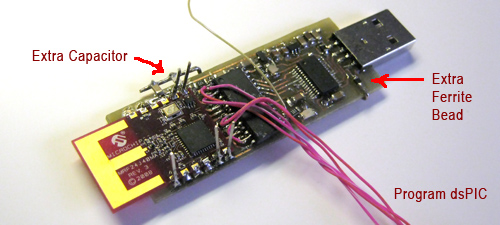
Sending data from a microcontroller to a PC usually requires some sort of serial connection, either through fiddly on-chip USB, FTDI chips, or expensive radio ICs. [Scott] didn’t want to deal with this when creating a network of wireless temperature sensors, so he hacked up a few cheap 433 MHz radio transmitters and receivers to transmit data to a PC for about $3.
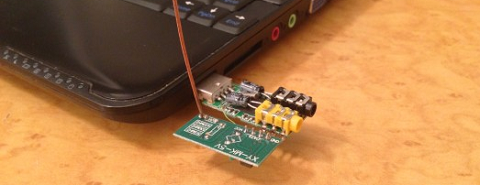
After sensor data is collected on a microcontroller and sent over radio, there’s still the issue of getting it into a PC. For this, [Scott] piped the data into the microphone port of a cheap USB sound card. We’ve seen this trick before both in the world of microcontrollers and loading programs onto a Commodore 64 via a cassette interface.
Once the data is sent into the sound card, it’s decoded with a a small Python app. Given the range and quality of the RF transmitters and receivers [Scott] says it’s not an extremely reliable way to send data to a PC. It is cheap, though, and if you need to read sensors wirelessly on a budget, it’s hard to do much better.
Check out [Scott]’s demo of his creation below.
[youtube=http://www.youtube.com/watch?v=GJHFldPwZvM&w=580]