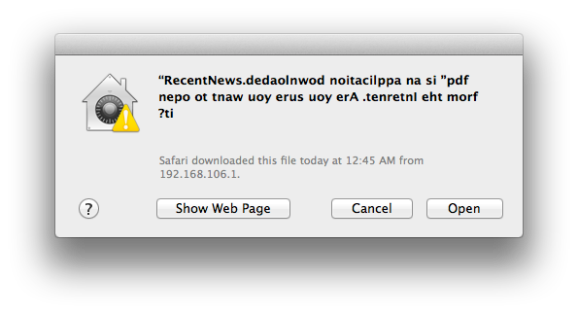
Check out this jumbled confirmation window. At first glance the message appears to contain a bunch of gibberish, but it can actually be read if you start at the right side and read each character moving left. The text displays like this because it is prefixed by a special Right-to-Left override Unicode character. The technique is being used in malware to obscure the actual extension of the file being launched. Notice that when written backwards your eye can still pick out the string “pdf” which may be enough to trick the uninitiated into approving the launch of the file.
This confirmation screen is launched when clicking on a piece of malware found in the wild a little over a week ago. If you do choose to run it, a decoy PDF file is opened in order not to arouse suspicion. But at the same time the program — which is signed with an Apple Developer ID — is installing itself in the home directory and making a cron job to launch at each boot. Sneaky!
















