Modded Minecraft is having a security moment, to match what we’ve seen in the Python and JavaScript repositories over the last few months. It looks like things started when a handful of burner accounts uploaded malicious mods to Curseforge and Bukkit. Those mods looked interesting enough, that a developer for Luna Pixel Studios (LPS) downloaded one of them to test-run. After the test didn’t pan out, he removed the mod, but the malicious code had already run.
Where this gets ugly is in how much damage that one infection caused. The virus, now named fractureiser, installs itself into every other Minecraft-related .jar on the compromised system. It also grabs credentials, cookies, cryptocurrency addresses, and the clipboard contents. Once that information was exfiltrated from the LPS developer, the attacker seems to have taken manual actions, using the purloined permissions to upload similarly infected mod files, and then marking them archived. This managed to hide the trapped files from view on the web interface, while still leaving them exposed when grabbed by the API. Once the malware hit a popular developer, it began to really take off.
It looks like the first of the malicious .jar files actually goes all the way back to mid-April, so it may take a while to discover all the places this malware has spread. It was first noticed on June 1, and investigation was started, but the story didn’t become public until the 7th. Things have developed rapidly, and the malware fingerprints has been added to Windows Defender among other scanners. This helps tremendously, but the safe move is to avoid downloading anything Minecraft related for a couple days, while the whole toolchain is inspected. If it’s too late and you’ve recently scratched that voxel itch, it might be worth it to take a quick look for Indicators of Compromise (IoCs).
MOVEit
The MOVEit file transfer system is actively being exploited by a zero-day that first showed up on May 27. The initial flaw is SQL injection, and when combined with other weaknesses, allows for full compromise of the MOVEit system. The flaw was patched on the 31st, but several large business and government targets have been hit by attacks.
Researchers at Huntress have pieced together what the attack actually looks like. It looks like the attacker behind the active exploitation is the ransomware group Clop, also tracked by Microsoft as Lace Tempest. I told you Microsoft’s new threat actor names would be hilarious.
Microsoft is attributing attacks exploiting the CVE-2023-34362 MOVEit Transfer 0-day vulnerability to Lace Tempest, known for ransomware operations & running the Clop extortion site. The threat actor has used similar vulnerabilities in the past to steal data & extort victims. pic.twitter.com/q73WtGru7j
— Microsoft Threat Intelligence (@MsftSecIntel) June 5, 2023
Triangulation
Researchers at Kaspersky found indicators of something new infecting iOS devices. This malware was detected via suspicious network traffic originating from iPhones, and appears to be a full blown APT toolkit. Once they knew what to look for, signs of this malware kit could be detected way back in 2019. This appears to be a non-persistent infection, where a reboot does away with the malware. What’s particularly interesting is that network logs showed individual devices being reinfected.
The infection vector for this exact malware seems to be CVE-2022-46690, triggered with an iMessage attachment. It’s a 0-click exploit, but has only been observed infecting iOS 15.7 and older devices. Though with a sophisticated campaign, it’s quite possible that other exploits are in use for other targets.
LastPass Updates
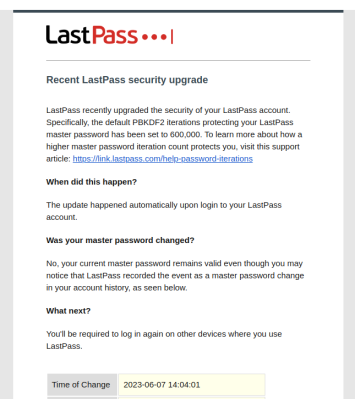
If you have hung on to LastPass, you may have noticed something odd this week, when we were all logged out of our LastPass accounts with an update. The big news here is that LastPass has finally pushed everyone to 600,000 iterations of PBKDF2, the hashing function used to make password cracking much more challenging.
Bits and Bytes
Speaking of passwords, RedTeam Pentesting found a password handling flaw in the STARCACE PBX, and used the opportunity to give a general lesson is proper password handling. Not to give away the punchline, but storing a password hash is less great when using the wrong hashing function, and when the hash itself can be used as a password.
Google has fixed a bug in the Android Mali GPU driver that has been under active exploitation. This issue, CVE-2022-22706, seems to have only been used against Samsung phones, but it’s good to see the fix finally land in Android proper.
And on the browser side, Google security teams have also been busy, fixing a zero-day in Google Chrome. CVE-2023-3079 is a type confusion bug in the Chrome JavaScript engine. As is normal for Google, more details about the vulnerability and campaign are currently unknown.
And last week we covered the disconcerting news that Gigabyte had accidentally left a backdoor in their Windows driver update functionality. The good news is that an update has already arrived to fix the issue. The fixes seem promising, adding signature verification for the files in question, as well as actually turning on certificate checking for the HTTPS downloads in question. It’s still probably a good idea to go turn off the APP Center Download options in your BIOS. But we must give some due credit, that this update was shipped in record time. So for that, good job GIGABYTE.

















@jonathan, a typo in “lastpass updates”? “…haching function…”? ::raises eyebrow:: I find it sad there is sooo little discussion on this column. But then I guess we may all get tired of the “more bad news…’
I keep trying to warn people about public repo software poisoning (aka the Minecraft exploit) and they keep responding to me as if I grew a third head. Sad.
Instead of increasing the rounds for PBKDF2 they should have gone ahead and switch to argon2id.