Europe has been in COVID-containment mode for the last month, in contrast to the prior three months of serious lockdown. Kids went back to school, in shifts, and people went on vacation to countries with similarly low infection rates. Legoland and the zoo opened back up, capped at 1/3 capacity. Hardware stores and post offices are running “normally” once you’ve accommodated mandatory masks and 1.5 meter separations while standing in line as “normal”. To make up for the fact that half of the tables have to be left empty, most restaurants have sprawled out onto their terraces. It’s not really normal, but it’s also no longer horrible.
But even a country that’s doing very well like Germany, where I live, has a few hundred to a thousand new cases per day. If these are left to spread unchecked as before, the possibility of a second wave is very real, hence the mask-and-distance routine. The various European COVID-tracing apps were rolled out with this backdrop of a looming pandemic that’s tenuously under control. While nobody expects the apps to replace public distancing, they also stand to help if they can catch new and asymptomatic cases before they get passed on.
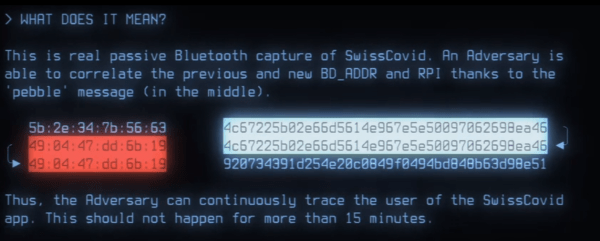
When Google and Apple introduced their frameworks for tracing apps, I took a technical look at them. My conclusion was that the infrastructure was sound, but that the implementation details would be where all of the dragons lay in wait. Not surprisingly, I was right!
Here’s an update on what’s happened in the first month of Europe’s experience with COVID-tracing apps. The good news is that the apps seem to be well written and based on the aforementioned solid foundation. Many, many people have installed at least one of the apps, and despite some quite serious growing pains, they seem to be mostly functioning as they should. The bad news is that, due to its privacy-preserving nature, nobody knows how many people have received warnings, or what effect, if any, the app is having on the infection rate. You certainly can’t see an “app effect” in the new daily cases rate. After a month of hard coding work and extreme public goodwill, it may be that cellphone apps just aren’t the panacea some had hoped.
Continue reading “COVID Tracing Apps: What Europe Has Done Right, And Wrong” →