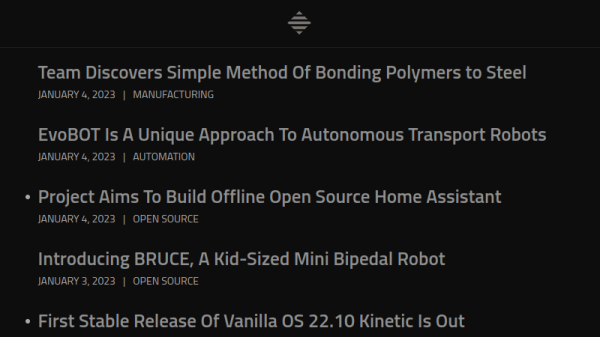
There’s probably some axiom in professional journalism that says you shouldn’t give out free advertisement to your competitors — but since none of us have any formal training in this kind of thing and are just making it up as we go along — we’re more than happy to plug the brand-new MOSFET.net.
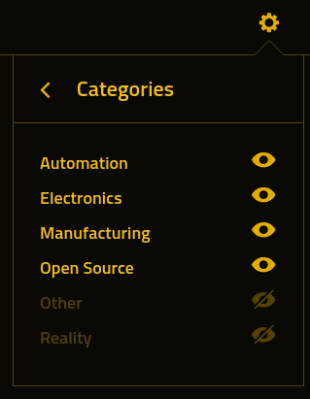
Created by the mysterious hacker [N-O-D-E], the site is exceptionally minimal, providing an experience not entirely unlike a feed reader. Each story has a main image, a few sentences that describe what it’s about, and the ever-important link to the original source. There’s even a color filter applied on the images so they aren’t jarring when compared to the site’s monochrome color scheme. (If that all sounds familiar, it’s because Hackaday came up with the idea 18 years ago. But it’s cool, we’re not salty or anything.)
In all seriousness, the site looks very well done and will no doubt be a great resource for the community. A particularly interesting feature is that entries expire automatically after 30 days. This speaks to the goal [N-O-D-E] has for MOSFET.net — it’s designed to show you relevant tech news, and literally nothing else. The focus and simplicity is beautiful.
Here’s wishing all the luck to [N-O-D-E] in this new venture. We know better than most that it can be a difficult and sometimes thankless job, but we wouldn’t still be doing it all these years if it wasn’t worth the effort. The tech world is always growing and there’s plenty of room for everyone. In fact, a recent peek at the analytics revealed that Hackaday got more views in 2022 than at any time in its history. As far as we’re concerned, the future looks bright for everyone.