The Da Vinci 3D printer is, without a doubt, the future of printing plastic objects at home. It’s small, looks good on a desk, is fairly cheap, and most importantly for printer manufacturers, uses chipped filament cartridges that can’t be refilled.
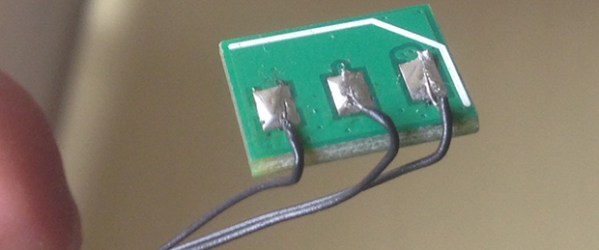
[Oliver] over at Voltivo was trying to test their new printer filament with a Da Vinci and ran head-on into this problem of chipped filament. Digging around inside the filament cartridge, he found a measly 300 grams of filament and a small PCB with a Microchip 11LC010 EEPROM. This one kilobyte EEPROM contains all the data about what’s in the filament cartridge, including the length of filament remaining.
After dumping the EEPROM with an Arduino and looking at the hex file, [Oliver] discovered the amount of filament remaining was held in a single two-byte value. Resetting this value to 0xFFFF restores the filament counter to its virgin state, allowing him to refill the filament. A good thing, too; the cartridge filament is about twice as expensive as what we would normally buy.