We’ve all seen the social logon pop up boxes. You try to log into some website only to be presented with that pop up box that says, “Log in with Facebook/Twitter/Google”. It’s a nice idea in theory. You can log into many websites by using just one credential. It sounds convenient, but IBM X-Force researchers have recently shown how this can be bad for the security of your accounts. And what’s worse is you are more vulnerable if the service is offered and you are NOT using it. The researcher’s have called their new exploit SpoofedMe. It’s aptly named, considering it allows an attacker to spoof a user of a vulnerable website and log in under that user’s account.
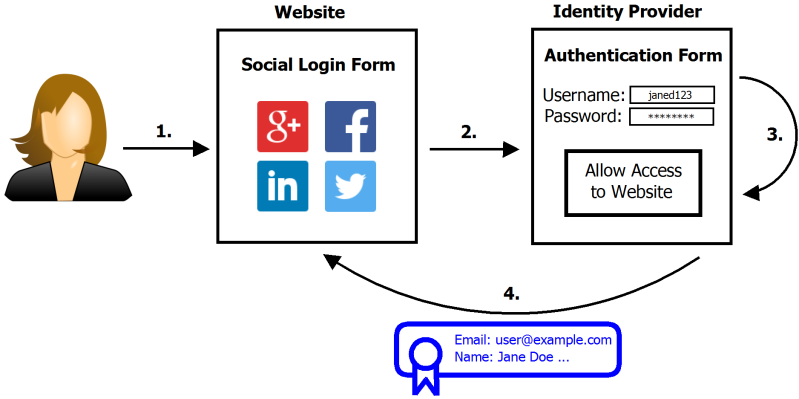
So how does it work? The exploit relies on vulnerabilities in both the identity provider (Facebook/Twitter/etc) and the “relying website”. The relying website is whatever website the user is trying to log into using their social media account. The easiest way to describe the vulnerability is to walk through an example. Here we go.
Let’s imagine you are an attacker and you want to get into some victim’s Slashdot account. Slashdot allows you to create a local account within their system if you like, or you can log in using your LinkedIn account. Your victim doesn’t actually have a LinkedIn account, they use a local Slashdot account.
The first step of your attack would be to create a LinkedIn account using your victim’s email address. This needs to be the same address the victim is using for their local Slashdot account. This is where the first vulnerability comes in. LinkedIn needs to allow the creation of the account without verifying that the email address belongs to you.
The second step of the attack is now to attempt to log into Slashdot using your newly created LinkedIn account. This is where the second vulnerability comes in. Some social media services will authenticate you to websites like Slashdot by sending Slashdot your user information. In this case, the key piece of information is your email address. Here’s the third vulnerability. Slashdot sees that your LinkedIn account has the same email address as one of their local users. Slashdot assumes that LinkedIn has verified the account and permits you, the attacker, to log in as that user. You now have access to your victim’s Slashdot account. In another scenario, Slashdot might actually merge the two credentials together into one account.
What’s really interesting about this hack is that it isn’t even very technical. Anyone can do this. All you need is the victim’s email address and you can try this on various social media sites to see if it works. It’s even more interesting that you are actually more vulnerable if you are not using the social logons. Some real world examples of this vulnerability are with LinkedIn’s social logon service, Amazon’s service, and MYDIGIPASS.com’s service. Check out the demonstration video below.















I saw this coming so I have never used or implemented OAuth. Entity security is a constant battle between actual security level and user convenience. It the convenience of OAuth that has made it popular and not the security. Tokenised authentication can never work with a single verified token (the email address in this case). Paypal has some weaknesses like this to.
This is not very hacker’ish for our type of hackers here but a suppose most of the visitors here have many online accounts.
Now that most people have mobile devices with touch screens, it would be much better to have an app that will convert gestures to encryption keys. The same software that is used for generating algorithms from finger prints would be ideal.
People would be more creative and find it easier to remember gestures rather than meaningless passwords. A password really does need to be meaningless before it is useful.
I had to clean up the mess left by a (real) hacker last week. They deleted the backend database and the account owner had not made a backup so I had to work with raw data and massage it into a shape that would fit into MySQL.
I went right through the server config and everything was fine. The entry vector was a weak password. A couple of days later I found out that the same hacker had taken over another six or so accounts. The other accounts had the same password and it hadn’t been changed. An account is a website, or perhaps a small number of websites for those not familiar.
Internet security by the most part is just a perception and a false one at that.
My advice to people is to never assume anything is secure. Instead think about what it is going to cost you if it’s not. If you could loose $10 and the risk is worth it for you then go for it. If it’s a large cost (money or privacy) then find an alternate means. We could do all of these things before the internet.
MEGA creates encryption keys by having you play a game and recording the mouse movements.
It’s pretty neat, but I don’t know how effects it is.
OAuth has nothing to do with this; OAuth’s primary purpose is to allow users to permit other sites to access APIs for their account; it’s (mis)used as federated login by sites like Twitter.
More to the point, OAuth doesn’t rely on email address; this is up to the sites in question making unwarranted assumptions about the level of verification the authenticating party has performed, and is outside the OAuth mechanism.
Thank you, I have just been searching for information about this topic for a while and yours is the greatest I have found out so far. However, what in regards to the bottom line? Are you positive in regards to the supply?
I have over 500 email aliases because I don’t trust anyone to not sell / loose my email address to spammers and I like having the ultimate control of just revoking an alias at any time. Now i’m screwed because i haven’t already setup accounts for every alias on every oauth provider site. BLEH :(
Thanks for f*cking me again LinkedIn
Having 500 email aliases sounds like a lot of hassle for no real gain. I use my regular gmail account for basically everything since gmail was invite-only, and I think that I don’t even see one spam mail per week. Google is really good of kicking the crap mail into the spam folder….
Can be very easy if you own the domain and choose the right hosting service. 500 gmail/yahoo accounts etc… would probably be a pain in the backside. But I imagine you could script the creating and configuration of accounts if you wanted to. have them all forwarding to the one you actually want to manage and if any of the email addresses ‘goes bad’ you can delete that account.
It is quite easy with no scripting if you have a catch-all address. Though it literally will catch everything. 20k spam messages per day to now “valid” accounts that would have previously bounced. But thats nothing gmail’s filters can’t handle. Spamassassin though will choke and run your cpu usage to 100% on a recent i7, and still be unable to ever complete the mail queue, and then you’ll be stuck with an ever growing delay in incoming email.
But, that being said, you can then just create new accounts like fullofit.bestbuy[at]mydomain.tld and know that there is a good chance that any email that only hits that address is because of bestbuy. I’ve caught retailers selling customer databases through bankruptcy sales by using unique addresses when I signed up for their rewards program. I’ve detected Paramount (Star Trek Online) getting their customer database hacked TWO YEARS before they admitted it happened. If you do go the catch-all route it is a good idea to create a few filters, such as to flag addresses containing some threshold of valid hexadecimal. 90% of the spam I receive is to addresses like e453ab827ac934fde1[at]mydomain.tld with around 100 copies of each message to different hexadecimal addresses.
So basically a catch-all address is an open invitation to get spammed since no mail ever gets rejected or bounced. :-)
But why do you care whether a particular site sells the database? Of course it’s annoying, but the deed is already done and unless you actually take the legal route and sue them for breach of contract and get some kind of compensation it’s merely a “fun fact” to know who the culprits are.
It’s a strange thing with the hex addresses though – any idea why the spammers sends to them?
you can do that with gmail bestbuy+youremail@gmail.com but I’ve found that a lot of the scripts that check for valid emails throw the “+” as an invalid email :(.
No idea about the random hexadecimal addresses, doesn’t seem to have any rhyme or reason behind it. Seems kinda silly for them to do that, almost like some spambot was written by an idiot who cut & pasted a dictionary + md5 hash password bruteforcer without thinking about it. Another nusance is most sendmail / exim configs out there will allow unauthenticated local mail (bob@mydomain.tld to jane@mydomain.tld) even when authentication is supposed required. So now you have spam getting to your users with valid dkim and spf.
The hex addys are from the email headers. They look like valid email addresses to the scrape script. It gets added to a database. Resold. Traded. Etc.
In theory you might be able to match the hexcode of your emails and see which friend lost your email address.
no no I ve been doing this for years and years and no spam at all . the trick is simple :
you make the catchall not a local account but a forward to some real ISP. this way hackaday@somesite.com will go to myreal@myisp.com and the ISP use huge spam filters. This way I NEVER ever get spam. and those I get I can identity who is the culprid as I use a special email to each site, so if hackaday@myemail sell this email and I get spam to hackaday@myemail I know hackaday sold my email.
And with a catch all you never have to manually setup alias. Some wehosting company dont allow catchall email type nor forwarding from catchall so please check first.
I do own my own domain and I don’t run any spam filtering software because I can’t be bothered to learn how SpamAssasin works. I can be bothered to ssh in and add an entry to /etc/aliases each time i sign up for something and also to keep a slip of paper in my bill fold for when clerks in stores ask me for an email address. It takes all of 7 or 8 seconds per signup event.
Regardless of how “good” gmail spam filtering it’s never perfect and if they have your address then they have your address and you’ll get spammed every time they find a way around the filters. If you have one “catch all” address then that’s really no better than just giving out your real address because if you have to nuke it you have to change your email address on every service.
I do want to know who sells my address, because I don’t want to do business with them anymore.
Let me relate my experience with a domain and a catch-all address.
The positive side has already been stated: each time I register with a service or fill in a form I invent on the spot a new e-mail address, which usually contains the name of the service. I don’t have to create anything on my server thanks to the catch-all address.
The negative side should be the spam, as David Kuder mentions the possibility of getting 20k spams per day! But in reality I get 0 spam per day. When I do get a spam, it’s either because someone has been hacked or has sold my e-mail address. The offending address is then quickly revoked. I rarely get spam with “guessed” e-mail addresses… The only thing I’ve done to avoid spam is to point to DNS blacklists in my mail server’s configuration file.
like I said in my other post I never get spam and also I remember that one reason people with catcall might get spam is because they dont make their domain information on the whois private and anonymous.
Domain I use for catchall have all whois data unavailable. Spammer use whois database to mine new domain name. all in all I’m sorry to tell you but I never get spam on my catch all account and I ‘v been doing this since 1996 with many different domains. besides using the names of the website you visit in the email probably trigger the “unlist script” when spammer are making their list. so if you have your own server go ahead do it you’ll see how great this is.
also outlook permits you to send from “other email” via “some account”. this way you can setup your a real imap/pop account postmaster@mydomain and then if you need to send an email to a website from which you registered as lets say hackafay@mydomain, outlook let you type under your account “postmaster@mydomain” the email manually. therefore it looks like its a real account and it never goes into the spam folder of the recipient.
Or as I said earlier just forward the catchall to your real email ISP to profit from their antispam system.
skrill(dot)com resell your email to many casino website I was able to put their nose in the dirt because I used a special email for their site . Once you feel like an address has been sold and is therefore corrupted with spam ; easy : you make rules in outlook to ignore any mail that is adresses to skrill@mydomain, or if you own your server you create a rule to disregard any mail addressed to that email. This way you never “burn” the real email cactch all email.
I really couldnt “live ” without catchall , it’s so great. when you meet someone, or in business and they as for your email, you can imagine anything right from the top of your head just like that, and then with rule in outlook you can categorized very easily . thats the best way to me to handle emails. Of course you need to super secure the password and connection of the main account and use SSL for outcoming and incoming mails as all your mails goes to the same account.
One other tip against spam with catchall : dont use the domain for anything else than mail. It means you need a domain with no info on whois, but also not have any website on that domain or any other service; a dedicated domain for all your emails. could be your lastname for business or anything. When OVH decided to remove catchall possibility to their hosting plans I just cancelled my account. Actually I do catchall from domain that goes to catchall to others domain this way I cant miss a thing and dont have to connect to many imap server . and still I can vow on bible or whatever that I dont get spam. hope this help. seriously give it a try its a life changing thing :)
This always seemed obvious to me. You can’t see a green padlock ensuring SSL from a third party site. In addition it just feels wrong in my bones.
That has nothing to do with it, the real problem is websites automatically associating an OAuth account with your account without requiring you to login locally to their site and verify you want to allow that token. GitHub and BitBucket get it right, you must be logged in already to associate a new token with your account, and you can revoke a token easily.
The main problem is this story is, that Slashdot doesn’t ask for the credentials of the local account before allowing to log in with the LinkedIn Login for the first time.
One thing to never ever do. If you’ve posted an ad to give away or sell an item on craigslist or anywhere else online, and someone contacts you by text message about it… Don’t fall for them asking to enter a code when you get a call to verify you a real person.
They want to verify your phone number with Google Voice so they can set up call forwarding from the GV number to your number. I got stung on that by some scammer posting fake ads for rental houses and apartments in various very expensive cities in Florida like Boca Raton, Delray Beach, Coral Gables and others.
If cell phones had hooks, mine would have been ringing off it. Was extremely annoying since I’m in Mountain time zone. I told a lot of people those ads were scams. I also got two of the scammer’s hotmail accounts nuked, at least two of his accounts at a real estate website frozen, a large amount of fake ads deleted, and informed a few formerly clueless Florida real estate agents about the “Florida Rental Scam”. https://www.google.com/search?q=florida+rental+scam
Shock and surprise that someone would snag their listings from a Multiple Listing Service (MLS) then post it on another site. The MO is “I’m out of town, send me the deposit and first month and I’ll mail you the key.”. *And some people will do it* despite the site having on every listing a warning to NOT send money to a person you have not met face to face at the house or apartment for rent.
I also discovered how gullible a lot of people are. Most of the callers said something in the vein of “I thought it was too good to be true.”. $700 a month for a 3 bedroom, 2 bath house with a pool in Coral Gables, YA THINK?! The scammer later raised the rents to $1000 and on one he just left the price at $3000, apparently hoping to snag someone both rich and stupid.
Sprint saw the forwarding to my cell phone and removed/blocked it but it didn’t work. The telcos have no way to put a general block on *incoming* call forwarding to a phone number. Why. The. Hell. Not?! Adding such a function, and having it be the default for ALL phone numbers, would dramatically reduce a lot of scam activity. Same goes for “slamming” and other crap 3rd parties can do with phone accounts. Most of those *can* be blocked but the default set by the telcos is to allow it all! One must contact your telco and request they specifically block such activity on a phone number.
Took me a while to find out how to “reclaim my number” from the Google Voice forwarding. https://support.google.com/voice/answer/150640?hl=en&ref_topic=1707989
I didn’t have to get a Google Voice account or number, I just used the I want a new number option and did the Call Me Now thing to verify taking my real phone number away from the scammer’s account. If that somehow gave me a GV number I don’t know what it is and wouldn’t use it if I did and I for certain wouldn’t tell anyone my GV number, if I have one.
Once I did that there have been no more calls. Yay!
That still does not excuse Google’s complete lack of any way to report someone using a GV account for criminal activity. If the evidence I supplied to Microsoft was good enough for them to take “appropriate action” on two hotmail accounts, it should be good enough for Google to cancel GV accounts – if Google provided any way to report such activity.
Aside from the early morning calls by a lot of clueless, gullible people, I enjoyed doing battle with the scammer and thwarting him or her on various things. I also found an ad site I didn’t know existed, similar to craigslist. It’s backpage.com Found that because the scammer also posted at least one fake ad on there for a rental in Brooklyn.
Does this comment system have the same vulnerablility since you can use your facebook, twitter or wordpress username and password?
Let’s find out! Your email address please? :)
Seems easy to fix though, surely Slashdot should just send an confirmation email out on signup?
Actually the scenario assumes that the email address is already compromised (if you read they have to use the same one). So you can’t validate using the email address. Instead you need to validate using all that annoying crap (phone typically) that was setup when your email address got switched to use two step validation, you did turn that on right?
Then though, if your email is truly compromised they probably have your two step validation setup to work for their needs to.
The only “real” solution is to create a “validation” link between the two accounts and signal the new linked account to log in as the original /. account (in this example, it could be anything really) to validate the account merge. If they don’t merge the accounts after an expiry period then trash the new account. At all times until it has been merged it should be allowed to do NOTHING.
Few sites would implement that though as most developers are just lazy.
I’ll add to that, lazy or their business department won’t allow them time to properly implement things the right way.
Actually, the email address need not be compromised, that aspect of the vulnerability lies within the social media site in that it would allow the attacker to set up an account without confirming the email address used. The attacker can then use that account they created under somebody else’s email to trick the site they’re tyring to break into think that they are the target user by using the social media’s login button.
If the email account was already compromised the attacker could just request a reset token from the target site and change the password to whatever they want and be done with it.
Really incredible vulnerability
I was just going to write this sounds more like poor implementation on slashdot’s behalf (in the example) for not requesting the password of their current account holder before linking the request with an existing account. I don’t think it’s laziness on the developers part. A lot of them run on deadlines, and they may not think it through 100%.
I agree with twdarkflame ; thats not what I understood from the article. They say that linkeld service allows you to open an account with someone else email? That’s not true you need to confirm a link that is send to that email. so all in all it means you broke the password of someone else email first.. and that is completely a different subject. Once u got someone email passowrd you can do whatever you want as most identification is done though email. So this news is not really interesting.
So… LinkedIn shouldn’t confirm federated logins until the email account is confirmed.
No, relying parties shouldn’t assume that linkedin has verified the email address it provides actually belongs to the user.
This should be caught with a “Not Verified” response.
thats why i tell people;
if its not email and you have to sign up, you wont find me there.
… you miiight find someone pretending to be me, but not me.
so if you think youve found me, pretty please, unfriend and report this “user”.
hopefully the account in question gets banned/deleted
This is ridiculous. Anyone who ever wrote an OAuth client and thought about how to handle the same person logging in using two different OAuth providers has probably thought of this. IBM hardly “discovered” any flaw in OAuth. The flaw they discovered was with SlashDot merging two separate accounts based on nothing but an email address. In their example LinkedIn wasn’t at fault, SlashDot was. Yes, LinkedIn is able to mitigate the problem but the cause was still SlashDot’s poor security.
I will go insane from having to create accounts for every website in existance just to see some stupid little peice of content, mainly because each has different password criteria that confliict…
why cant the world be like hackaday?