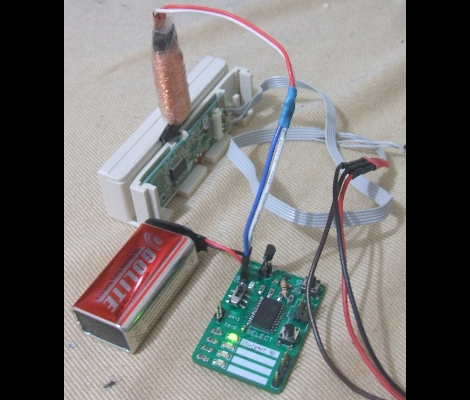
[Samimy] has put together this really neat video tutorial on building a Radio Controlled secure hard drive. How can a hard drive be radio controlled? That’s the first thing we thought too. He has torn apart a remote-controlled car and is using the guts to remotely switch on power to the drive. This means that the drive is only active if you boot the computer after you put the fob in the hidden security system. It looks like it would be fairly effective. We’re curious though, if he is putting the entire drive assembly inside his PC, why rely on batteries for the circuit? Why not pull from the PC power supply? Another neat upgrade might be connecting to an internal USB connection on the motherboard so a reboot isn’t necessary.
Check out the entire video after the break.
Continue reading “Radio Controlled Hard Drive Security”