This deep dive into the Linux-powered Reolink B800 IP camera started because of a broken promise from its manufacturer. When [George Hilliard] purchased a kit that included six of the cameras and a video recorder, the website said they were capable of outputting standard RTSP video. But once he took delivery of the goods, and naturally after his return window had closed, the site was updated to say that the cameras can only function with the included recorder.
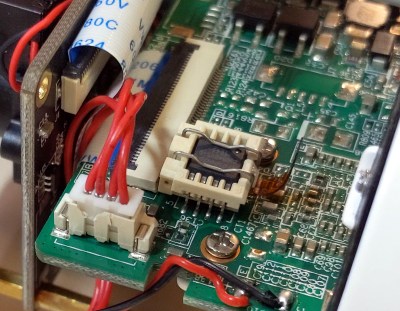 Taking that as something of challenge, [George] got to work. His first big break came when he desoldered the camera’s SPI flash chip and replaced it with a socket. That allowed him to easily take the chip out of the device for reading and flashing as he tinkered with modifying the firmware. After adding cross-compiled versions of
Taking that as something of challenge, [George] got to work. His first big break came when he desoldered the camera’s SPI flash chip and replaced it with a socket. That allowed him to easily take the chip out of the device for reading and flashing as he tinkered with modifying the firmware. After adding cross-compiled versions of busybox, gdb, and strace to the extracted firmware, he bundled it back up and flashed it back to the hardware.
If you think that’s the end of the story, it isn’t. In fact, it’s just the beginning. While getting root-level access to the camera’s OS would have potentially allowed for [George] to dump all the proprietary software it was running and replace it with open alternatives, he decided to take a different approach.
Instead of replacing the camera’s original software, he used his newly granted root powers to analyze it and figure out how it worked. This allowed for to sniff out some very suspect “encryption” routines built into the software, and eventually write his own server side in Rust that finally allowed him to use the cameras with his own server…albeit with a bit more work than he bargained for.
Projects like these are a fantastic look at real world reverse engineering, and a reminder that sometimes achieving your ultimate goal means taking the long way around. Even if you’re not in the market for a hacked security camera, there’s no doubt that reading the thorough write-up [George] has prepared will teach you a few things. But of course, we’d expect no less from a guy who runs Linux on his business card.
















While kudos for using the existing software, and I do get the effort and pain of using your own software, it is sad to see a mother propriatery piece not being liberated. It would have been much nicer to have seen a custom Linux distro that was open for these cameras …
But with, scratch …
Might be due to certain legal issues that “could” arise
Knowing the internal flash layout and the format update format, I probably could provide a firmware update that lets you log in, or even a custom distro. But it would be much harder to use the hardware capabilities of the system like the H.265 encoder since that info is all packed into the dvr binary.
Yeah I figured it was that, so much binary blobbage and zero documentation for linux/android camera stuff, that it comes down to “did you actually want to use your camera at best quality, or did you want a blind dinky linux system.”
This is truly a nice hack for small Linux devices commonly floating around.
Where can I find a good tutorial for Ghidra?
I would try google but you have probability tried that.
Perhaps try asking some Retro game cracking forums?
ik they do a bit reverse enginering for emulators etc.
Damn you autocorrect.
I think the manufacturer will be interested as well. It for sure adds value to their camera.
Seems like they either intentionally crippled their cameras or lied in the product description, I’m not so sure they actually are interested, esp. given the “encryption” part.
They are intentionally crippled, these cameras have an equivalent that DOES output rtsp onvif etc (I know I have two in my system lol) these crippled cameras are sold much cheaper than the full fat versionstho I have no doubt the hardwares identical, if you could just flash the regular firmware you would probably be good to go.
For those reading these reolink cameras, the full fat ones, do not require old IE plugins etc to be configured so perfect for someone like me who uses linux everywhere.
I think if the mfgr finds out, they will change the firmware to thwart this hack from working with future purchases.
(of course, AFTER they call their lawyers!)
I don’t think fly-by-night manufacturers in China care much about added value.
The big question is:
Should you buy this same camera knowing there is a hack or should you reward the brand that cripple the camera?
(for people that bought the camera, they already got your money.)
I was thinking the same thing. Unless the camera is very cheap for the hardware feature set I’d probably stay away.
or jsut buy the uncrippled version, there very reasonably priced, require no IE plugins to configure (i.e you can configure them from firefox/crome in linux) and of all the cameras i have tried over the years , in the sub £100 segment they are one of the best. IMHO ofcourse.
“Should you buy this same camera knowing there is a hack or should you reward the brand that cripple the camera?”
I dunno, ask the people who have bought Rigol O-scopes.
(oh, wait! By posting your question on HaD, you ARE asking those people!)
On a semi-related note, what recommendations are there for cameras and recorders that don’t have questionable security? I’ve looked at the Cloud Key Gen 2 (and related cameras) from Ubiquiti, but they don’t support anything but Ubiquiti cameras (and they seem like they are walling their garden in tighter and tighter, which I don’t like).
Ah, these kind of epic reverse engineering projects are what make my heart sing!
Bravo!
Interesting. Anyone have a list or website characterizing all the choices for open and hi-res security cameras; please post links., including pin-hole cameras and other mixtures.
Why would the stored video files be on anything other that a linux based system’s HD?
Maybe on high bandwidth USB 3+ devices?
Preparing for ports to usb4 should be in the works?’
If I were to contribute code/fixes and other embedded goodies, where should I send such snippets?
Thanks for this thread!
James
I had a similar Reolink camera that never played nice with RTSP (allowing ffmpeg to copy and record the stream). RTSP was unusable but RTMP worked fine.
Assume your runnign zoneminder? I have 2 5mp cams running , both requred tcp transport for the main feed but were happy with UDP for the sub feed. bomb proof reliable. love them. if your on zoneminder read this thread if you have a lot of 2mp+ cameras, it is an absolute godsend. https://forums.zoneminder.com/viewtopic.php?f=9&t=27537