
Possible Entrapment Scenario In Hacking Case



[pdp] provides some perspective on the news regarding the GIFAR attack developed by researchers at NGS Software. As he explains, the idea behind the attack, which basically relies on combining a JAR with other files is not new. Combining JAR/ZIP files with GIF/JPG files will create hybrid files with headers at both the top and bottom of the file and allow them to bypass any image manipulation library as valid files. While tightened security and more stringent file validation practices are advisable, the problem is larger than just a vulnerability in browser security. ZIP is an incredibly generic packing technology used everywhere, from Microsoft files to Open Office documents, and of course, in JAR files. He closes with, “any file format that is based on ZIP, you allow your users to upload on your server, can be used in an attack”
[photo: Jon Jacobsen]
Security-Hacks has a great roundup of essential Bluetooth hacking tools. As they point out, Bluetooth technology is very useful for communication with mobile devices. However, it is also vulnerable to privacy and security invasions. Learning the ins and outs of these tools will allow you to familiarize yourself with Bluetooth vulnerabilities and strengths, and enable you to protect yourself from attackers. The list is separated into two parts – tools to detect Bluetooth devices, and tools to hack into Bluetooth devices. Check out BlueScanner, which will detect Bluetooth-enabled devices, and will extract as much information as possible from those devices. Other great tools to explore include BTCrawler, which scans for Windows Mobile devices, or Bluediving, which is a Bluetooth penetration suite, and offers some unique features like the ability to spoof Bluetooth addresses, and an L2CAP packet generator. Most of the tools are available for use with Linux platforms, but there are a few you can also use with Windows.
[via Digg]
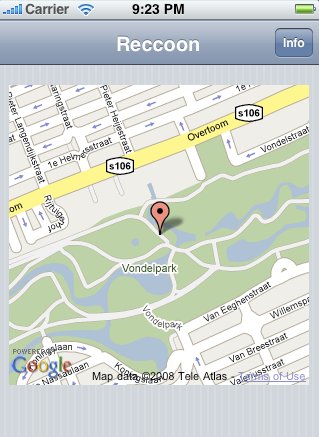
[Dominiek ter Heid] wanted to prototype an application for the iPhone that incorporated GPS. He experimented, and came up with a step-by-step tutorial on how to create a web application that would push GPS information to his iPhone through the use of JavaScript and AJAX. This tutorial will save web hackers who want to play with the iPhone 3G a lot of grief. Using Cocoa Touch, and a CSS/JavaScript pack called IUI, he successfully created a web application that looks native to the iPhone and is able to grab GPS information. The application integrates the GoogleMaps API with the GeoNames database. We look forward to seeing the types of creative applications that this prototype will inspire. What sort of web application would you want to create for the iPhone?
[via digg]

In the aftermath of [Terry Childs], the jailed disgruntled software engineer who created a God password and effectively locked San Francisco officials out of their own computer system, IT Grind unveils its Techie Hall of Shame. The Hall of Shame highlights figures who give computer professionals a bad name. From [Roger Duronio], the systems administrator who wasn’t satisfied with his raise, to [Kenneth Kwak], who installed spyware on his boss’ computer in order to gossip, the wrath of the IT professional can wreak thousands to millions of dollars of damages for companies and corporations to clean up. As much as these figures seem to be singular figures, we think they also serve as cautionary tales. Always have backup. If you suspect you’ve got a disgruntled employee, you should probably at the very least keep another expert eye on him. And hire more than one person to manage your systems. [Deb Perelman] asks her readers who else they think would be worthy of the Hall of Shame. We’re curious to know what you think, too.
[via digg]
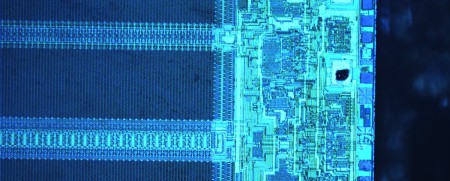
Have you ever wanted to break open your IC and see where those pins really go? [nico] goes through his process of dissolving ICs to their core and photographing the tiny die. The technique involves liquefying the package in sulfuric acid until all the packaging material and pins are gone. He even explains how to use sodium bicarbonate (common baking soda) to neutralize the solution thus allowing for simple sink disposal. Although silicon hacking is generally done by funded hackers with a really nice lab, it is certainly possible to execute some of these techniques with limited equipment and chemical access. For instance, if you can’t get sulfuric acid, send your IC off to a failure analysis lab like MEFAS. For more information and stories on silicon hacking, check out [Chris Tarnovsky]’s process for hacking smartcards and [bunnie]’s talk Hacking silicon: secrets behind the epoxy curtain.

The court cases against high profile hackers [Gary McKinnon], [Gregory King], and [Robert Matthew Bentley] all had major developments last week, with [King] and [Bentley] sentenced to time in prison and [McKinnon] in a tenuous
state fighting extradition.
Both [King] (aka Silenz) and [Bentley] (aka LSDigital) will serve time for crimes related to botnets, but where [King] used one to stage DDOS attacks, [Bentley] used them to create spam. [King]’s botnet had 7,000 nodes, and though the court did not release the size of [Bentley]’s botnet, all of his bots were computers in the Rubbermaid company. [King] agreed to a two-year sentence, while [Bentley] was sentenced to 41 months.
[McKinnon] (aka Solo) who is of British origin, may serve up to 60 years in prison for mounting the “biggest military hack ever” on U.S. government computers. Between 2001 and 2002, he allegedly hacked into 97 computers in U.S. military and NASA networks. To be charged in American courts, though, he would have to be extradited first, and his extradition appeal to British courts is currently pending.