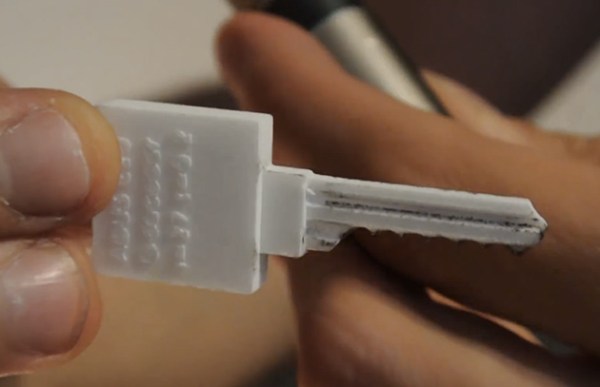
Getting past a locked door is easy if you have the right tools. It’s just a matter of knowing how to adjust the pins inside to an even level while turning the mechanism at the same time when everything is perfectly in place. That’s the beauty of a bump key. You never have to see the actual key or what it looks like. And with a simple hit to the back of the key, and bumping it just enough, the lock can magically be opened.
Lock picking items like this can be ordered online for a couple of dollars, or as [Jos Weyers] and [Christian Holler] showed in a recent Wired article, alternatively you can print your own at home. The video of these 3D printed keys (which can be viewed below) attempts to prove that a person can unlock a door with plastic, which was a little bit surprising to us because it seems like the edges would break off right away. But as it turns out, a thin plastic bump key can be made and does function. Not sure how long these keys can last though, but sometimes all you really need is a one time use when trying to open a specific, tricky lock.
As the article states, “Weyers and Holler aren’t trying to teach thieves and spies a new trick for breaking into high-security facilities; instead, they want to warn lockmakers about the possibility of 3-D printable bump keys so they might defend against it.” Although this information is geared towards lockmakers, we see our Hackaday readers finding this data useful as well. Organizers of hackerspaces who hold regular lock-picking events might want to print their own keys and teach classes centered around security. The uses for this are boundless in regards to educating the public about how locks truly work.