Geosynchronous satellites, girdling the Earth from their perches 36,000 km above the equator, are remarkably useful devices. Depending on where they’re parked, they command views of perhaps a third of the globe at a time, making them perfect communications relays. But as [James Pavur] points out in his DEF CON Safe Mode talk, “Whispers Among the Stars”, geosynchronous satellite communication links are often far from secure.
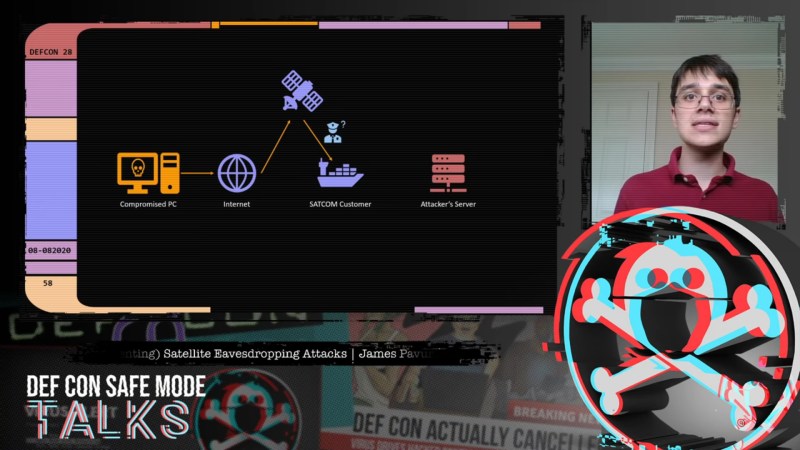
[James], a D. Phil. student in Systems Security at Oxford University, relates that his exploits rely on the wide areas covered by the downlink signals from the satellites, coupled with security as an afterthought, if it was even thought of at all by satellite service providers. This lackadaisical approach let him use little more than a regular digital satellite TV dish and a tuner card for a PC — off-the-shelf stuff that you’d really have to try hard to spend more than $300 on — to tap into sensitive information.
While decoding the digital signals from satellites into something parseable can be done with commercial applications, [James] and his colleagues built a custom tool, GSExtract, to pull data from the often noisy signals coming down from on high. The setup returned an amazing bounty of information, like maritime operators relaying the passport information of crew members from ship to shore, point-of-sale terminal information from cruise ships in the Mediterranean, and in-flight entertainment systems in jet airliners. The last example proved particularly alarming, as it revealed an exploitable connection between the systems dedicated to keeping passengers content and those in the cockpit, which clearly should not be the case.
We found [James’] insights on these weaknesses in satellite communications fascinating, and it’s well worth the 45 minutes to watch the video below and perhaps try these exploits, which amount to side-channel attacks, for yourself.















A most enjoyable talk.
Interesting that the FBI released a notification cited their work weeks before it was published.
How is customers’ failure to follow even the most basic standard cryptographic practices a security failure by the satellite service provider? They deliver your data. If you’re an idiot and don’t encrypt, you deserve what you get. It’s no different from the regular Internet.
Maybe I WANT to stream stuff in cleartext to everybody in the world. How’s the satellite supposed to know that I don’t?
Using satellite internet service to stream content “to the world” intentionally would definitely be interesting use case worth exploring.
I think the only news here is that this still continues to be possible.
This has been a known issue for nearly as long as there has been widespread satellite internet.
A very interesting video. At first, I thought the topic was signal analysis and pulling data out from below the noise floor (as in Dr Joe Taylor’s WSJT, etc), but the topic instead is about the magnitude of unencrypted/freely accessible data available to be intercepted from satellites (security through obscurity). While I’m sure such data gathering is well-known to nation states and many hackers, it was interesting to see it presented all in one place.
Dan,
To be more accurate, the only satellites which are “parked” at the equator (which is the only place in orbit a satellite can be “parked”) are geostationary satellites. Yes, a geostationary satellite is also a geosynchronous satellite, but not all geosynchronous satellites are anywhere near “parked”. The original Sirius Satellite Radio satellites are in a tundra orbit (better reception in northern latitudes than geostationary) which is still geosynchronous. A satellite can be in a polar orbit and still be classified as a geosynchronous satellite as long as it makes a full rotation around the earth once every sidereal day.
When I wrote my previous comment I was busy and hadn’t watched the video yet. I just watched the video and in the video James refers to the satellites as geostationary, not geosynchronous as in the Hackaday article.
Very interesting video. Thanks, HaD :)