Hacking — at least the kind where you’re breaking into stuff — is very much a learn-by-doing skill. There’s simply no substitute for getting your hands dirty and just trying something. But that doesn’t mean you can’t learn something by watching, with this root password exploit on a cheap IP video camera being a good look at the basics.
By way of background on this project, [Matt Brown] had previously torn into a VStarcam CB73 security camera, a more or less generic IP camera that he picked up on the cheap, and identified a flash memory chip from which he extracted the firmware. His initial goal was to see if the camera was contacting sketchy servers, and while searching the strings for the expected unsavory items, he found hard-coded IP addresses plus confirmation that the camera was running some Linux variant.
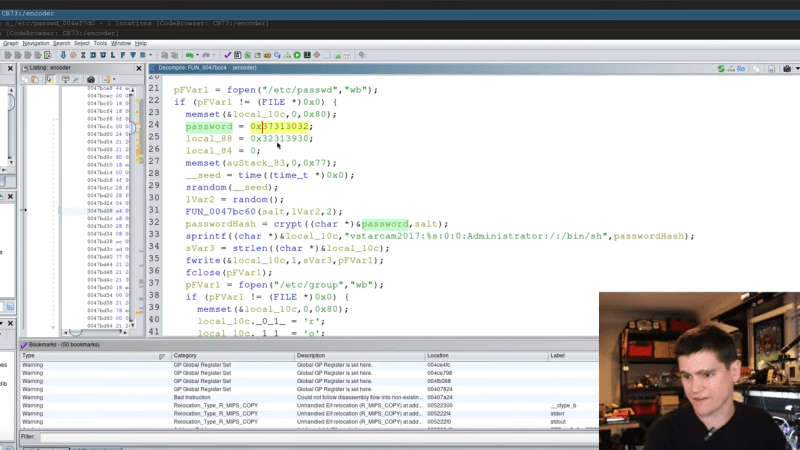
With evidence of sloppy coding practices, [Matt] set off on a search for a hard-coded root password. The second video covers this effort, which started with finding UART pins and getting a console session. Luckily, the bootloader wasn’t locked, which allowed [Matt] to force the camera to boot into a shell session and find the root password hash. With no luck brute-forcing the hash, he turned to Ghidra to understand the structure of a suspicious program in the firmware called encoder. After a little bit of poking and some endian twiddling, he was able to identify the hard-coded root password for every camera made by this outfit, and likely others as well.
Granted, the camera manufacturer made this a lot easier than it should have been, but with a lot of IoT stuff similarly afflicted by security as an afterthought, the skills on display here are probably broadly applicable. Kudos to [Matt] for the effort and the clear, concise presentation that makes us want to dig into the junk bin and get hacking.















Not unexpected … The only cheap camera I have was found to have telnet ports open and a hardcoded root password – it was blank. it accepts a change via passed, until reboot when it becomes blank again.
“until reboot when it becomes blank again”
That’s the “anti-lockout” feature. 🤔
When the article said “cheap”, I figured $15 max, but no, this camera sells for between $25-$37!
That’s close to the price of a low-end “real” security cam, and as much or more than Wyze/Dafang cams, which, while questionably secure in large part due to their cloud services, you can at least make relatively secure by blocking their Internet access, or even flashing custom firmware onto them.
I guess the extra money went towards putting in a battery, but battery powered security cams are generally not a great option to begin with, unless you hook them to solar, and even then, the recording restrictions still make them a less than great option.
In developing countries where 24/7 electricity isn’t guaranteed, battery-powered security cameras hooked up to solar are the norm.
Funnily enough this morning I was just checking if free TP-Link C200 is worth picking up and found https://github.com/nervous-inhuman/tplink-tapo-c200-re even has hidden wired ethernet port, but sadly 15fps max.
damn, autocomplete pasted wrong nickname from remembered selection. Im sorry feipoa for accidental impersonation.
I have one of these, got it free from some promotion or something, probably an internet or phone contract renewal.
Needless to say, as soon as I saw the need for a proprietary app, it stayed firmly sealed in its box.
Maybe if someone can make a clean firmware that allows local use via RSTP, I might be able to put it to use.
The thing is so cheap it’s basically not even worth reselling…..
As is often said, the “S” in IoT stands for ‘Security’.
There is no “S” in IoT, so does that mean there is no Security ?
Internally originating Threat
You have successfully found the pun
Looks like they have a fallback pin in case some deletes the /etc/passswd fike. So as long as thhats there,no worries right? :p now that 7102 would take a very lobg time to brute force…
Hard-coded passwords are a form of ID-IOT (hyphen is redundant).
I bought a couple silly things from Temu not long ago, one of them was a little camera. Everything else was fine but when I took the camera out of the box I asked myself, “do I really want to plug this thing into my computer?”
The answer is “No” and I’ll be tossing it in the trash ASAP.
Oops, the above comment was meant to be at the bottom of the thread.
Apologies if this is covered in the video, don’t have the time to watch it at the moment, but the real question is what can be done with this password?
If we’re talking about remote access to every unit via some publicly accessible API, that’s very very bad. If we’re talking about remote access when on the same network / when the camera isn’t behind a firewall or reasonable network security, well, that’s still pretty bad.
However, if we’re talking about getting root over a local serial console only, with no (known / obvious) remote entry paths, I’d argue that it’s good — as the saying goes, there’s no assumption of device security when the attacker has physical access anyway, and for people who want to modify or repurpose their own hardware, being able to get root locally is a strong benefit, not a drawback.
As an aside, I’ve worked on IoT-adjacent projects where I argued against implementing any of the SoC’s supported secure boot features, on the grounds that I didn’t philosophically agree with locking people out of hardware that they bought, or bricking every device sold in the event that the company went out of business or decided to drop support for that project.
I’m a big fan of this mindset. Remote access should be locked down to protect the user. Physical access should be granted to enable the owner.
At the very least if they don’t want to give access to their own code then some kind of “wipe” button to grant me access to the hardware and delete all the code.
yeah, the trouble is, this is typically something you install outdoor, and it sounds like you can start a telnetd with physical access, which possibly might stay hidden for long and remote controlled via wifi… possibly…
The camera referenced here is definitely not an outdoor unit, though. And really, if someone can dismantle your outdoor security camera, get a root shell reconfigure it and put it back in service without detection… there may be other issues at play!
Agree completely. This reminds me of an Alexa issue where it was claimed that hackers could gain access to your Alexa device, but turned out that they would have to have physical access, open the unit, and solder a jumper wire (or some other physical mod to the device).
While I fundamentally agree with you, the truth is, a lot of rules are on their way to nake things like secure boot mandatory (RED directive etc). The better option would be to put the signong kets in escrow. The upside is well have quantum computing soon so we can do a database with all keypairs :) jokes aside, we can atleast do spmethong at some ppint. Far far from useful, i agree.
Just assume all devices will contact the Chinese mothership or are easy to access. I have all of my security cameras on a network that’s not routable to the Internet or my LAN. Networking 101.
i know this isn’t applicable to everyone but i’m crazy about how many things can be resolved by not giving a hoot.
i was able to effortlessly get an mjpeg stream out of my cheap ipcam, so i don’t need to hack it.
i don’t point it at anything private, so i don’t mind if anyone else hacks it.
if you believe in privacy, all sorts of things can stress you out. but once you accept that privacy is obsolete, bliss descends upon you :)
I have one Tapo C210. Since it has movement, it is by default looking at the wall. Only when enabled through home assistant it points to the scene of interest. I’m not skilled enough to do anything else, but after reading this article and the comments, I may try harder.