”: sending an adversarial network to you in a box.
Companies concerned about security have learned to protect their internet-accessible points of entry. Patrolling guards know to look for potential wardrivers parked near or repeatedly circling the grounds. But some are comparatively lax about their shipping & receiving, and they are the ideal targets for warshipping.
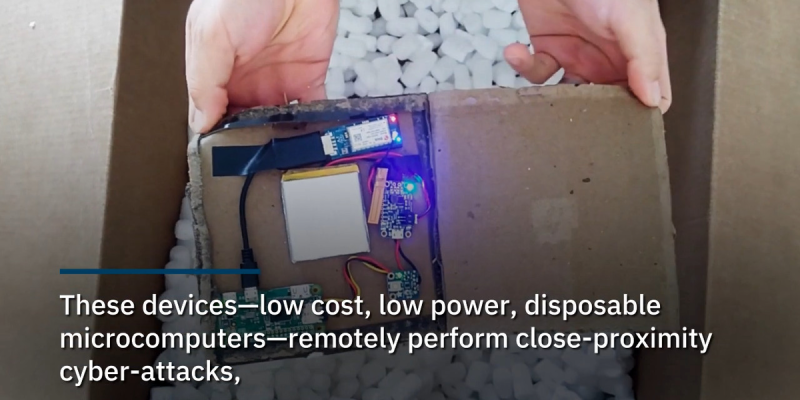
Bypassing internet firewalls and security perimeters, attack hardware is embedded inside a shipping box and delivered by any of the common carriers. Security guards may hassle a van bristling with antennas, but they’ll wave a FedEx truck right through! The hardware can be programmed to stay dormant through screening, waiting to probe once inside the walls.
The presentation described several ways to implement such an attack. There is nothing novel about the raw hardware – Raspberry Pi, GPS receiver, cellular modems, and such are standard fare for various projects on these pages. The creative part is the software and in how they are hidden: in packing material and in innocuous looking plush toys. Or for persistence, they can be hidden in a wall mounted plaque alongside some discreet photovoltaic panels. (Editor’s note: What? No Great Seals?)
With this particular technique out in the open, we’re sure others are already in use and will be disclosed some years down the line. In the meantime, we can focus our efforts on more benign applications of similar technology, whether it is spying on our cat or finding the nearest fast food joint. The hardware is evolving as well: a Raspberry Pi actually seems rather heavyweight for this, how about a compact PCB with both an ESP32 and a cellular modem?
Via Ars Technica.















I could swear I saw this in an episode of Leverage.
Here it is: Season Two, the Top Hat Job.
That’s certainly what I always think about when this topic comes up.
As for the the choice of device, I’d argue that a smartphone of the day would have been more useful than the original Pi (which would have just been released when they made that episode) as it would have had WiFi and cellular baked in, not to mention being more powerful.
Nope, i was wrong. It was a cellphone they used, not a Raspberry Pi.
Interesting but not new. https://thehackernews.com/2013/11/russia-finds-spying-microchips-planted_1.html
Admitted – it’s a (new) variation. But of an old topic.
I think the innovation here is putting it into something flat/cardboard that could be confused with packaging.
For prior art on Trojan Horses, you have to go back to, well, Troy.
The idea is at least 4 or 5 years old. Packaging and all. Hell a few years back a guy rigged up a cat with spark core. And sent it out into the neighborhood. There’s a natural progression to things like this and war Kitty doesn’t come before war shipping in that evolutionary chain.
And to the other comments about how to ship it I’m left wondering if they’ve ever shipped anything, or if perhaps post offices in less rural areas are less tax than I’m used to. But suffice to say plenty of illegal stuff is shipped everyday in the US, without being concealed in plushies or alarm clocks. You weigh the box, prepay shipping and you drop it in a mailbox, whether it’s a cell phone or vacuum sealed drugs, if it doesn’t alert to the automated usual scumbag sensors it’s usually not looked at and as long as you don’t put your name and address on it or do something similarly do something stupid it doesn’t usually show back up at your door with an FBI escort.
The long and short is that the idea has mostly always been to build it into the box or ship a novel alarm clock and a thank you note. Super simple stuff, don’t overthink it. It doesn’t matter if the thing gets thrown away or the battery dies. You’ve paid $50 for potential access to data that could be worth many times that. It’s a cheap gamble. And people making that gamble either aren’t deeply concerned with legality or they’re doing it on company dollar to prove a point (red teams.)
It seems new because it’s so mundane and obvious to professionals that nobody thought it was even worth discussing until now. I’m surprised it’s even come up at all. It’s like an article about the right click function in windows. We noticed, we didn’t feel the need to talk about it…
They’d have to report when a package contains hazardous materials, like batteries. If they don’t, it could be considered a crime. Much worse, if something goes wrong, and one battery catches fire, the man most certainly will end up in jail, aside from his criminal wifi attacks.
It is a crime regardless, the entire premise is to perform either a attack on the network or Snoop on traffic, both of which are illegal, the batteries is a moot point, especially considering blind drop boxes for FedEx ups and USPS, most don’t have cameras, and none of them require I’d to ship
One could always use an older battery technology that’s not considered hazardous to ship.
Cause, ya know, criminals obey and care about breaking the laws…
But who checks if the senders address is valid?
Here in Germany i could easily send of a packet anonymously if i really wanted. Thanks to outsourcing the post office to small private companies, like kiosks and lotto booths, no one of these businesses has the time or even the interest to check if you are really you or remembering you in a few weeks or months. They get paid like 50 €cents per package going trough their shop, not enough to give a crap.
Bundespost got outsourced?
Long ago. Budespost does not really exist anymore. Where I live its all DHL.
Their counter is in the grocerie store and they dont even know how to handle the packages when it say “Dont throw” on all sides.
Seems like domestically (for the US at least), it is relatively easy.
https://faq.usps.com/s/article/Can-I-Ship-Lithium-Batteries
Following the links eventually get to a page “Installed in Equipment.”
Sending lithium batteries is not prohibited, only limited to ground transportation. Although once declared, the package will be labeled specifically to alert that it contains lithium batteries which probably isn’t desirable in these circumstances. But like Taylorian said… if you’re intending to violate laws from the start… an additional violation isn’t likely much of an impediment.
And the notion of tracking it back to an individual through the sending address is kinda ridiculous, since that would be faked anyway. I’ve shipped all kinds of things to all kinds of places all over the world. Never once have I had a postal worker verify that the sending name and/or address matches any kind of official ID.
While it’s true the post office doesn’t demand ID, you aren’t allowed to ship over a certain weight without either metered postage or handing it to a postal worker. And if you hand it to a postal worker in a post office there’s probably video surveillance. It’s not really anonymous if it’s witnessed. Granted, this is more about stopping the next Unibomber, but still.
Can’t you buy a prepaid flat rate box from the post office and drop off the package later on in a regular mailbox?
https://store.usps.com/store/product/shipping-supplies/priority-mail-forever-prepaid-flat-rate-small-box—ppsfrb-P_PPSFRB
“the package will be labeled specifically to alert”
Time for the cheap plush toy to be ‘upgraded’ to a battery powered furby!
Not many would make the connection that the warning and type of batteries actually in a furby differ. So long as the creepy bastard comes to life when turned on, it’s highly likely the box labeling would even be given a thought.
That’s like the getaway driver in a bark robbery shouldn’t speed because he could get a ticket.
woof.
When coupled with RFID this could become particularly problematic. Ping me once, fool you. Ping me twice, phone home.
” There is nothing novel about the raw hardware – Raspberry Pi, GPS receiver, cellular modems, and such are standard fare for various projects on these pages. ”
There are passive ways of blocking such. e.g. Faraday cage. And then there’s light-based ways* of communicating inside a building. Harder to abuse.
*Or short enough wavelength it doesn’t penetrate the room.
Well, running Ethernet into a faraday cage is no problem either if you need a network isolated wirelessly.
I saw a researcher on Twitter pointing out that this is just attacking insecure wifi, and could be done from the parking lot. It would be way more interesting to see attacks against wireless mice and keyboards sent this way.
Ooh yeah add a 2.4ghz SDR and you could get some juicy data
That really depends on the building – a wifi router in the middle of my ‘office’ (which I’m sure is typical of many large combined office/production facilities) would have no chance of reaching the parking lot…and as such might not be secured as well as one might wish it to be.
If the attack is in the packaging that raises the question “When did companies start saving all boxes?” The answer of course is “NEVER”.
It’s probably getting chucked in a bin until somebody goes out to the dumpster. That could be hours or days, which plenty long enough to grab something like a WPA handshake, scan bluetooth for vulnerable devices, sniff 2.4ghz keyboards, etc.
I think I’ll put a dummie wifi in my office, give it something else to infiltrate.
Why do I really want one of these to show up?
Every now and then when I am in a crowd of people (stadium, mall, park) I think of building a dummy wifi, just to see how many would link to it.
(Hey! Someone left their WiFi open! Free Internet!”
The US Postal Authority has one of the highest arrest and conviction records of any law enforcement agency in the United States. I think it wouldn’t be worth the risk sending something like through the mail.
Sounds like I should start a package handling agency that companies can contract with. Get some x-ray scanners and people with the skills to examine the images looking for strange stuff. Questionable packages can be quarantined and handled according to a company’s policy. That big battery seems like it couldn’t be too hard to see.
An interesting next step would be to see how cheap a custom board can be. If power consumption can be lowered even more, then that could open up new battery possibilities. An expendable device doesn’t necessarily need a lithium ion rechargeable battery. Using something like coin cells or AAA cells is probably a stretch, but if they could be used they probably would not raise as much attention depending on how everything is packaged.
Wouldn’t the recipient most likely open the package?
The idea is that it would take some time before someone does open said package when it’s a large organization. Most people these days track packets that they expect and have no idea when something comes without them knowing it’s in the mail room waiting on them to retrieve it. Double points if you address it to someone who doesn’t even work there. It will sit for a very long time.
Put a fake RMA number on it.
If the device was found, the sender/builder would be screwed, I cant see how someone would expect to get away with this if law enforcement got involved. The cellular modem is identifiable by IMEI, which could be traced to the supplier, then vendor and point of sale. Ive not seen anywhere that you could buy one of these in a shop for cash, so bought online would have a record of who bought it and recipient address. Same goes for the SIM card and data plan. Even pre-paid SIMs require ID.
You can definitely still get prepaid SIMs without ID in the US, I’ve done it with cash a few years ago but I doubt it’s changed much. Also if you can design a single side PCB with 0805s for an esp32 and GSM module then it’s pretty easy to fully DIY too without having to order from a fab as long as you have etchant and a laser printer, get the modules from different Chinese sites using different accounts if you’re paranoid enough and of course ship the final box from a drop-off somewhere far from where you live but essentially this can be done pretty untraceably (of course also have good opsec on the receiving end and software).
Good practice too would be including something like an eBay ‘stun gun’ high voltage generator that zaps everything’s power rails through a transistor that gets activated if the box is opened (photoresistor or simple contact switch), and can even be remotely triggered or just done automatically before the battery dies to make data extraction as hard as possible.
Actually there are ways around this. I once invented a “passive” parcel tracker using FM radio station identifier, that does not need a GPS so works even in sealed areas. But a workaround would be to forward it to a second user who installs the card and sends it on its merry way, as they could simply buy this at a shop for cash, activate with burner phone then install.
Note, not fully tested as ran into 4 letter issues but it does work well enough. I tested some aspects using $0.30 FM IC and LEDs as capacitors for the larger values needing temperature stability, it would work with a PIC 10F222 as controller.
Maybe I can repurpose it for locating lost items? Schematics available on request.
Incidentally don’t use a phone battery as Customs *WILL* pick it up. I also found that there are batteries which won’t get you in the merde with C&E and are actually used for things like weather balloons or good old fashioned Zn C
Maybe a homemade Mg ion ribbon battery as these are generally believed to be idiot proof ™ and only 2 cells in series if a good step up regulator running directly on the micro/radio combi @ 3.3V plus run on ambient moisture.
To: OP Maybe in 2013 but they long since got rid of this over here. The reason: people simply buy them somewhere else.
All it did is p*ss people off and make them not visit.
If you want a long-lasting battery and you can deal with an anemic power-to-weight ratio, ‘crystal power cells’ might be the way to go, as they are solid salts and thus almost completely inert.