
With each passing day the rate we acquire digital media increases (we don’t even bother unpacking our CDs when we move anymore). Large publishers have started moving away from DRM, which means we’ll be buying even more digital media in the future. Acquiring all of this nonphysical property puts importance on not just making it easily accessible, but also protecting it from destruction. Slashdot asked for reader suggestions of what NAS to buy; we’ve compiled some of the options below and want to know what you use.
slashdot11 Articles
Neutering The Apple Remote Desktop Exploit
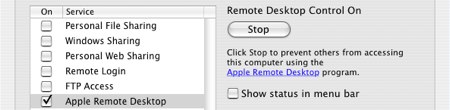
Yesterday, Slashdot reported a privilege escalation vulnerability in OSX. Using AppleScript you can tell the ARDAgent to execute arbitrary shell script. Since, ARDAgent is running as root, all child processes inherit root privleges. Intego points out that if the user has activated Apple Remote Desktop sharing the ARDAgent can’t be exploited in this fashion. So, the short term solution is to turn on ARD, which you can do without giving any accounts access privileges. TUAW has an illustrated guide to doing this in 10.4 and 10.5.
Wireless Hacking With The OLPC XO

Not even a week ago we asked what we should do with our OLPC XO. InformIT’s [Seth Fogie] has written a great two part article that covers turning it into a hacker toolkit. Part one is an overview of the OLPC, how to upgrade it, and do some usability tweaks. Part two covers installing Nessus, Metasploit, and doing some wireless sniffing. We’ll be building our own little green monster based on this and let you know how it goes.
[via Slashdot]
Phlashing Denial Of Service Attack, The New Hype

Imagine how surprised we were to discover that by accidentally bricking our router we were executing a brand new attack: Phlashing Denial Of Service (PDOS). This week at EUSecWest, researcher [Rich Smith] will present the theoretical PDOS attack. Instead of taking over control of an embedded system, the attacker turns it into a nonfunctioning brick by flashing it with a broken firmware. Anyone who has flashed a device knows the danger of interrupting the procedure.
Continue reading “Phlashing Denial Of Service Attack, The New Hype”











